If it seems to good to be true, it is. 03/20/19
Everyone likes a good deal. So when one of our analysts found a 2014 Jeep Wrangler Rubicon with less than 50000 km on Autotrader for $11500, his heart skipped a beat. This vehicle was loaded with aftermarket goodies and usually goes for four times the price. Check her out, she is a beauty!!

He hoped with all his heart, that this was the real deal. However with the price being so low, his scam detector was running at full power. He contacted the seller and discovered that the vehicle belonged to her father who has just passed away. She knew nothing about jeeps and just wanted to get rid of it. Hmmm, that sounded plausible. He investigated further.
The seller informed him that if he wanted to purchase the jeep he would have to do it through WTC, otherwise known as Wiozacars Trading Corporation. Our analyst did some research and found that it was an escrow company with tons of good reviews from various sources going back several years. Oddly enough, there wasn’t one link in the three pages of search results to the company’s website. Maybe it didn’t have one. This might be legit after all.
Our analyst informed the seller that he was interested but didn’t know anything about WTC and asked for more information. The seller sent him detailed instructions on how to complete the transaction along with a link to the WTC website. That is when things started to fall apart. If the company had a website, why didn’t a Google search find it? He clicked the link the seller provided and found a very beautiful and professional looking fully functional website.
He decided to call their bluff and asked if his wife could look at the vehicle. Never mind that he was in Calgary and the vehicle was in Quebec. By now he was certain it was a scam, however he wanted to see what the sellers would do. Sure enough, after his request all communication stopped and the ad was removed from Autotrader. Scam confirmed.
No matter how badly you want to believe that once in a lifetime deal is the real thing, take the time to do your research. If their website doesn’t come up in a Google search or they are asking to use an unknown third party to do the transaction, walk away.
Brazen phishing email asks for passport information – 12/17/18
This week a new phishing email is popping up in Mount Royal inboxes. The cheeky criminals are coming right out and asking for passport details as well as other personal information. They don’t even bother with links or fancy look a like web pages. They just ask for your information so they can send you money. The email looks like this:

Because this is a low tech scam, people tend to let their guard down and be more receptive to getting hooked. The scammers count on this and hope the victim gets excited enough about the possibility of getting free money to give up their personal information. Once they have it, they can use to to steal their identity and wreak havoc on their life.
This is definitely a case of, if it seems too good to be true then it probably is. No bank will email you out of the blue to ask you for passport information. If you refuse to accept reality and want to cling onto hope, then contact the bank directly to ask them if they are trying to transfer you some money. Don’t ever send personal information like passport, driver’s license or credit card information in an email.
Cyber criminals try bomb threats, fail and turn to threats of acid attacks – 12/14/18
Last week inboxes across North America received phishing emails that threatened to blow up their place of business if they did not immediately pay $20 000 in bitcoin. The good news is there was no bomb. The bad news is not everyone understood that.
Police departments across the continent were flooded with calls from panicked citizens reporting the bomb threats. The bomb threats were so disruptive that police forces in the US and Canada issued reports and held press conferences assuring citizens that the threats were part of a phishing scam.
Unfortunately for the criminals, no one is paying the extortion fee. So while they get an A for getting everyone’s attention, they get an F for not making any money.
Having bombed with their bomb scare (sorry, I couldn’t resist), this week the criminals are threatening an acid attack if they aren’t paid. Apparently they are trying to repeat the success of their sextortion scam which netted them $146 380 in three days. So if you receive an email in broken English threatening to throw acid in your face if you don’t pay up, delete it.
Must Read – They’re back and this time they’re impersonating David Docherty – 12/12/18
The MRU impersonators are at it again. Apparently they didn’t get bites just pretending to be a supervisor so they have upped their game. Their third attempt uses an email that appears to come from Dr. Docherty himself.

As with the other attempts, if you respond to this email you are asked to purchase gift cards. This is just another reminder to check the sender’s email address when you find yourself responding emotionally to an email.
Must Read – MRU impersonators are back – 11/16/18
A few weeks back I warned the Mount Royal Community that emails were making the rounds that appeared to be from Mount Royal Employees. Typically the impersonated employees were supervisors of some sort and the emails were sent to their reports. The criminals were taking advantage or our natural tendency pay attention and take action when we are contacted by our supervisor.
Unfortunately the scam is back. Thankfully abuse@mtroyal.ca has been flooded with reports and no one has yet taken the bait. However just to be on the safe side, I thought I would give everyone a friendly reminder to check the sender’s email address before responding to an email.
Scammers sending emails that look like they came from your account – 10/24/18
There is a new twist on the you have been naughty scam. Criminals are sending emails that once again claim that they have evidence that you have been visiting porn sites and if you don’t pay them, they will make that information public.
The newest form of the scam claims that they have installed a RAT (remote access Trojan) on your computer that allows them to send the evidence from your device. To drive home the point, the email looks like it has come from your email account.
The good news is, it is all a big bluff. They don’t have access to your email, they are only spoofing the email address. Your account is secure. Your reputation is intact and you can peacefully delete the email.
Scammers using voicemail to steal WhatsApp accounts – 10/17/18

