Alert – Fake Invitations to View a Google Doc – 05/03/17
There are two new phishing emails that are making the rounds with fake invitations to view Google Docs. They are both very clever and they are both sent from someone that is in your contact list. The first one is a bit easier to spot as it looks something like this:
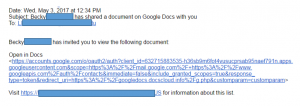
For those of you who have received an Invitation to View a Google Doc before, it is easy to pick up what is amiss with this email. However for those of you who haven’t, this is what a legitimate Invitation to View a Google Doc looks like. When you click the Open in Docs button, the document is opened for you.
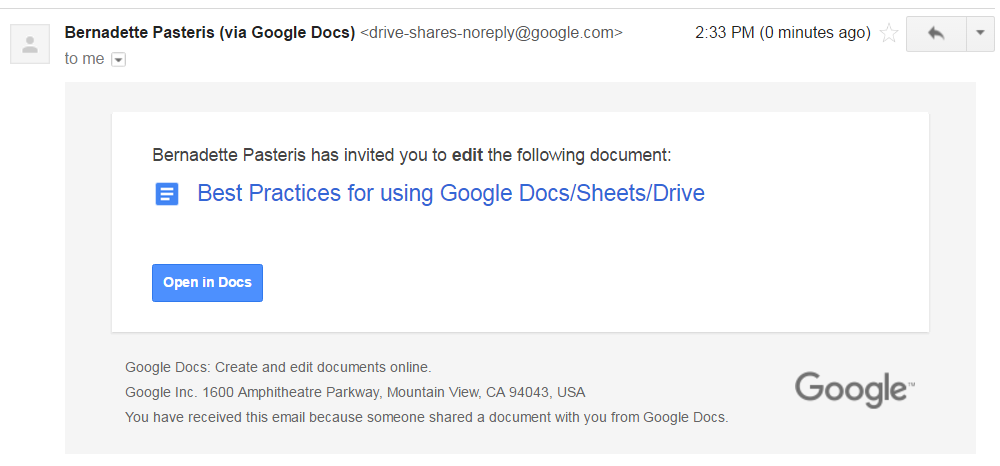
The second phishing email is more sophisticated in that it looks a lot like a legitimate Invitation to View a Google Doc. The only thing missing from the email is the name of the document. However if you click on the Open in Docs button instead of viewing the document, a dialog box appears asking you for permission to access your email. This is the tip off that something is awry. Google Docs does not need access to your email to function.
If you see a dialog box instead of a document when you click the Open in Docs button, DO NOT CLICK on anything. Disconnect your computer from the Internet and call the IT Service Desk. If you want to learn more about this phishing campaign, check out the CBC article.
As these latest phishing campaigns show, criminals are getting more and more sophisticated in the development of their phishing emails. It is getting harder and harder to determine what is a legitimate email and what is a scam. To avoid becoming a victim of cyber crime, verify the legitimacy of all unexpected emails containing links or attachments regardless of who they come from.
McAfee Logo Has Changed – 05/02/17

Just a heads up for staff and faculty. If you take a look at your task bar in Windows and see a new icon, don’t worry it’s just McAfee’s updated logo. McAfee is the antivirus software that is loaded onto all Mount Royal workstations. Don’t have the new logo yet? Don’t worry the logo is updated in stages, it will eventually be your turn. If you have any questions or concerns, contact the ITS Service Desk.
New phishing email targeting the Mount Royal community – 04/07/2017
A new phishing email is making the rounds at Mount Royal. The cyber criminals use an official sounding name and reference a fund transfer to entice people to open a password protected Word document.

As a password protected document adds a sense of legitimacy to a phishing email, ITS has decided to block all incoming emails that have password protected Office documents as attachments. If you have a legitimate need to receive a password protected Office document, please contact the ITS Service Desk.
New login screen for Google a privacy concern – 04/07/2017
On April 10, 2017 Google will start rolling out a new login screen. It will begin with limited release and then widen until all users are converted over. The new screen will no longer give you the option to Stay signed in. Instead all users will automatically be connected to Google/Gmail/Google Drive with this feature enabled.
Why is this a concern? Well, if you are using a public workstation in the library, a classroom or meeting room and you log out of the workstation you will not be logged out of Google/Gmail/Google Drive. The next user who starts up that workstation and opens Google Chrome will see all of your emails and files on display.
Starting today, we are asking that all faculty, staff and students logout of Google/Gmail/Google Drive before they logout of any computer or device that is not their own.
If you have any questions or concerns, please contact the ITS Service Desk.
