Which email address to use when – 09/15/20
Who would have thought that 2020 would have everyone who can, working and taking classes from home? In a few short weeks we had to find a workspace, navigate chaos at home and learn a whole new set of skills. In the shuffle, it is easy to have work/school seep into our home life and vice versa. While it is normal to have this happen occasionally, as a general rule you should make sure you are using your email accounts appropriately. Here are a couple of tips that will help you sort through the work/school/home mess.
Use your MRU email only for work/school purposes
While this was a good idea before the pandemic, it is even more important now. Criminals know our home networks don’t have all the security bells and whistles that are on our corporate networks. Attacks are on the rise as they look for vulnerabilities. One of those is using your MRU email for personal purposes.
The more places you use your MRU email address the greater the chances you are going to reuse passwords and expose yourself to credential stuffing. As we are notified when your MRU email address has been used for a login credential of a breached account provider, we sometimes find out more about your personal life than we would like. Save us both the risk and embarrassment. If an account is for personal use, use your personal email address for your username.
Don’t use your personal email address for work/school
Since we have begun working at home, it feels like I have responded to 55.1 requests to view Google documents. The requests have come for quick reference guides, user manuals, registration forms, you name it. Every time I have had to reply with…
This document is only viewable by those with a Mount Royal email address. Please login to your Mount Royal email to access the document.
It gets mighty tiresome. I don’t know who the requester is unless they use their Mount Royal email address. For that reason, I do not grant non MRU email addresses access to documents. Everyone on campus should be following this protocol.
As important as it is to use your work email address to access documents, it is even more important for attending Google Meetings. Don’t make your meeting host guess who you are or whether you should be attending. Make it clear you are supposed to be participating by using your Mount Royal email address.
When you must use your MRU email address
To access some accounts, you must use your Mount Royal email address as a username. In these instances it is especially important to use a unique password. It prevents criminals from gaining access to your email by using a password that they have stolen from another account provider.
By following these simple rules you will decrease your vulnerability to cyberattacks, protect your privacy and make your colleagues, instructors and students lives easier. Happy days for everyone!
Don’t take candy from strangers – 09/16/20
All malware is not created equal. This week a particularly devious piece landed in an MRU inbox. It was wrapped up in a zip file attachment. Here is what the malicious email looked like:
This malicious email is hard to identify as it contains a previously sent email thread. Interestingly enough, there is no human behind this email. It was sent by malware. When it gets on your machine it picks an email in your inbox and replies to it. Sending a copy of itself to an unsuspecting recipient.
The email is generic enough to work with pretty much any email. However it is the vagueness that flags it as suspicious. The other tell is the sender’s email address. Because this is malware and not a person sending out the email, the sender’s email address is incorrect.
If you decide to click and open the attachment, you see an Excel spreadsheet with this in the first cell.

If you missed the other two red flags, this one is your last chance to dodge the bullet. This very official looking graphic is asking you to enable editing and content to be able to “decrypt” the document It is also telling you what type of device to use to view it. Anytime you have this kind of instruction given to you to view a document, close it immediately and report it.
The instructions are not there to enable you to view the document. They are there to ensure the malware can be installed and will function. By asking you to enable editing and content, it is bypassing the safety controls we have in place to prevent the running of macros. It is not “decrypting” anything. If you can’t open a document just by clicking on it, consider it a threat.
This is another reminder how important it is to check the sender’s email address before you open an attachment or click on a link. If you recognize it, contact the sender using another method and confirm that they sent the email. If you don’t recognize it, don’t click. You wouldn’t take candy from a stranger, you shouldn’t take attachments from them either; no matter how enticing they are.
The PhishAlarm button, the best way to report suspicious emails – 09/23/2022

Updated from 05/26/2022
The PhishAlarm button is the quickest and easiest way to report suspicious emails you find in your Mount Royal inbox. However, you have to be using Gmail as your email client to have access to it. In addition, if you aren’t an employee you will see the button but will get an error message if you try to use it.

If you are using Outlook or some other application to view your emails or you aren’t an employee, forward suspicious emails to cybersecurity@mtroyal.ca.
Please don’t forward phishing emails to abuse@mtroyal.ca We can receive 114 phishing reports in a single day and it takes time to filter through them. While we won’t be ignoring emails sent to abuse@mtroyal.ca, forwarding them to cybersecurity@mtroyal.ca will ensure they are identified and responded to in a more timely manner.
To report a malicious email using the PhishAlarm button
- Open the email
- Click the PhishAlarm button in the side panel. If you don’t see your side panel, click the arrow in the bottom right hand of your screen.
- Click Report Phish. A confirmation pane appears.
- Click the X to close the confirmation pane.

