Used a public computer lately? You may have left your credit card data behind. – 01/09/17
How I almost fulfilled my dream of owning a pair of red soled shoes
Most days the horror stories I read about and pass along to our community do not directly affect us. They are simply tales of cyber security woe that I pass along to warn the unsuspecting in an attempt to prevent a possible future disaster. Today was different. Today I had an OMG moment. Once of those moments when the world seems to go on pause while you try and process what you have just seen. Today one of our lovely analysts in ITS put a library loaner laptop on my desk. The type of laptop that hundreds of students and staff check out of the library for temporary use every week. On the screen plain as day for everyone to see, was the credit card information of the last person who had logged into Google Chrome on the laptop.
After the shock had worn off, I briefly entertained the idea of doing some post Christmas shopping. I had always wanted a pair of Christian Louboutin’s red soled shoes. However, sanity kicked in and I realized that if this one unfortunate individual had made such an enormous mistake, then there is probably a pretty good chance that others have too.
How was such an error made? How did his credit card information get on that laptop? Google Chrome is to blame. To understand how this could happen, you need to understand how Google Chrome works. Chrome has this fabulous little time saving feature called Autofill. As you fill out forms, Chrome will ask you if you want it to remember the information. Things like passwords, your address and yes your credit card information. So the next time you are asked for it in a form, Chrome fills the form out for you. This is a feature that you can disable. Thing is, if at any time you enabled it and information was stored, the data remains stored in Chrome until you go in and delete it.
That is exactly what happened with our poor library laptop borrower. They opened Chrome, synced their account so they would have access to their bookmarks and then when they were done they closed Chrome and returned the laptop. Thing is when you sync your account it syncs everything including your Autofill information. In addition, when you close Chrome it does not turn sync off, so the next person who comes along and opens Chrome sees all your bookmarks and has access to your Autofill information which in this case included address and credit card data. Thankfully the good people at the library noticed something was up before it was loaned out again and disaster was averted.
I really would love to go shopping on your dime, however my tastes are rather expensive…Louboutin’s start at 500 Euro… so I think the smarter thing would be to tell you how to avoid leaving your personal information on a workstation that isn’t yours.
- If you plan on accessing your Google bookmarks on devices or workstations that are not your own, disable Autofill and delete any stored information.
- When you are done working in Chrome on someone else’s workstation, turn off sync. Logging out of Gmail does not turn off sync, it just pauses it while your passwords and autofill entries remain accessible to whoever is using Chrome.
By following these two simple steps, you will avoid receiving a bill for a pair of these beauties.
Consider getting Rid of Your Yahoo Account – 12/16/16
With more information everyday coming out about the extent of the hack at Yahoo it may be time to dump your Yahoo account. The scariest part about the breach? It has been determined that the hackers got a hold of Yahoo’s code for cookies and have the possibility to forge them. Why is that so scary? It allows the hackers to access user accounts without passwords, making changing your password a useless exercise. Yahoo is contacting users who may have had their cookie information stolen. However, do they really know which users have been effected and to what extent?
Have a Yahoo account, but you aren’t sure how to proceed? Check out this article from KrebsOnSecurity.
Dailymotion Accounts Hacked – 12/07/16
Around the 20th of October, 85 million usernames and emails were taken from Dailymotion servers along with 18 million hashed passwords. For those of you who don’t use Dailymotion, it is popular video sharing website. Because the passwords were encrypted, it will take some time for the cyber criminals to crack them. This gives users time to change their passwords on their Dailymotion account as well as change the password for any other accounts using the same password.
Once again this drives home the importance of having a different password for each account. It is not a matter of if one of your accounts will get hacked, it is a matter of when. Limit the damage…use unique passwords.
How to Avoid ATM Fraud – 11/28/16
As the Christmas shopping season goes into full swing, cyber criminals are upping efforts to steal your hard earned cash. Most people have heard the horror stories of devices called card skimmers being placed on ATM card slots. These devices scan the magnetic strip on your card while tiny cameras capture your finger movements as you enter your pin. The majority of you have been educated enough to not use ATMs that have large plastic thingy’s sitting over the card slot.
