New cybersecurity awareness training goes live August 15 – 07/19/2023

It is that time of the year again. Time to say goodbye to last year’s training and say hello to a brand new year of cybersecurity fun. The training for new hires is now live and new employees are being enrolled automatically every Monday as they were last year. However, the rest of the program does have a few changes.
First, training for current employees won’t be launched until August 15 when faculty returns to campus. This does shorten the time that is available to complete the training. However, now notifications won’t be going out to people who aren’t here.
Second, contractors are now required to take training as well as employees. We decided to expand the cybersecurity awareness program as last year we experienced a cybersecurity incident that originated with a contractor.
Third, the training completion due date for current employees is now June 15. New hires will continue to have 60 days to complete their cybersecurity awareness training and 30 days to complete their PCI awareness training. By moving the deadline ahead two weeks, faculty will no longer be getting reminders when they are not on campus and it will be easier to meet our PCI compliance requirements.
Lastly, all our training content this year has been approved by the EDI office. Previously only our Cyber Guys videos were reviewed. This change ensures that all our content falls in line with the University’s strategic direction to strengthen diverse communities.
The rest of the training program remains unchanged. Current employees can still test out of training. As well, our monthly Cyber Guys videos will continue to deliver giggles every month starting in October.
We hope these changes make the program more effective and less onerous. We welcome your feedback on the changes or any other aspect of the program. With your input, we can continue to improve ensuring the program helps the entire campus stay cybersafe.
How to mark an email as unread on your phone – 07/18/2023
When reading an email on your phone, it is challenging to determine if the email is malicous or not. The screen is just too small to see the red flags, increasing the chances you will become a victim of a cyberattack.
Reading an email on your phone is perfectly safe. However when you are asked to take action, mark the email as unread and read it again later on a larger screen. While this is great advice, how exactly do you mark an email as unread on the Gmail app?
To mark an email as unread on the Gmail app:
- Open the email
- Click on the envelope in the upper right hand corner
Twelve character passwords are now being hacked on a regular basis. 08/01/2023

For years you have been hearing that a strong password is greater than 8 characters long, has uppercase letters, lowercase letters, numbers and symbols. Today that is no longer the case. The threat actors now have computing power and tools that allow them to brute force hack any 8 character password in less than a day.
So how long should your password be? Well that depends on whether you have created the password yourself or have had a password manager do it. According to experts, if you generate the password yourself, it has to be 20 characters long. If you have a password manager generate a random one for you, then it only needs to be 12 characters long.
Why the discrepancy? The thought is the human brain cannot generate a random enough password to keep criminals out. We tend to use dictionary words and dates making it easier for these types of passwords to be cracked. In comparison, a password manager generates a completely random combination of characters which is much more secure.
I know what you are thinking, isn’t 20 characters overkill? Well we have had multiple accounts on campus brute force hacked in the past year. The passwords were unique, were used no where else, had 12 characters or less and included all the recommended characters. There was no way that the passwords could have been stolen from elsewhere. A brute force hack is the only explanation of how the accounts were compromised.
A 20 character password may be secure, but if you are trying to come up with a single word that is that long, it can be bloody hard. The whole process is easier if you use four random words that have meaning to you, but would be nonsensical to anyone else. Once you hae your words, insert a number into each one and capitalize one letter in the word. You can use spaces as your special character or replace the spaces with a special character. For example, saddlepad blue shiny bay, becomes s4addlepaD#b4luE#s4hinY#b4aY.
To make it easy to remember, I insert the same number in the same place, captialize the last letter and replace the spaces with the same symbol. The result is a monster password that will take years to crack but can be remembered.
While having a 20 character password will keep your accounts safe for now, it won’t be long before we will need 33 character passwords or longer. To add an extra layer of security, enable multi-factor authentication on all your accounts so that if your passwords are cracked, the attackers won’t be able to gain access.
Smart employee sees a correct email address and verifies anyway – 06/20/2023
Payroll was hit repeatedly this week with change bank requests. The requests looked legitimate. They came from a Mount Royal employee and the email address displayed was correct.
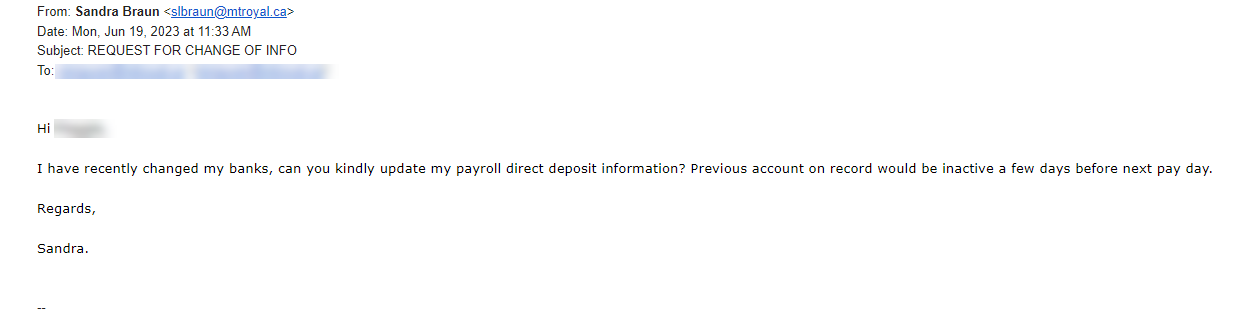
Fortunately, this wasn’t Payroll’s first rodeo and they knew that the sender’s email address was just a text field. An attacker could easily enter anything they like into that field. They also knew to verify that the request was actually made by the displayed sender. For this reason, they created a new, second email with a screen shot of the one received and asked the displayed sender if they had in fact sent the email. The answer was no.
Payroll’s quick thinking saved themselves and their colleagues days of heartache and a whole lot of money. This is a great illustration of why it is so important to verify that an email is legitimate before you act on it, even if the sending email address is correct. Just by taking a few extra minutes to send a new message, text or call; you can avert disaster and save the day just like Payroll did.
Campus slammed with fake performance reviews and faculty bonuses – 06/15/2023
This past week was a busy one for the cybersecurity team. The campus was slammed with document share invites from Google that were designed to look like they came from campus chairs and supervisors . Here is an example of one of the emails.