Airline email scam catching 90% of users – 04/07/2017
A group of cyber criminals are having a lot of success with the latest spear phishing campaign. They are mining social media for information on where and when you may be traveling. Using this information they send out fake airline reservation confirmations or receipts that look just like the real thing using an email address that looks legit.
Many of these emails contain links to sites that look like the real thing, asking you to enter your username and password and encouraging you to open an attachment or click on a link that loads malware. The loaded malware allows the criminals to hack into the network.
These criminals are clever enough to vary the format of the email and the delivery method for the malware, making it more difficult to detect.
If you receive a confirmation for a flight or a receipt, do not click on any links or open any attachments. Instead, go to the website of the airline directly using a URL that you know is legit and check your account or reservation on the site itself.
If you do click on one of these links or open one of these attachments, please disconnect from the network and call the Service Desk at 403-440-6000 immediately.
Ransomware Alert – Do not install a Chrome font pack! – 02/02/17
There is a new ransomware scam. So new that antivirus software isn’t aware of it yet and therefore can’t detect it. Chrome for windows users that visit compromised websites are suddenly finding the text on the page becomes unreadable. An alert appears explaining that their browser doesn’t have the font needed to display the page properly and instructs them to install a font pack. To add to the fun, they are unable to close the alert using the “x” button and they cannot close the browser. If you choose to download and install the so called font pack, you are able to read the text but ransomware is also being installed in the background. The nasty thing is so sneaky, you don’t even notice that something is awry…at least not at first.
Your first clue is your computer starts to run rather slowly. Then you see folders on your desktop grey out and you can’t open them. As the encryption starts to spread you loose access to your documents one by one. Then the lovely ransom note appears. However by this time you no longer have access to any of your files.
If you find your folders are greying out or you are unable to open files, please disconnect from the network immediately and call the Service Desk.
This latest ransomware uses a common tactic for delivering malware, the fake alert window. If an alert of any type pops up when you visit a webpage, encouraging you to install something to fix the problem, close the browser immediately. Do not click on anything in the alert window including the “x” as some diabolical hackers design their malware to install regardless of where you click. If you are unable to close the browser, reboot your machine. By following this simple no click rule, you will save yourself a whole lot of frustration and heartache.
Alert – Mount Royal Targeted by Phishing Emails – 01/19/17
Members of the Mount Royal community are receiving emails that look an awful lot like they come from the ITS Service Desk. Problem is, they aren’t. The clever criminals are even shameless enough to hide their malicious link in an email that looks like it is trying to prevent cyber crime. Here is what to look for:
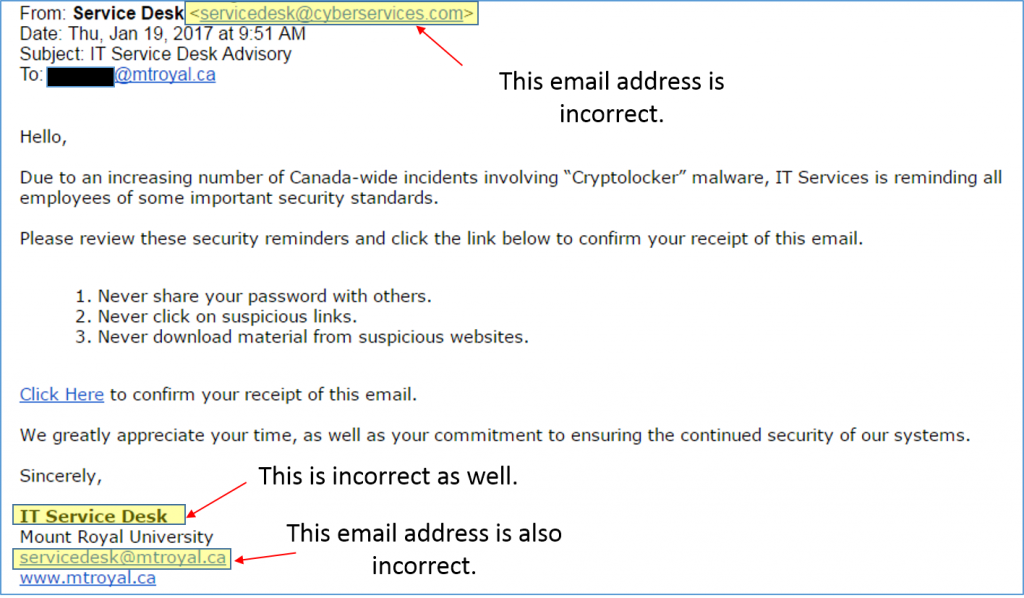 Of course if you click on the link, some nice nasty malware gets loaded onto your system. If this email shows up in your inbox, do not click on any of the links and delete it immediately.