Not only is the PhishAlarm button super easy to use, it sends the cybersecurity team more information about the email making it easier to investigate. It’s a win for everyone!
On a final note, the PhishAlarm button is designed to notify us of unknown malicious emails. As a result, you are unable to report emails that are in your spam folder or those that have already been marked by Google as suspicious. This saves the security team time as Google has already taken measures to ensure everyone is aware the emails are malicious so we don’t have to waste resources investigating them. Those messages don’t need to be reported and can simply be deleted.
Hackers use fake Cisco WebEx vulnerability to lure victims – 05/21/20
Criminals are sending phishing emails that look surprisingly legitimate. They appear to come from apparently trustworthy senders, like “cisco@webex[.]com” and “meetings@webex[.]com.” They emails urge recipients to take an immediate action in order to fix a security vulnerability in their WebEx software. The emails look like this:

If you click on the Join button, it will take you to a page that asks for your login credentials. Of course the login page belongs to the criminals and will only steal your credentials.
If you receive an email asking you to update software, do not click the links in the email. Instead, start up the software and check for updates by selecting Help from its menu and selecting About. You can also visit the official website for the software and load updates from there.
Criminals are creating look-a-like MRU webpages – 04/23/20
We have been notified that cybercriminals have registered and are using the domain www.mroyalu.ca as well as several other look-a-like domains. They are attempting to fool people into visiting their malicious websites.
While working from home, it is very important that you double check all links that you receive in emails and the sender’s email address.
If the link does not have mtroyal.ca, mru.ca, mrucougars.com or mymru.ca before the first single / in the URL, it is malicious.
Examples of legitimate URLs are:
mru.ca/cybersecurity
mru.ca/wellness
https://www.mtroyal.ca/AboutMountRoyal/WhyMRU/
https://www.mymru.ca/web/home-community
Examples of fraudulent URLs are:
https://www.mroyalu.ca/AboutMountRoyal/WhyMRU/
https://www.mymur.ca/web/home-community
https://www.my.mtroyal.ca/Home
Please do not let curiosity get the better of you, and attempt to visit any of these fraudulent websites. They will harm your machine and/or steal your data.
If the sender’s email address ends in anything other than @mtroyal.ca, then it is malicious.
Examples of legitimate email addresses are:
bpasteris@mtroyal.ca
cybersecurity@mtroyal.ca
Examples of fraudulent email addresses are:
bpasteris.mtroyal.ca@gmail.com
bpasteris@mroyalu.ca
bpasteris@mtroyal.email.ca
Please be extra cautious at this time.
Updated 04/27/20
Big yellow banner bad, sometimes – 04/15/20
Have you every opened an email and seen this?
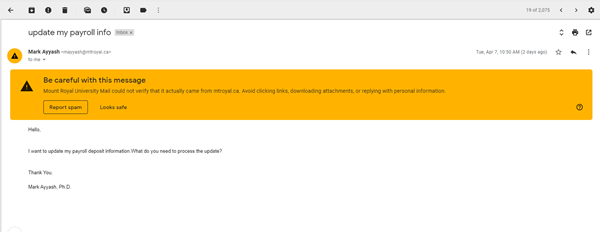
This big yellow banner is a warning that Google has identified the email as coming from outside the Mount Royal network even though it has a Mount Royal email address. This happens when someone on campus is using a cloud based tool to send out communication emails or when someone is pretending to be a Mount Royal student or employee.
We whitelist the cloud based tools used on campus to avoid getting this error on legitimate emails. However, the developers of these tools like to change things once in a while without notice. If we aren’t able to adjust the whitelist in time, this banner will show up even if it isn’t malicious.
What do you do if this warning shows up on in email? Stop and take a closer look at the email. If you have seen the exact notification or newsletter before, then it is probably a whitelisting issue. If it is from a person, then it is probably malicious. Not sure, click the PhishAlarm button or forward it to cybersecurity@mtroyal.ca.
Updated 05/29/20
If you don’t report, we don’t know – 03/17/20
With the world on melt down, cyberattackers took advantage of the mayhem to send out a slew of spear phishing emails to several departments. Most of them had a member who reported the suspicious email right away. As a result, we were able to notify their colleagues before most of them had even opened it.
Unfortunately, one department was left vulnerable. None of their members reported the malicious email sent to them. We eventually found it, but we it was much later and there was a delay in the notification going out. This delay increased the chances that someone would become a cyberattack victim.
We know that all of you have much on your mind trying to figure out how to teach and work from home. However during this challenging time, please don’t forget to take those extra two seconds to let us know when something suspicious lands in your inbox. The sooner we know, the sooner we can let everyone else know and reduce the risks to everyone’s data, including yours.
What do you do with those invites from Alignable? – 02/14/20
Across campus an email similar to the following has been popping up in inboxes.