However, the latest card skimmers are so thin they are inserted inside the card slot and are impossible to detect. Check out this video.
How do you protect yourself from such ingenious technology? Simple, cover the pin pad as you enter your pin number. The information that a skimmer scans from your card is useless without the pin. If you cover the pin pad, the criminals camera is unable to record your pin regardless of where it is placed.
Want to reduce your chances of encountering skimmers at all? Only use ATMs that are physically installed in a bank, they are harder to hack. Also, try and avoid using ATMs on weekends. Thieves tend to install these devices on a Friday when they know the bank won’t be open for a while.
Technology is every changing and so are the criminals methods. As careful as we may be, a breach may still happen. Reduce the damage by keeping an eye on your bank statements and disputing any unauthorized charges immediately.
Happy Shopping!!
What happens when a cyber criminal steals your account? – 11/21/16
So, the worst has happened…someone has hacked your account and taken it over. You have called the help desk and had the password reset. All is good right? Wrong. When a cyber criminal gets ownership of your account whether it is an email, social media profile or gaming account they typically do the following:
- Change your name
- Forward any mail to another account
- Delete/steal your mail or delete/steal content or credits
- Change your signature
- Add secondary email addresses to the account
- Steal any stored credit card data.
This means when you get your account back you have to:
- Make sure the correct name is associated with the account
- Check to see if mail is being forwarded
- Ensure the email signature is correct
- Look for secondary email addresses that have been added and delete them
- Cancel any credit cards associated with the account
If that isn’t irritating enough, lets add one more goody to the list of annoyances that come with a compromised account…if your account was used for spamming, you will have the joy of receiving hate mail as well as having a lot of messages that you send to others bounce back due to spam blockers. Unfortunately there is no way to re-mediate that. For this reason, most people who have their accounts hacked will end up abandoning them and creating a new one. But hey…you got your account back.
AdultFriendFinder Hacked! – 11/16/16
A massive data breach of the adult dating and entertainment company Friend Finder Network has exposed more than 412 million accounts, including (and this is really bad) over 15 million “deleted” records that were not purged from the databases. Over the weekend it became clear that 339 million names, addresses and phone numbers of registered users at the AdultFriendFinder site were hacked. All these records are now owned by cyber criminals, exposing highly sensitive personal information. On top of the AdultFriendFinder records, 62M accounts from Cams.com, and 7M from Penthouse.com were stolen, as well as a few million from other smaller properties owned by the company.
Cyber criminals are going to leverage this event in a lot of different ways: (spear-) phishing attacks, bogus websites where you can “check if your spouse is cheating on you”, or ways to find out if your own extramarital affair has come out.
Any of these 339 million registered AdultFriendFinder users are now a target for a multitude of social engineering attacks. People that have (had) straight or gay extramarital affairs can be made to click on links in emails that threaten to out them.
There will be phishing emails that claim people can go to a website to find out if their private data has been released. This is a nightmare that will be exploited by spammers, phishers and blackmailers who are now gleefully rubbing their hands, let alone the divorce lawyers and private investigators that are going to pour over the data.
Be on the lookout for threatening email messages which slip through spam filters that have anything to do with AdultFriendFinder, or that refer to exposing your activity on the site and delete them immediately, both in the office or at the house.
Do not click on any links or open attachments in emails that appear to come from AdultFriendFinder. Instead, go directly to the website to change a password or get more information.
Please forward this to friends, family, colleagues and peers.
Read the Phishing Email that did Podesta in – 10/28/16
Poor John Podesta, he checked with his security team and they let him down. Check out the email thread from Wikileaks and see how his team was fooled. This one is very sophisticated. The sender address looks completely legit. The only way you know it is a phishing email, is the CHANGE PASSWORD link (the link appears as a URL), does not take you to google. His staffers did tell him to go to the site directly to change his password, but being the busy guy he is he used the link.
How do you avoid being compromised like John?
- Do not click on links in unsolicited emails.
- If you feel the email is legitimate, go to the site directly using a URL that you know is legitimate. Do not use the URL in the email. Do not use a link in the email.
The New Posterboy of CyberInsecurity: John Podesta Fell For Social Engineering Attack 10/24/16
The other thing of note here is that this particular phish spoofed a security alert notice from Google .
