Cyber Safety Summit 2018 – 04/23/18

The Cyber Safety Summit 2018 will be held on October 2, 2018 at the Lincoln Park room in the Main Building of Mount Royal University’s campus. The summit will include experts speaking on home security, social engineering, fraud protection and how to recover from a cyber attack. In addition we are adding a new topic this year, protecting your privacy. Registration is free.
Spend the whole day with us or just come by for your favourite session. Either way you have the opportunity to hear from the experts themselves how to keep your family and home cyber safe. Come with your questions and concerns, leave armed with the knowledge you need to keep hackers at bay.
Can’t attend the summit? We will be live streaming all sessions. Visit the website to review last year’s program and to sign up for Summit updates.
Mark your calendars now!! See you on October 2, 2018!!
Fake software updates installing malware – 04/19/18
Legitimate websites are being infiltrated by hackers who inject malware that looks like a software update into the site’s code. The malware detects which browser you are using and displays an authentic looking update notification that matches. The malware is very stealthy as it only displays the fake update notification once. This has allowed it to avoid detection until now even though researchers believe it has been in place since at least December 2017.
How do you know the difference between a legitimate update notification or malware disguised as one? You don’t. The criminals are getting just that good. If you receive a notification that an application or browser needs updating:
- Close your application/browser.
- Reopen the application/browser.
- Go to your application/browser settings.
- Locate and select the Update command.
Note that the Update command is sometimes found with the About this application information instead of with the settings. Updating the application or browser within the application itself is the only safe way to ensure your application or browser is up to date.
How to spot fake businesses on Google Maps – 04/18/18
Cyber security expert Bryan Seely did some digging and discovered that large numbers of service businesses listed on search engines were fake businesses. They have no office location or business license. They simply answer calls and dispatch servicemen. However, when the service is provided customers are often charged much more than the quoted amount. In addition, if the consumer has a complaint later the business listing has often disappeared. Because these fake listings are so well marketed, they take customers away from legitimate businesses significantly affecting their viability.
When he brought this information to the search engines attention he was ignored. When he tried to engage media, he was ignored. However, when he wiretapped the Secret Service he finally got someone’s attention and Google Maps responded with a temporary fix. Unfortunately the bad publicity wasn’t enough to get them to do what needs to be done to fix the problem permanently.
So where do you turn if you are looking for a service business? Fortunately, the majority of service businesses in Yelp’s top listings are legitimate. Yelp works a bit differently than Google Maps and others, they create the listing and the business owner claims it. This model greatly reduces the number of fake businesses on the site. However, they still have their share. So how do you determine whether the business you are calling is legitimate or a fake?
- The business name is the name of the city followed by the name of the service. For example, New York Locksmith. Fake businesses select business names that will get the most search engine hits.
- Stock photography is used for the business photos or the photos are similar to those found on other sites. There is no real business so they have no photos of it to post.
- The have less than double digit reviews. A business that is legitimate will have been online for some time and have double digit reviews.
- The reviews are all 4 or 5 star. Most businesses will have a variety of reviews not just top rated ones.
- The reviews don’t span the life of the business. If they only have reviews listed for one year and they have been in business for 5, there is something wrong.
- If you click on the person who left the review and they have reviewed several businesses of the same type. Someone who has left 7 reviews for locksmiths is either getting paid to write reviews or locks their keys in their car an awful lot.
- They don’t have a business license. Most legitimate businesses will be licensed.
- They are hiding their address. Scammers will hide their addresses so it is more difficult to report them to Google and the consumer cannot see that it is just a post office box.
- The website looks very similar to other websites. Scammers will often set up several fake businesses with websites that are identical except for the name and a few graphics.
- The price advertised is too good to be true. Fake businesses will list ridiculously low prices for a service and when they show up to perform it, suddenly change the price.
Unfortunately, some legitimate businesses will meet some of the criteria. However, only fake businesses will meet most of them. If you aren’t sure if a service business is legit, call them and ask them about their business license, if they are bonded or insured, where they are located, for a written service quote and how to identify their employees. If they balk on any of those questions, hang up and look for another one.