According to their website, Alignable is
…the online network where small business owners across North America drive leads and prospects, generate referrals, land new business, build trusted relationships, and share great advice.
Their website is slick and professional. It has an impressive lists of testimonials. In addition logos of media outlets are prominently displayed. Everything on the site is designed to make the service look like it is widely used and trusted.
While there is no doubt that this a legitimate service, their marketing practices appear to be a bit troubling. Those reporting the Alignable emails to the cybersecurity team often remark that they do not know the person who sent the invite. Others complain that they did not sign up for the service but yet everyone in their contact list has been spammed.
These complaints are not just coming from our community. The Better Business Bureau has 19 similar complaints. While Trustpilot gives it a 51% excellence rating and a 40% bad rating with very little in between. When you see ratings on the extreme ends of the spectrum like that, that usually indicates that a bot is posting the good reviews.
Scouring the rest of the internet, influencers indicate that it is an amazing tool that you should try while other folks warn to stay away unless you want to spam your contacts. It is difficult to know what the real story is.
What I can tell you is unhappy users have experienced the following:
- They have been signed up for the service when they click the cancel button on the would-you-like-to-join dialog box.
- They have had their entire contact list spammed with invites without their permission.
- They have had invites sent out on their behalf without ever joining the service.
It is not possible to say whether these actions are deliberate or Alignable has a glitch in its service. Either way I suggest that before you accept one of their invitations, you treat the email like any other coming into your inbox and contact the person who sent it to you to make sure it is legitimate. While you are at it, you should ask them about their experiences with the platform. If they give you green lights, then you are good to go. If not, delete the email.
What have your experiences been with Alignable? I would love to hear about them. Please post your comments below.
Email from The Spamhaus Project is fake – 01/31/20
The latest phishing email to arrive in MRU inboxes is this beauty that looks like it comes from The Spamhaus Project, an international organization that creates block lists of spammy and phishy email senders.

This email is a bit clever as they use a link to the real Spamhaus Project website to try and convince you the email is legitimate while threatening to block your email address. Unfortunately the painfully bad grammar, zip file attachment and wrong email address clearly mark it as a phishing attempt.
You have to give them credit for trying though, if you are in a hurry and don’t take the time to read the email carefully, the odds are pretty good you will panic and click. Don’t get caught, slow down and stop and think before you click.
Mount Royal University’s email policy clarified – 01/31/20
Updated: 02/07/20
In the When to use your @mtroyal.ca email address article, I outlined some general guidelines on how to determine which email address you should use for creating accounts and accessing online services. This article generated a slew of questions related to availability of email accounts once someone leaves the University. I thought it would be helpful to clarify who gets to keep their accounts, under which circumstances and why.
Our email policy states
The University provides an email account to all faculty, staff and students to be used in the course of their duties or activities at the University. The University may also provide an email account for alumni, retirees, and professor emeriti, as well as other at the discretion of the University.
All email accounts and associated addresses are the property of the University.
So what does this actually mean and how is this policy implemented? Well that depends on who you are and under what circumstances you leave the University.
- If you are a staff member your access to your email will be terminated regardless of why you leave. This is to ensure business continuity.
- If you are a faculty member the same rule applies unless you are leaving due to retirement. Retired faculty members get to keep their emails as long as they adhere to the email policy. This is part of their collective agreement.
- Students retain permanent access to their email account.
Regardless of who you are and why you left, the University owns the email account and at any time they can revoke your access. The most common reason is not following the email policy. However it is at the discretion of the University to revoke it for any reason that they deem credible. Some of those reasons may be a change in policy or a change in email provider.
Therefore you should never consider your @mtroyal.ca email account to be yours for life. It is yours until the University decides it is not. That is why I suggested all MRU account holders follow the guidelines outlined in the When to use your @mtroyal.ca email address article. The guidelines ensures that you maintain access to your accounts even if your access to your @mtroyal.ca email address is lost.
Another thing to consider is FOIP requests. According to the email policy, any email sent with your @mtroyal.ca account is subject to a FOIP request regardless of whether the content of the email is personal in nature or not. If you don’t want your personal emails to show up in a FOIP request, don’t use your @mtroyal.ca account to send them.
If you have any questions about email access or the email policy please contact the Service Desk, they will be happy to help.