In Podesta’s case the bad guys used a bit.ly link , which is very common. And the landing page for the credentials phish probably looked something like the one below…
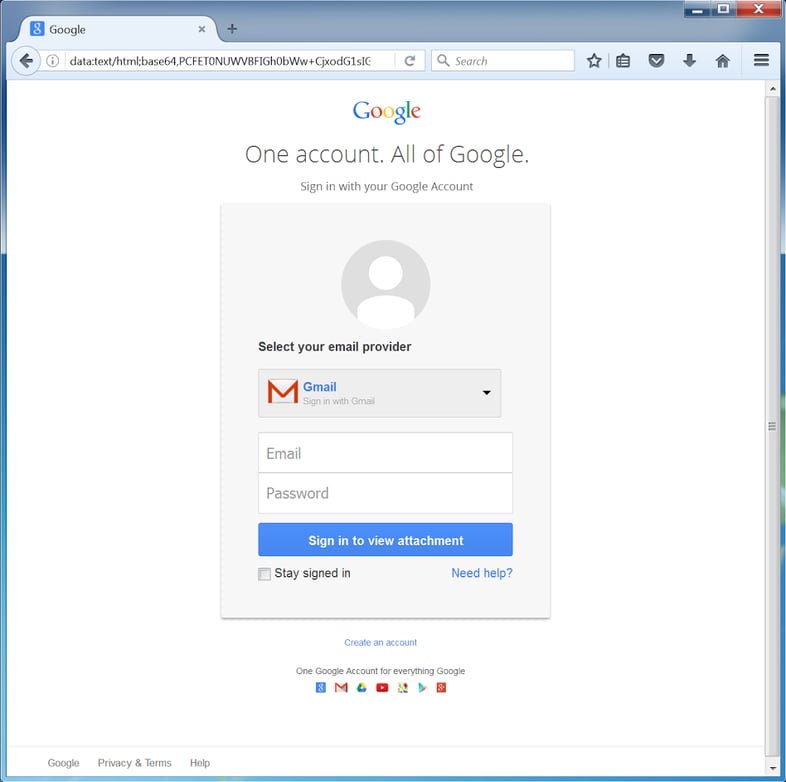
- Using a terrible password to begin with
- Re-using that password for multiple sites/accounts
- Sharing the password with assistants
- Asking an assistant to email him his password when he forgot it
- Not turning on two step verification
- Not changing passwords after one account was known to be compromised
(Taken from KnowBe4)
Dropbox and Adobe Breach Affects Mount Royal Users 10/24/16
In 2012 there was a very large breach of Dropbox and Adobe credentials. At that time, Dropbox and Adobe passwords were compromised. We have been notified that Mount Royal email addresses were associated with this breach. As a result, we are concerned that some users may have used their Mount Royal password for their Dropbox or Adobe login as well.
If there is any chance that you used your MyMRU password for Dropbox or Adobe we are asking you to change your MyMRU password immediately. This will also change your Mount Royal Gmail/Google and Blackboard passwords. To change your password, please use the “Change your password” link located on MyMRU.
As login credentials for any site can be compromised, we are encouraging everyone to always use a unique password for each of their accounts. Using a password manager such as KeePass is an easy and safe way to generate, keep track of and store your passwords.
For tips on creating strong, secure passwords and using KeePass, please refer to the Creating Passwords section of the mru.ca/itsecurity webpage.
We thank everyone for doing their part to keep their accounts secure.
Security on Dating Sites – 10/4/2016
Dating sites are popular ways to meet new people. However, not all sites have adequate security. A database containing data from users of HaveAFling, HaveAnAffair and HookUpDating was found on the open web unsecured. The information could be accessed without using a password. The data that could be accessed included names, contact information and bios. The company has since rectified the situation, however if you were one of the users of HaveAnAffair, you may be getting an angry text from your significant other.
When deciding to post personal information on a site or through an app, stick with larger companies who have been around for a while, invest in data security for their users and are reputable. Better yet, date the old fashioned way and ask out the cutie strolling down Mainstreet.
Want to know more about the data breach? Check out the ZDNET article.