Armed with nothing more than your phone number, criminals can steal your WhatsApp account. How? By registering your phone number on their phone. Here is how it works.
First the attacker makes a request to have your phone number registered to the WhatsApp application on their phone. When WhatsApp receives the request, they text a verification code to your phone. The scammers make their request in the middle of the night or when you are on a flight so you don’t see the verification code. With the text not answered, WhatsApp offers to read out the code and leave it in a voicemail.
If your cell phone carrier has a default password set up for voicemail and you have not changed it, the criminal simply enters the default password and boom…they can hear the verification code. Once they enter that code, the account gets transferred over to their phone. The attacker then sets up two step verification on the account and you have no way of getting it back.
The moral of the story, set strong and unique password for your voicemail. While you are at it, do that with all your accounts.
Fake sites use HTTPS too – 10/04/18
As the holiday season approaches, people around the world are getting ready to cruise the internet looking for great gifts at bargain prices. As you do your online holiday shopping, keep in mind that sites labeled HTTPS guarantee your data is encrypted as it is transmitted between your computer and the web. It does not guarantee that the site is legitimate.
Criminals have gotten wise. They are now registering their fake web sites so they are tagged as HTTPS. So now instead of having to worry about your credit card information being intercepted as you purchase the iPhone XS Max for the unbelievable price of $300.00 USD, you can be confident that only the scammer is receiving your data.
So how do you know that a site is legitimate? Stick with retailers that you have used in the past and access their web sites using a bookmark or search result. If you receive an email with an offer, don’t use the link in the email. Visit the website directly.
If you are using a new retailer:
- Check reviews first. Avoid retailers with large numbers of complaints that haven’t been resolved.
- Always pay with a credit card or PayPal so you have a method of recourse should things go wrong.
- Remember to read all the terms & conditions of sale. Know if they have a return or exchange policy.
Lastly, remember…if it is too good to be true, it probably is a scam.
Hurricane Florence Relief Scams – 09/27/18
It is a sad reality, but when there is a disaster it doesn’t take long for criminals to find a way to profit. Hurricane Florence is no exception. There are numerous websites for hurricane Florence relief that have popped up in the last week. All have very professional looking graphics and legitimate sounding names. All of them allow you to donate directly from their web site. However, many of them are simply collecting money and putting it into their own pockets.
In addition to the “charity” websites, the bad guys are sending out phishing emails tugging at your heart strings and asking you to donate to hurricane Florence relief. Just as you would with any other unsolicited email, don’t click on links or open attachments in these emails. If you wish to donate, visit a charity’s website directly.
Not sure where to donate? Make sure you do your homework first. Charity Navigator is a terrific organization which investigates and rates charities. They have hundreds of charities listed on their website. You can see if the charity is legitimate and how much of their raised funds are given away and how much are used for administrative costs. With a little research you can make sure your good deed doesn’t turn into it’s own disaster. Happy donating!!
Must Read – Scammers pretending to be Mount Royal employees – 09/27/18
It has been a busy week. There are two phishing emails going around campus at the moment. The first one starts out rather innocently.
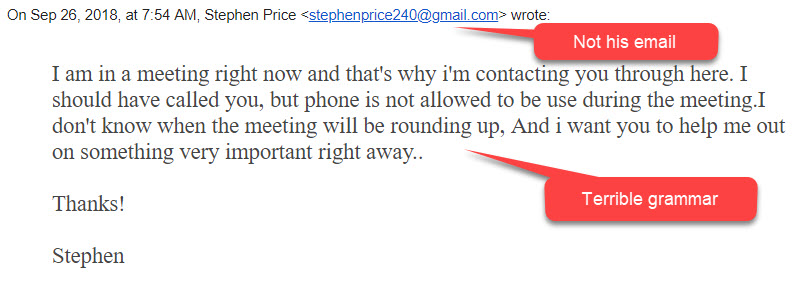
However if you respond to it, like half a dozen people did, you receive a second one.
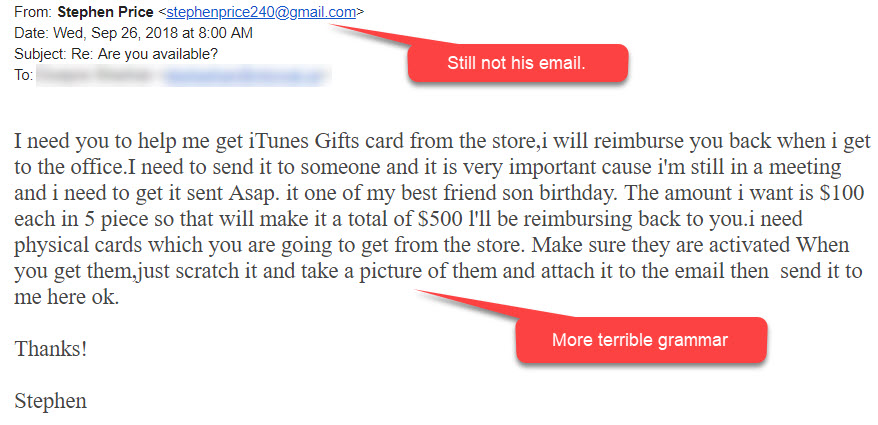
You are probably wondering why anyone would respond to the first email. First of all the email was from a department head, so that tends to get people’s attention and generate an emotional response. Also, almost all who responded were looking at the email message on their phone. They were unable to clearly see the sender’s email address or the grammar errors. This is just another reminder as to why it is so important to wait until you get to a large screen to take action on an email. It is also a reminder to not respond to our emotions. If you read an email and are responding emotionally to it, that is your cue to pause for a minute and take a closer look.
Impersonator number two is a bit more sneaky. Check out this bad boy.

I just love how they added the signature line to this one. They must have received an email from Mount Royal at some point. This is the stuff that keeps me up at night. The grammar is perfect. The content is plausible and looks legitimate. The fuzzy logo is a bit of a tell, but other than that it’s not an easy one to spot.
That was the bad news. Now for the good news. In both cases IT services was notified of the threat by Mount Royal University employees who forwarded the email to abuse@mtroyal.ca. Their quick thinking gave us a heads up right away so we could block both email addresses and prevent further attacks. They are superheros!!
Keep an eye out for these types of emails in the future. If you find one, forward it in its entirety (no screenshots please) to abuse@mtroyal.ca and you can be a superhero to!!