Of course if you click on the link, some nice nasty malware gets loaded onto your system. If this email shows up in your inbox, do not click on any of the links and delete it immediately.
The criminals are getting smarter and smarter and are starting to make fewer and fewer mistakes. Remember, before you click on a link in an email, or open an email attachment contact the sender and verify that the email is legitimate.
Phishing Scam Alert: OneClass Chrome Extension – 12/12/16

As mentioned in a previous post, you should only download apps, browser extensions and the like from reputable sources. The latest alert is for the OneClass Chrome Extension. It is a phishing scam that will attempt to send an email to everyone in your Blackboard courses and steal your usernames and passwords. Several Mount Royal students have already been affected by this scam.
How the phishing scam works:
- Students receive an email with a link to install the OneClass Chrome Extension.
- During the installation, the user will be prompted to accept its permission of “Read and change all your data on the websites you visit.”
- When the user accepts, a button will be created within Blackboard pages to “Invite your Classmates to OneClass”.
- The extension attempts to email everyone in the user’s Blackboard classes to promote the OneClass extension.
- The extension also attempts to collect user credentials (usernames and passwords).
If you receive the following phishing email, do not install the extension or click on any links on the email. Please delete the email.
“Hey guys, I just found some really helpful notes for the upcoming exams for <University Name> courses at <URL removed>. I highly recommend signing up for an account now that way your first download is free!”
If you have installed the OneClass Chrome extension, you should immediately remove it and change the password of any site you logged into while it was installed.
To remove the extension:
- Open your Chrome Browser.
- Select the 3 vertical dots in the upper right-hand corner. A menu appears.
- Select Settings. The settings page appears.
- From the menu on the left, select Extensions.
- Scroll down until you locate the OneClass Easy Invite extension.
- Select the Trashcan icon beside the “OneClass Easy Invite” extension. A dialog box appears.
- Select Remove.
- Close all Chrome windows and return to the Extensions page to verify the extension has been removed.
Remember to use the link on the MyMRU log in page to change your password, and to change your password on any other sites you used while the extension was installed.
Any students who need assistance can contact START http://www.mtroyal.ca/AboutMountRoyal/TeachingLearning/AcademicDevelopmentCentre/START/index.htm and any staff who need assistance can contact the Service Desk at 6000.
Dailymotion Accounts Hacked – 12/07/16
Around the 20th of October, 85 million usernames and emails were taken from Dailymotion servers along with 18 million hashed passwords. For those of you who don’t use Dailymotion, it is popular video sharing website. Because the passwords were encrypted, it will take some time for the cyber criminals to crack them. This gives users time to change their passwords on their Dailymotion account as well as change the password for any other accounts using the same password.
Once again this drives home the importance of having a different password for each account. It is not a matter of if one of your accounts will get hacked, it is a matter of when. Limit the damage…use unique passwords.
Alert – Phishing Email Targeting the Mount Royal Community – 11/24/16
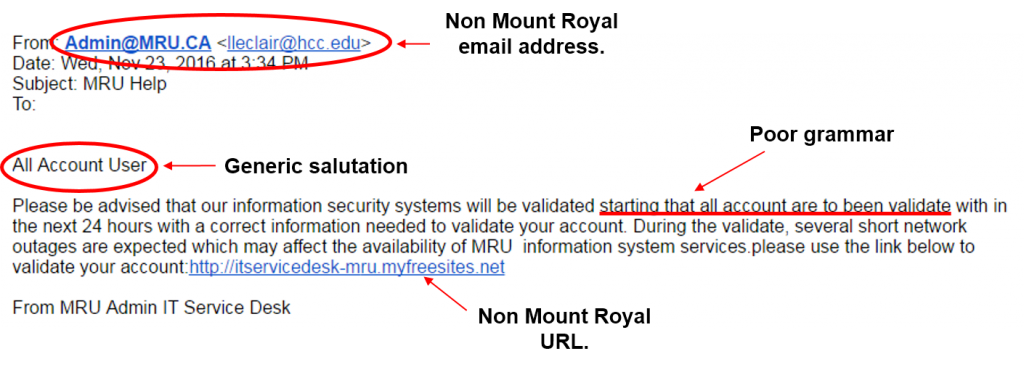
Here is the latest phishing email pretending to come from the IT Service Desk. How do you know it is a fake? It contains an email address that is not found on the Mount Royal network and it uses poor grammar. Other things that are suspicious but not clear giveaways are, it is addressed to account user instead of a person and the link takes you outside of the Mount Royal website.
If the following email shows up in your inbox, please do not click on any of the links or reply to the email. Please delete it immediately.
Looking for a handy desk reference to print off and refer to when trying to determine if an email is legitimate? Print out this one created by KnowBe4.
