Another Canadian university targeted by MacEwan-like scam – 06/26/19
Last week was a rather exciting week for a Canadian university as a scammer tried to convince the university’s finance department to deposit money into their account. The scammers were thwarted by a Finance clerk who followed procedure. Yes, the superhero in this story is boring, annoying old procedure. Here is how it went down.
The university was building a new student centre. So when a Finance clerk received a request for a direct deposit form that looked like it came from the construction company working on the project, they thought nothing of it. They replied to the email request with the form and instructed the company to complete it and forward it to the Finance VP’s admin assistant, as per procedure.
When the admin reviewed the form, everything looked fine at first glance. However when she called the construction company to confirm that they had sent the request, as per procedure, they learned that they had not.
Realizing that they were being targeted by a scammer. The University staff looked closer at both the emails and the completed form. They discovered two things. First the beginning of the email address was correct, but the word “group” had been added to the end of it. Second the name of the site manager on the form was correct but the signature on the form was clearly forged. Both of these red flags had been missed. However, because both the admin and the clerk had followed procedure, disaster was adverted.
Unfortunately the City of Burlington in Ontario wasn’t so lucky. It isn’t know if procedures weren’t followed or if they weren’t in place. However, when they were targeted with a similar change-to-payment scam, they lost $503, 000 to the scammers.
This is a reminder that procedures are in place to help, not hinder. We are all human. We make mistakes. However, following procedure helps us do our jobs successfully and keeps us out of trouble. Regardless of which department you are in, follow your teams procedures. They are there to help.
New email scam impersonates MRFA president – 06/26/19
The following email showed up in MRU inboxes this week.

There are two things that make this email so convincing. First Melanie’s email address is, in fact, correct. No, her email wasn’t compromised. It was spoofed. Second, they name a colleague as the person who will reimburse you. A nice touch actually. With such a convincing email, how the heck are you supposed to know this is a scam? Well, there are a few tells.
First off, the grammar is rather crappy. Not what you would expect from the president of the MRFA. Second, if you try calling Melanie to confirm she sent the email, you get a phone message saying the MRFA office is closed and she isn’t returning messages. If the office is closed, why would she be sending money to vendors? Third there is a sense of urgency. The email says the money needs to be transferred today. Lastly, she is asking you to take money from your personal account. That is a HUGE red flag. Why on earth would she ask you to take money from your personal account to pay a vendor? Nothing makes sense in this email except the email address and name dropping.
The best way to protect yourself from this type of a scam, is to go slow and question everything. If something doesn’t add up, call the email sender to confirm that they sent the message. If you aren’t sure you can forward the message to abuse@mtroyal.ca and we will take a look at it for you.
That is just what Megan did. Thanks to her quick actions, we were able to track down those who received this message, notify them it was a scam and stop the attack in its tracks. Way to go Megan, you are a superhero!! Be a superhero like Megan, report malicious emails to abuse@mtroyal.ca and help protect your colleagues from scammers and hackers.
For Megans efforts, she will be receiving a commitment sticker. Want your own sticker? Report an malicious email to abuse@mtroyal.ca or come down to see me on Main Street on August 20th from 10:00 am to 2:00 pm. Pick up your sticker and spin the prize wheel to win cool swag.

Reply to emails cautiously – 05/22/19
Since September, the Mount Royal community has been targeted by a gift card scam. With this scam, criminals send you an email that looks like it comes from your supervisor asking you if you are available. If you respond, they ask you to purchase gift cards and send them photos of the redemption codes. This past weekend another 300 or so Mount Royal inboxes received one of these scam emails.
Fortunately, we had more people reporting them than we had people responding to them. Some of those that did respond sent out personal information such as where they were located, photos and their plans for the weekend. To our knowledge, no one went as far as purchasing gift cards. We are thankful for that.
Realizing that you gave scammers personal information about yourself just feels creepy. It is also dangerous. The criminals can then take that information and use it as content in malicious emails that are sent to yourself or others. This makes the emails seem legitimate increasing the likely hood that someone will be tricked.
In addition to being dangerous, conversing with the scammers encourages them to continue targeting Mount Royal. If they get a response to an email, they know it is only a matter of time before they convince someone to follow through and purchase those gift cards. Ignoring their inquiries will not stop the attempts, but it will reduce their frequency.
The best way to defend yourself from giving out personal information to criminals is to check the sender’s email address before you read the body of the email. That way you have a better idea of who you are talking to before you respond. They may still be a hacker, but the odds are much smaller. Just by taking this small simple step you greatly reduce your chances of sharing information that you wish you hadn’t.
Is it spam or is it phishing? 05/23/19
I am truly delighted with the number of malicious emails that are being forwarded to abuse@mtroyal.ca. The Mount Royal community is doing a great job of letting us know what to look for and helping us defend their data. There is one question that people keep asking though, what is the difference between Spam and a phishing email? I thought I would take a moment to clarify.
Spam email
- Goal is to sell you something.
- It is sent to hundreds or thousands of people at a time.
- Reading the email does not generate an emotional response.
- It may or may not contain links
- Clicking on the links will take you to the organizations website.
Phishing email
- Goal is to steal your data or use your workstation as a tool to access data on other people’s devices.
- It can be sent to thousands of people or just one or two.
- Reading the email generates an emotional response.
- It may or may not contain links and or attachments.
- Clicking on the link or opening an attachment takes you to a fake web page and/or loads malware onto your device.
The easiest way to determine if what you are dealing with is spam or phishing is by examining the purpose of the email. If it looks like they are trying to sell you something, then it is probably spam. If it looks like they are trying to confuse or trick you, then it is likely phishing.
Spam emails should be marked as spam by clicking the stop sign icon in the Gmail menu bar. Phishing emails should be forwarded to abuse@mtroyal.ca. If you aren’t sure which one it is, forward it to abuse@mtroyal.ca and we can let you know.
Fake package tracking email found in MRU inbox – 05/14/19
The latest phishing attempt is quite lovely. The criminals have made it purposely vague with the hope that it will peak your curiosity. Here is what is looks like.
![]()
If you have recently ordered something online. curiosity could get the better of you. If you click the link, this is what you find.
![]()
You were promised a PDF, which is usually but not always safe to open. However, you are given a Word document instead. It’s the old bait and switch. Having navigated to this point safely, you are more likely download the document. Of course if you do, malware is downloaded with it.
Remember troops, stop and think before you click. Stay safe out there.
Another Rahilly phish making the rounds – 05/08/19
The gift card scammers are giving another go at trying to convince employees that our new president Dr. Rahilly is trying to contact them.