While it clearly states, in big letters at the top, that Benjamin Clark is sharing the document, the document description says that it is Ranjan Datta who is doing the sharing. This can confuse you just enough to make you open the file. If you do, you will be asked to enter your Google login credentials before you are able to view the document. Once you enter your login credentials, you are indeed able to view it. However, your login credentials will have also been sent to the attackers. If the attackers are clever enough, you aren’t even aware that anything is amiss.
Fortunately, It is fairly easy to spot these impersonators if you pay attention to what Google is saying and ignore the description that the attacker has entered. Google will always post the name and email address of the person sharing the document in big letters at the top of the email. In addiition if that person does not have a Mount Royal email address, a pale yellow banner appears above the Open button letting you know. In comparision, the description is in a normal size text and appears just above the name of the shared file.
By taking a pause and analyzing the email, you can avoid having your email compromised. That said we are all human and make mistakes. If you think your login credentials may have been stolen, change your password immediately by visiting the MyMRU login page and clicking the Change Password link.
If you find one of these suspicious looking emails in your inbox, please report it using the PhishAlarm button or by forwarding it to cybersecurity@mtroyal.ca. Your quick actions allow us to alert your colleagues and prevent them from becoming victims.
The space audit is coming, cover up sensitive information – 05/31/2023

Starting June 12, Facilities Management will be conducting its annual space audit. Employees will enter all rooms on campus in order to update space information. Photos will be taken to record the condition of finishes, furniture layouts and equipment. Part of the project involves auditors creating work requests in the Frontline system for maintenance issues they identify.
Why reporting phishing emails matters- 05/18/2023