Those cute quizzes are sucking up data about you – 04/11/18
With the fallout from Facebook’s poor choices continuing, this is a great time to remind everyone that big brother is always watching. As fun as those cute little quizzes are on social media, you could be giving hackers everything they need to impersonate you.
Quizzes that ask you the name of your first pet, what was the first car you drove and where you went to school are thinly disguised attempts at getting a hold of the answers to privacy questions. Outside of privacy questions, even seemingly innocent information about your past can be used against you in the wrong hands.
When it comes to quizzes, just don’t. Your privacy is not worth a few moments of entertainment.
ALERT – Mount Royal staff victimized by phishing email that is a reply to an old thread – 03/26/18
Mount Royal employees are receiving emails from a vendor that are actually replies to a legitimate message. As the message is a reply and it is from someone we do business with, employees have been tricked into opening the attachment more than once putting our network at risk.
How the heck did they manage to reply to a message that the vendor had sent ages ago? Simple, the vendors email account was hacked. Once the hackers had access to the email account all they had to do was scroll through the emails in the sent folder until they found one that mentions an invoice and reply to it. Of course they attached an edited invoice containing a nice little keylogger trojan onto it first.
Those that opened the attachment found a blank document and then contacted the Service Desk to see why. The Service Desk calmly explained all their keystrokes were being recorded by malware they had unintentionally installed and then sent support staff to re-image (wipe clean and re-install) their machines.
Unfortunately this is not the first time that Mount Royal University has been targeted by this type of attack. Late last year another vendor had their email account compromised and multiple Mount Royal staff members received replies to an old meeting invite containing a document that “required their input”. That document contained malware as well and once again we were re-imaging machines.
How do you know when an email from a vendor contains a malicious link or attachment? Truthfully, you don’t. The only red flag on either of these emails was the date of the original message. The email thread was months old and was used in the attack because it contained a subject that would allow an attachment to be added to it without looking odd. However, a recent message could also have been used if it had contained the right content.
So how do you protect yourself from such attacks? You call the vendor when you receive an email with a link or attachment and confirm that they sent the email. You do not reply to the email as if their email account has been compromised, you will be conversing with the hacker. Do not use the contact information found in the email to contact the vendor either. The hacker may have changed the email signature. Use a contact number that you find in a Google search or that you have used before.
Yes, horrors, you have to actually pick up the phone and talk to a person. However, it will practically eliminate the risk of having your machine wiped clean and the operating system re-installed. Not a fun way to spend the morning.
Windows 10 Cortana can be used to access your locked computer 03/12/18
With the Windows 10 anniversary update Cortana, the voice assistant, is enabled by default. It can be asked questions and accessed even if your device is locked leaving it vulnerable to hackers. This was brought to everyone’s attention when researchers were messing around and discovered they could get Cortana to visit a malicious website just by asking regardless of whether the screen was locked or not. If you don’t use Cortana, this isn’t an issue. However if you do use it, you can change its settings to turn off when the screen is locked. Check out this How-To_Geek article to find out how.
Mount Royal Community Member gets fake CRA call – 03/09/18
One sure sign that spring is on its way…tax scammers pop up along with the tulips. Although we are a ways away from enjoying the tulips, the scammers are out in full force. One Mount Royal employee came into work to find this on his voicemail.
Click the far left of the bar to listen to the voicemail message.
Pretty nasty huh? So how to do you know this is a scam? Simple, the CRA will never phone you and threaten legal action or arrest. They will never send someone to your house to collect payment or to arrest you either. This was a voicemail, so it was easy to calmly listen to the message and analyze it to determine if it was legitimate.
What do you do if they have you on the phone and they are threatening you? The scammers can be very insistent and believable causing considerable stress and confusion. If you experience a call like that from the CRA, tell them you will call them back and hang up. You can then contact the CRA at 1-800-959-8281. If there are any issues with your taxes, whoever answers the phone will be able to address them.
