Sextortion scam surfaces at MRU – 07/30/18
Brian Krebs was the first to report on a clever but disturbing sextortion scam making the rounds. Unsuspecting people everywhere, including members of the Mount Royal community, are receiving a version of this email:
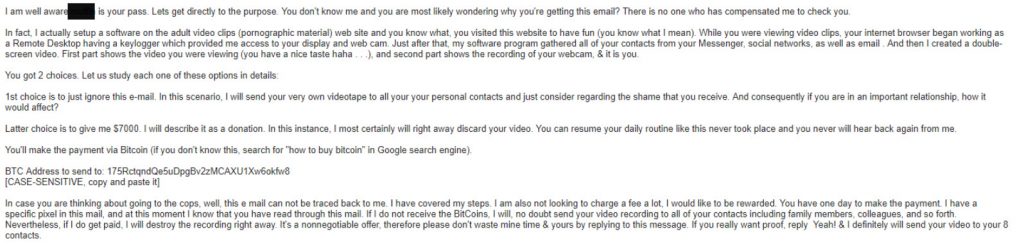
What makes this email so alarming is it correctly displays your password. In the majority of cases, the password is an old one and has been changed ages ago. However if you have been naughty and this email shows up in your inbox, you may be tempted to pay up and save your reputation.
The good news is, the password was collected from a data breach and not because they have hacked your machine. The blackmailers do not have a video of you behaving badly, nor do they have your contact list. Your reputation is safe and no one has to be paid off to make sure it stays that way.
Watch out for fake vacation deals – 06/14/18
With summer just around the corner, scammers are setting the bait with deals on cheap flights, huge discounts and hotel bargains. These too good to be true offers are often exactly that. If you receive an unsolicited email or text advertising a holiday deal use your cyber safety skills. Visit websites of companies you know directly and search for reviews on those you do not. If you are tempted to take the bait, pause and make sure:
- you are dealing with a reputable known company
- you have read the negative as well as the positive reviews
- the domain name is correct and typosquatting isn’t being used
- you read all terms and conditions
- there is a way to contact the company should things go wrong
- the site URL displays https before you enter payment information
- payment is made with a credit card
University of Regina breach due to weak passwords – 05/28/18
Last year when a University of Regina engineering professor was checking grades, he noticed the class average had changed. When he investigated he found that some students’ grades had been changed and it appeared as though the Dean had done it. When the Dean was questioned, it was determined that his account had been compromised.
The University has conducted a thorough investigation into the hack over the last year and have determined that weak passwords and the faculty use of default passwords were responsible for the security breach. The student responsible was expelled.
As a result of the breach, the University has made several changes to their systems and have recommended mandatory training for all employees.
This a reminder to keep your accounts secure with strong passwords that are unique for each account. If you would like to learn how to create strong passwords that are easy to remember or learn how to easily and safely store passwords, sign up for a workshop, complete the online training or contact me at bpasteris@mtroyal.ca and I would be happy to help.
Alexa secretly records and messages a private conversation – 05/28/18
A couple in Oregon thought Amazon’s Echo was just the thing to make their life easier. They purchased the device and then connected it to their environmental controls, lights and security. With Echo, they could use the Alexa voice assistant to control their whole home with voice commands. Everything was wonderful until they received a panicked phone call from someone on their contact list telling them to unplug their Alexa device. Without the couple’s knowledge, a message had been sent to him containing a recording of their private conversation. He was sure they had been hacked.
Unfortunately, that wasn’t the case. No hack had occurred. In fact, Alexa had become ‘confused’. According to Amazon, the voice assistant ‘heard’ a word similar to Alexa that caused it to start recording. It then ‘heard’ a string of requests that resulted in the recorded conversation being sent to the panicked caller. Amazon has since assured the public, that occurrences such as this are very rare and that they are working to reduce the odds even more.
For this Oregon couple though, the trust has been broken. Feeling violated, they will never be plugging the device in again. They are choosing the privacy of their home over the convenience of a voice assistant.
Sources:
- (2018, May25) ‘Alexa are you recording this?’ The Calgary Herald, NP6
- http://business.financialpost.com/technology/personal-tech/amazons-alexa-eavesdropped-on-a-couples-conversation-and-then-sent-the-recording-to-someone-else
Check those photos you are posting on social media – 05/18/18
When sharing with friends, family and colleagues on social media, check your photos carefully before you post them to make sure you aren’t sharing too much. Just ask the Hawaii Emergency Agency or the RAF how embarrassing it is to have sensitive information broadcast over the Internet. I am choosing to ignore that fact that they used horrible judgement when it came to password storage and management, as nauseous as it makes me. Instead I want to focus on the fact that they failed to recognize the photos would be handing out their login credentials to anyone who can use the zoom feature on a browser.
