Get your security updates, restart your machine – 05/15/17
Although the WannaCry ransomware exploited a vulnerability in Windows that had been patched in March 2017, it was still able to bring several organizations to their knees. The culprit? Computers running outdated software that did not have the security patch installed. As a best practice, all Mount Royal staff and faculty should be installing updates when prompted and be restarting their machines. This ensures they are always using the most secure software versions and minimizes the risk of a malware attack.
Security isn’t the only benefit of keeping your machine up to date. Regularly updating your machine keeps it more stable so it crashes less. Also, updating the machine takes less time if it is done regularly.
Yes, I know…it’s inconvenient. It takes time for the machine to restart and it’s a total pain. Here’s a tip…turn your machine off at the end of each day and any updates will automatically be downloaded. When you come in the next morning, turn on your machine and go get that morning cup of Joe. By the time you get back, your machine will have installed the updates and be ready to go.
Have you downloaded the updates but can’t restart your machine right away because you are working on a project or running a report? Make sure that when the notification appears asking you to restart your machine that you do so within 24 to 48 hours. Do not continually ignore the prompts and leave your machine vulnerable.
Worried about meeting room or classroom computers? All smart cabinets, classroom computers and meeting room computers are automatically turned on and updated during off hours. As long as no one is logged into the machine, it will be updated. Have any questions? Give the IT Service Desk a call.
What you should know about the worldwide ransomware attack – 05/15/17
Friday the world was given a sampling of exactly how much damage ransomware can cause. Cyber criminals released a brand new form of ransomware that had the capability to replicate itself and infect other machines on the same network. This allowed it to spread at a very rapid rate. The ransomware’s more notable victims were the NHS, UK’s healthcare sytem and the Spanish telecom giant Telefonica. Surgeries were cancelled, ambulances were diverted and services were interrupted.
This ransomware called WannaCry, took advantage of a vulnerability in Windows that had been found by the NSA and then published on Wikileaks. In March, Microsoft issued a patch that effectively eliminated this vulnerability. You may be wondering why millions of machines became infected if this vulnerability was addressed. The answer is two fold. First, Microsoft has stopped supporting older operating systems such as XP and Vista. That means they do not normally provide security patches for these operating systems. Second, many users do not install the latest updates.
So how to you keep your data safe from WannaCry and other malware?
- Backup your files regularly
We are human, at some point we may click on something we shouldn’t. If all your files are backed up, you can restore your system if you are hit by malware.
- Keep all your applications secure by installing all updates
Programmers are human too. Sometimes their programs are released with vulnerabilities that allow criminals to use the programs for their own purposes. When those vulnerabilities are found, they are fixed with a software update. If you do not install your updates, you leave your computer vulnerable.
Do you have a XP or Vista machine? You should consider upgrading to Windows 7 or 10. In the meantime, Microsoft has taken the unprecedented step of issuing Vista and XP updates to address the vulnerability WannaCry exploits.
- Verify all links and attachments in unexpected emails before opening them
To date the majority of malware is delivered by a user clicking on a link or opening an attachment. Phishing emails are no longer containing, poor graphics, bad grammar or are coming from strangers. More and more attacks appear to come from someone you know, contain relevant content and are slick in their appearance. To truly stay safe, you should contact all senders of unexpected emails containing links or attachments by phone and verify that they actually sent the message.
By following these simple steps, you will avoid the heartbreak of WannaCry.
How to Limit the Potential Damage from Stolen Credentials – 05/11/17
Another day, another list of Mount Royal emails that may have been compromised. How? The emails were used as usernames to login to external websites/accounts. These external websites then had their user’s login credentials stolen. This is not a concern if each website has a unique password. However if you reuse the same username and password combinations for multiple websites, once one is compromised they are all compromised.
As it is not a question of if but when one of your websites has their user’s credentials stolen, how do you minimize the damage?
- Avoid using your Mount Royal email to login to external websites whenever possible. Some sites require your work email to access their services. However the majority of sites allow you to enter any email address.
- Create a separate gmail account for logging in to work related websites. New accounts can be created/added from the Google login page. Once a new account has been added, you can view its inbox on a separate tab giving you access to both your accounts at once.
- Use personal emails for personal sites. This will save you from embarrassment. When a site has a Mount Royal email in its list of usernames and it gets hacked, we are notified. We really don’t want to know that you have a Neopets account.
- Use a unique password for every website. Having difficulty coming up with and storing so many passwords? Use a password manager to store and generate passwords.
- Change your passwords regularly. A significant amount of time often passes before theft of login credentials is detected giving criminals lots of time to use them before they are changed. Changing your password makes stolen credentials useless.