You see them on a regular basis. They arrive in your inbox asking you to click on a link, open an attachment or provide personal information. If you do, you lose your data, gain a virus or your money disappears. These pests in our inbox are called phishing emails. Cyber criminials fill them with tempting bait like invoices, delivery notifications and offers of free money.
Gratefuly, these annoying emails only appear periodically. It is unusual to get more than 7 in a week. You can thank IT Services for that. They use a variety of hardware and software tools to detect this pestilence and remove it. As a result, the majority of phishing emails never even make it to your inbox.
Unfortunately, ITS can’t keep 100% of malicious emails out of your inbox. If they did set up those types of defenses, you wouldn’t receive any emails at all. They must leave some leeway to allow legitimate emails to be delivered. Phishing emails get through because the defense tools consider them to be legitimate until they are identified and flagged as malicious. The only way these emails get flagged is if you report them.
There are actually three ways to report an email. First, there is the PhishAlarm button. This button is located in the right side panel of the Gmail window. When you open an email, you will see the button appear. Click the button, click Report Phish and you are good to go. Reporting this way isn’t just easy, it also captures information from the email header and includes it in the report so it is easier for ITS to analyze the email.
Unfortunately, not everyone has access to the PhishAlarm button. If you are not an employee of MRU, you won’t see it. Therefore we have a second way for you to report. You can forward the email to cybersecurity@mtroyal.ca. Using this method is a little more work and we don’t receive the same information about the email but at least we are notified so your colleagues can be too.
Lastly, you can also report the email directly to Google. It takes a little more effort, you have to click the three dots in the upper right hand corner and then select Report Phishing from the menu. However, once Google receives the report they can flag the email. If enough people flag it, it gets pulled from inboxes. Google also adds the email to its blocked list so future versions are kept out of inboxes entirely.

If you just delete a phishing email and don’t report it, we can’t notify others of the threat and Google can’t block it or pull it from inboxes. As a result, it continues to be a threat to your colleagues, family and friends. Email reporting is an essential part of our defenses. We can’t fight the cyber criminals without you. Regardless of what method you use, please report phishing emails.
See what information Google is collecting about you – 03/27/2023
On a weekly basis, we hear about evil Google and its data collection practices. Fortunately, you can see exactly what data Google is collecting and limit it. To make this whole process easier, Google has a Privacy Checkup that you can run.
To run the Privacy Checkup:
- Open Chrome or Gmail.
- Click on your profile picture in the upper right hand corner of the window.
- Select Manage your account from the drop down menu.
- In the left hand menu, click Data & Privacy.
- Click Take Privacy Checkup.
Smishing attack thwarted by faculty member – 03/14/2023
It was just after 11:00 AM on a Friday when Kelly Sundberg received this text message
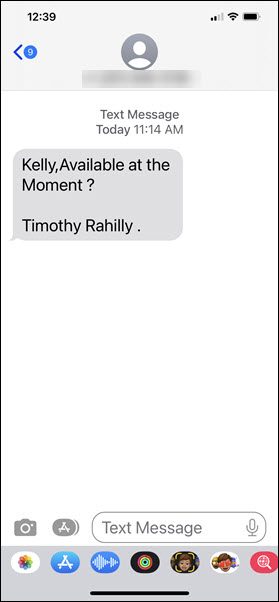
This was an odd request as the text was coming to Kelly’s personal phone. However, if something was urgent, maybe it was Tim texting him. What Kelly did next saved him from being scammed out of thousands of dollars, he contacted the Presiden’ts office and asked if it really was Tim that had texted him.
As it turns out, Tim wasn’t even in the city. The text had definitely not come from him. It had come from a scammer whose next move would have been to convince him to purchase gift cards as rewards for hard working colleagues.
Before you say, “I would never fall for that scam”, know that more than one person on campus has. It isn’t because they are stupid or because they didn’t take their cybersecurity awareness training. They became victims because the attackers are just that good at confusing you, creating urgency and getting you to react instead of think.
Kelly did two very important things right, firstly he stopped and let his rational thought kick in before he took action. As a result, the attackers did not have a chance to confuse or manipulate him. Secondly, he followed the guidelines in the cybersecurity awareness training, verify before you take action.
No matter how certain you are that a text or email is coming from your boss, if an unexpected request is made, call the sender and make sure the message actually came from them. That one step saved Kelly, it could save you too.
Scam calls now appear to come from an MRU phone number – 02/02/2023

Previously, I had written a blog article warning about callers impersonating Visa and asking for your credit card information. The scam has evolved and is now more sophisticated. Employees on campus are receiving calls that appear to come from an MRU phone number stating there is an issue with purchases on their P card.
As with the Visa scam, the attackers ask for your P card information to confirm who you are. No one who has a legitimate reason to check your P card purchases will call YOU and ask YOU to confirm YOUR identity. Neither will they ask for any information on the card.
If someone calls you asking for this information, please hang up. If you have recieved this type of call and have given out card information please contact Finance immediately and let them know.
Regardless if you have received one of these calls or not, check for fraudulent transactions on your P card regularly. Quick action minimizes the damage a scammer can do.