Other photos found on the Internet have displayed phone lists with employee’s home phone numbers, accounting codes, employee id cards and passwords.
Before you post a photo online, take a really good look at it. Zoom in on details. Make sure that there is nothing sensitive in the photo. Look for contact lists, house numbers, license plate numbers, account numbers, bill statements, invoice statements, credit card statements or anything else you want to keep confidential. Don’t count on the text being too small or out of focus to read. With the right software, a hacker can make almost anything readable.
Twitter asking users to change their passwords – 05/04/18
Why is twitter asking all its users to change their passwords? They discovered that login credentials were being stored unmasked in an internal log. This means anyone at the company who opened this log could see users’ passwords and usernames. A HUGE no no. The good news is, they have no evidence that suggests any passwords or account information have been stolen. Now this doesn’t mean that some Twitter systems analyst hasn’t taken down your credentials to use at a later date, it just means they don’t think it has happened.
While this is a huge embarrassment for Twitter, for most of its users it will likely be nothing more than a lesson on the importance of having two step verification enabled. Those lucky ones who reuse passwords will also be reminded why it is better not to as they scramble to remember all the accounts that use the newly exposed password.
Give your emails your undivided attention – 04/16/18
Firefox Can Keep Facebook from Tracking You – 04/03/18
With the announcement that Cambridge Analytics was collecting info on Facebook users without their explicit consent, more and more users are concerned about using the platform and what that means for their privacy.
In response, Mozilla has released an extension for their Firefox browser that limits what Facebook can track beyond the open browser tab. Installing the Facebook container extension keeps tracking limited to what occurs in the open browser tab that is currently displaying Facebook. Any activity outside of that browser tab is off limits and for the most part will not be reported back. This of course only works while you are using a version of Firefox that has the extension installed. It does not limit tracking on other devices or browsers.
The downside is you may not be able to use your Facebook account to login to other sites or be able to comment on sites that use the Facebook comment plugin.
Want to learn more about this extension and how to use it? Check out this Naked Security article.
How to protect your facebook data – 03/22/18
With the news that hundreds of thousands of Facebook users had their information collected and distributed without their knowledge, many people are rethinking their Facebook accounts. Especially as it was all done legally in accordance with Facebook’s Data Use Policy and their Terms of Service.
If you are not ready to turf your account altogether, there are some things that you can do to protect your data:
- Set up Login Alerts.
- Make sure your posts aren’t searchable
- Make sure only friends can see your posts.
- Only let people that you know contact you, search for you or add you.
- Enable two-factor authentication.
- Stop using your Facebook account to login to other apps.
- Audit apps that currently connect to Facebook.
Whew!! That is quite a list. Kinda makes you wonder if it is really worth all the effort. Maybe it is easier to just pick up the phone and call your friends.
How do you know for sure your buddy sent you that email? You don’t. – 02/14/18
While navigating the scary world of cyber security, most of us have felt safe clicking on whatever we find in an email from a trusted friend or colleague. After all we know who they are. However, did you know that it is possible for a cyber criminal to send you an email with your friend’s name and email address sitting in the sender field? That’s right. You can receive an email that appears to come from someone you know, but in reality comes from a criminal.
How is one to determine if the email actually comes from the person who appears to have sent it? If you simply reply to the email and ask, you may be talking to the hacker. If you use any contact information in the email, you may be talking to a hacker. The only way to determine if an email legitimately comes from someone you know is to call them using a phone number you know is legit . That’s right, you have to pick up a telephone, call them and ask if they sent you the email. I know many of you are shaking at the thought of having to actually have a conversation over the phone, however this is the only sure way to know if the email came from them.
Some of you may be thinking, “Hey I can just email them using an email address that I know is legit”. Problem is, their email account may be compromised and they may not even know it. Others may be thinking, “I can just look for phishing red flags“. You are right, you sure can. However, cyber criminals are getting better and better at constructing emails. There are fewer and fewer red flags to spot. If you choose not to make the call, you are taking a risk. Make your life less stressful, just pick up the phone. One call can guarantee the click is a safe one.