Alert – Mount Royal Target of Spear Phishing – 05/05/17
Mount Royal employees are being targeted in a new high impact email phishing campaign. What makes it so alarming?
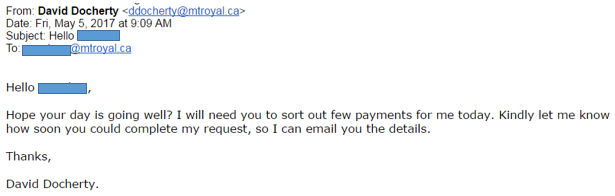
- The email sender is David Docherty and it appears to be coming from his Mount Royal email address.
- It disguises its malicious intent by using a friendly tone and it doesn’t contain a link or attachment that usually accompanies a phishing email.
However, it should raise a red flag because normal payments are not requested this way. Take a look:
How do you protect yourself against this type of attack?
- Always pay attention when processing your emails. Do not multitask.
- Be familiar with your department’s procedures and processes. Anytime you receive an email that goes against those procedures or processes, you should contact the sender directly to confirm it’s legitimacy.
Remember, just because an email looks like it comes from someone you know, doesn’t mean it is. Just because an email doesn’t contain links or attachments, doesn’t mean it isn’t malicious.
Huge kudos to our people in Finance who identified this. You are our superheros!!
Alert – Fake Invitations to View a Google Doc – 05/03/17
There are two new phishing emails that are making the rounds with fake invitations to view Google Docs. They are both very clever and they are both sent from someone that is in your contact list. The first one is a bit easier to spot as it looks something like this:
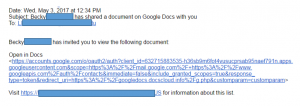
For those of you who have received an Invitation to View a Google Doc before, it is easy to pick up what is amiss with this email. However for those of you who haven’t, this is what a legitimate Invitation to View a Google Doc looks like. When you click the Open in Docs button, the document is opened for you.
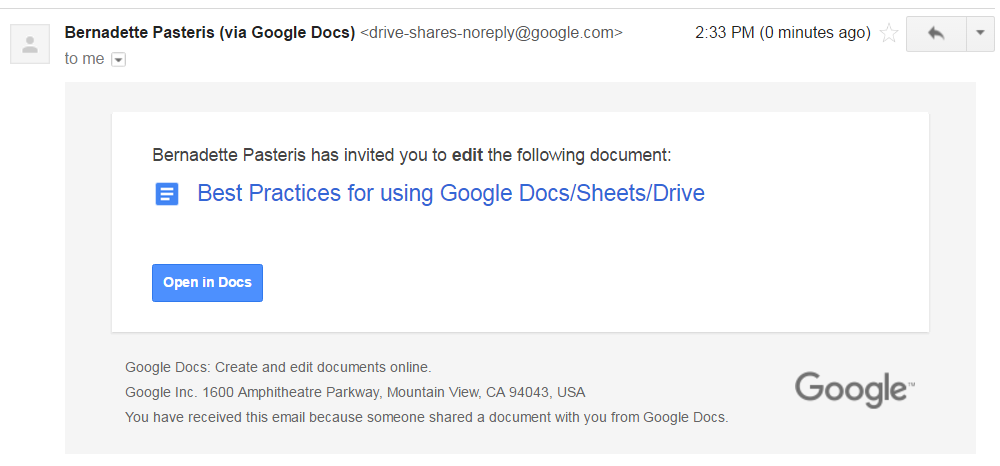
The second phishing email is more sophisticated in that it looks a lot like a legitimate Invitation to View a Google Doc. The only thing missing from the email is the name of the document. However if you click on the Open in Docs button instead of viewing the document, a dialog box appears asking you for permission to access your email. This is the tip off that something is awry. Google Docs does not need access to your email to function.
If you see a dialog box instead of a document when you click the Open in Docs button, DO NOT CLICK on anything. Disconnect your computer from the Internet and call the IT Service Desk. If you want to learn more about this phishing campaign, check out the CBC article.
As these latest phishing campaigns show, criminals are getting more and more sophisticated in the development of their phishing emails. It is getting harder and harder to determine what is a legitimate email and what is a scam. To avoid becoming a victim of cyber crime, verify the legitimacy of all unexpected emails containing links or attachments regardless of who they come from.
McAfee Logo Has Changed – 05/02/17

Just a heads up for staff and faculty. If you take a look at your task bar in Windows and see a new icon, don’t worry it’s just McAfee’s updated logo. McAfee is the antivirus software that is loaded onto all Mount Royal workstations. Don’t have the new logo yet? Don’t worry the logo is updated in stages, it will eventually be your turn. If you have any questions or concerns, contact the ITS Service Desk.