Watch out for phishing emails from the CRA as well. As I mentioned in a post last year, the CRA will never email you unless you have given them previous permission to do so and they will never send you an email with links unless you have specifically requested a document.
For more information on how to identify CRA fraud and protect yourself, visit the CRA website.
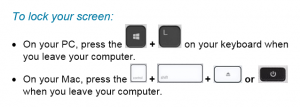
Lock your Screen When you Leave the Scene – 02/07/18
Just a friendly reminder to lock your screen EVERY TIME you leave your workstation unattended. In the time it takes to get a print out or go to the kitchen to throw out garbage, your workstation can be compromised. The hackers need less than a minute to access your workstation and load malware that runs in the background. The malware can be present for months, giving the criminals access to the network and our data without you even being aware that it is there.
It is not enough to say, “Well I usually lock my screen but sometimes I forget.” Usually will not keep our network safe. Always will. Join us in the fight against cyber crime. Be a super hero and lock your screen EVERY TIME!
Why you should worry about cryptocurrency mining – 01/26/18
First things first, what is cryptocurrency? Cryptocurrency is digital currency. The most known is Bitcoin, however others are popping up such as Monero. How do they work? Well, I found a nifty little video that tells you the basics. It refers to bitcoin but the premise applies to all cryptocurrencies.
Neat huh? Notice the part where they say it takes lots of computing power and lots of electricity to mine? This is where things get interesting. Criminals have figured out that if they use the computing power of other machines, they can mine more cryptocurrency faster without having to invest in all the computing power or electricity themselves.
Why should you be concerned? More and more malware is mining cryptocurrency. The malware is often hidden on legitimate websites, applications or browser extensions. Why is this a problem? After all it is just using the processing power of my computer, its not actually doing any real harm is it? Well, no and yes. No it isn’t doing anything malicious like encrypting your hard drive or stealing your data. However, it is wearing out your machine and slowing it down. The more clever mining malware waits until you aren’t actually using your machine to mine. This reduces the chance you will notice that it is actually there, but still wears out the processor, eats up bandwidth and increases your electricity bill. Less clever creations, slow your computer down to a noticeable crawl.
Having millions of other peoples computers mining cryptocurrency for you can be quite lucrative. So much so that some websites have turned from using adware to generate revenue to asking users to lend their computing power. This is just fine if the user knows it happens and consents. It is another thing entirely when its done behind the scenes. Finding out your machine is being used for mining after the fact tends to leave you feeling like you need to take a shower. Its just not nice.
So what can you do about it? First of all, if your workstation seems slow contact the Service Desk. If it is your home machine, check the CPU processes to see if you have any spikes in usage. How do you prevent the mining in the first place? The mining software is considered to be malware, so the regular security measures that you take to protect yourself from malware will protect you from crypto mining. Make sure you:
- Use an Ad blocker
- Stay away from shady websites
- Only download software from reputable sites with good reviews
- Beware of browser extensions
Mount Royal Employees Receiving Recorded Messages From “Google” – 12/11/17
Several employees on campus have been receiving calls ask them to verify their business on Google. The caller is a recorded voice or robo call. If you choose to press 1, you are connected to a person who tries to sell you a service. They are not from Google, but are using Google’s name to sound legitimate. Their service is a scam as verification of a business on Google is done through snail mail, and there is no charge for it.
If you receive a robo call, make note of the organization calling and hang up. You can then contact the organization directly and determine if they have a legitimate need to contact you. Robo calls are usually trying to sell you something or are scams.
Scammers don’t just use robo calls to con you out of your hard earned money. They will call you directly as well, creating a sense of urgency to trick you into signing up for an over priced service that you don’t need. If a person calls you and asks for payment of a service over the phone, ask for the name of the organization and tell them you will call them back. Google them and check reviews of their service. If you decide that you do want to sign up, contact the organization directly using the contact information found in the Google search. Do not be tricked into using a phone number that the caller gives you. If they are legitimate, you will be able to contact them using a publicly available number.