This time they have managed to get his name correct, replacing the much loved Tin with Tim. They have also changed up the email address going with presidant to make it look more official. Although if they had spelled it right, it would have been more effective.
This is just another attempt at a gift card scam. If you check the sender’s email address before you read the body of the email, you will be less likely to have emotion override rational thought and reply in haste. If you are contacted by the “presidant”, just delete the email.
Think you won’t ever be tricked? Think again. – 05/03/19
Mount Royal has been targeted by the gift card scam for months now. It seems like every month we receive a dozen or so reports of emails that appear to come from Mount Royal supervisors asking employees if they are available. The scammers hope they will get a response. Once they have one, they attempt to convince the employee to purchase gift cards and send them the redemption codes.
Last week the scammers came very close to being successful. A Mount Royal employee responded to the scammer and was about to go out and purchase gift cards as instructed when they thought they should double check with their supervisor’s admin. This sober second thought saved them hundreds if not thousands of dollars and a lot of embarrassment.
You are probably thinking you would never get sucked in like that. But dollars to doughnuts, that employee who responded thought the same darn thing. When our emotions get engaged, rational thought is bypassed. Hackers know this, that is why they create emails designed to do just that. You may think you cannot be tricked however when you receive an unexpected email that appears to come from your boss, your emotions get engaged. Rational thought is gone and all you want to do is follow instructions and make your boss happy.
So how do you defend against such an attack? When you open any email, the first place your eye needs to go to is the sender’s information. You need to engage rational thought before emotions can be triggered by what is in the rest of the email.
Check the email address and make sure it is legitimate. If the email address is not a Mount Royal address then you know it isn’t coming from your supervisor and it can be deleted. Only once you have established that the email address is correct do you read the email itself. Remember that the email may still be malicious. Just because it looks like it came from your boss, doesn’t mean it did. Their email may have been compromised. Look for red flags and if anything seems amiss contact your supervisor to make sure they did indeed send the email.
Must Read – No we don’t have a secret email service – 04/23/19
A new phishing email is showing up in MRU Inboxes and Spam folders. It looks like this:

The first question you should ask is why would you receive an email about unread messages? However, if the panic over missing out on 2 messages throws common sense out the window, a glance at the sender’s email address should alert you. If you miss that clue and click on the REVIEW NOW link in a desperate attempt to avoid missing out, it takes you to this web page:

If you have gotten to this point, there is a good chance you will think that MRU has a secret email service outside of Gmail that you weren’t aware of. As a result, you will have no issues with entering your Mount Royal login credentials to access the mysterious messages. That is exactly what the hackers are hoping you will do. Once you do, Bob is your uncle, and they have control of your Gmail.
Let me assure you that the only email messages you will every receive from Mount Royal University will come through and be received via Gmail. You will never have to login to another email service to receive messages.
If this or a similar emails show up in your Inbox or Spam folder, delete them. If you ever have questions about the legitimacy of an email that you have received from us, please forward the email to abuse@mtroyal.ca and we will be happy to investigate for you.
Must Read – The impersonators noticed we have a new president – 04/18/19
The Mount Royal impersonators are continuing their gift card scam. However, they have figured out that we have a new president and they have changed tactics accordingly. The latest phishing emails appear to come from Dr. Tim Rahilly.

This causes concern for two reasons. First, they are obviously monitoring our website for information to put into phishing emails. Second, as Dr. Rahilly has not yet officially begun his term there may be some confusion about his email.
To clarify things, he has had an official Mount Royal email address for quite some time. If you receive an email that appears to come from him, please check the email address to ensure it is correct. If you are unsure, please forward it to abuse@mtroyal.ca and we will check it for you.
Another variation of the MRU imposter phishing email – 04/02/19
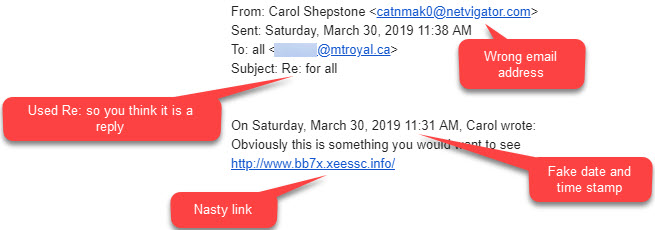
Once again miscreants are trying to catch our employees off guard by hitting them with a phishing email that appears to come from a fellow Mount Royal employee. Fortunately for us, our employee identified the odd email address and stopped the attack cold.
The clever criminals added some distracting details to try and trip up their intended victim. They added a Re: to the subject line plus a fake time and date stamp to make it look like the email was a reply to a previously read email. They know we tend to trust email replies and they bet that the odd email address wouldn’t be noticed. They were wrong.
Our superhero employee saved the day by forwarding this bad boy to us instead of clicking on the nasty link. Keep a look out for this one.
If it shows up in your inbox, be a superhero and forward it to abuse@mtroyal.ca.
