See what information Google is collecting about you – 03/27/2023
On a weekly basis, we hear about evil Google and its data collection practices. Fortunately, you can see exactly what data Google is collecting and limit it. To make this whole process easier, Google has a Privacy Checkup that you can run.
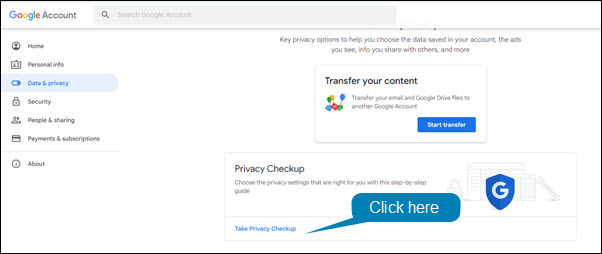
To run the Privacy Checkup:
- Open Chrome or Gmail.
- Click on your profile picture in the upper right hand corner of the window.
- Select Manage your account from the drop down menu.
- In the left hand menu, click Data & Privacy.
- Click Take Privacy Checkup.
What to do about those annoying pop-ups

It has happened to everyone, you visit a website and then shortly one or more pop-ups show up on your screen. Admittedly, with the availability of popup blockers this happens a lot less than it used it. However, it still happens. Those popups are not just annoying, they are often dangerous. Cyberattackers use them to trick us into downloading malware onto our machines.
While there are many ways attackers try to trick us. They have two favourite methods. The first is to fill the popups with pornography. There is nothing more horrifying than having naked people flash on your screen especially when you are at work. The idea is to make you panic so you will click on the X in the popup window to close it. It can be very effective. Anyone in that situation would do exactly as the attackers want and click to close the offending windows as quickly as possible. Unfortunately, once you click you download malware onto your computer.
The second method they like to use is the fake virus alert. The popups appear with flashing read text and flashing arrows directing you to click to remove a virus that they have detected on your machine. They are playing everyone’s worst nightmare in technicolor. It is understandable if someone panics and clicks. However, as before, once you do malware is loaded onto your machine.
The terrifying thing is popups can show up anywhere, not just on dodgy sites you have never visited. Legitimate websites can also be compromised by attackers. One day you are checking the Daily Kitty with no issues, the next day you visit and obscene images fill your screen.
The good news is, there is an easy way to get rid of the unexpected popups without downloading malware. The next time your screen comes alive with dozens of panic inducing popups, just close your browser. Don’t click on anything inside the browser window, just click the little x on the browser window itself and close the thing. Once the browser is closed, the problem is gone.
To make sure it doesn’t reoccur, don’t visit the website that you were on again. As long as you close the browser window and not the popup window, no harm is done. Even better, nothing else needs to be done. No report needs to be made to IT. You don’t have to scan your machine for viruses. You don’t have to spend the day wringing your hands hoping that you didn’t mess up. You can just enjoy the rest of your day in blissful serenity knowing that you stopped the criminals in their tracks.
Chrome’s latest update includes a confusing pop up – 06/01/22
Chrome has been updated. As part of the update, a pop up appears when you login

This pop up is simply reminding you that Mount Royal University is managing your MRU Workspace account and that we have access to it. This new pop up is part of Google’s new privacy features. There hasn’t been any changes to your account, the University has always had access to it. The pop up isn’t malicious and your computer has not been hacked.
Click to select Keep local browsing data to save your current bookmarks. Then click the Continue button to close the pop up and use Chrome/Google Workspace as usual.
MRU community hit by tech support scam – 04/29/21
The tech support scam is back. This week a MRU community member had a virus warning popup on their screen while they were working. The virus warning listed a phone number and appeared to come from Microsoft.
The individual phoned the Service Desk. However, when they couldn’t get through they called the ‘Microsoft’ number in the pop up. The fake Microsoft rep hung up on them when the caller didn’t provide the rep with the information they were looking for. Our MRU community member avoided being scammed simply by not being cooperative. However, had they been dealing with a more patient scammer, this could have gone very wrong very quickly.
This is a reminder if you see a dialog box with a virus warning and a phone number, it is a scam. Most likely there is no virus on your machine. instead, the website that you have visited has been compromised by a hacker to display a fake virus warning to anyone who views it. If this happens to you, close your browser and then open it again. Do not close the pop up. Do not visit that website again.
If you are concerned that your MRU issued device may have a virus, contact the Service Desk. Be patient, they will get back to you. If it is your personal device you are concerned about, run a virus scan. If something appears to be amiss and the virus scan does not find anything, take your device to a repair shop to have it checked.
Google Chrome Privacy Settings you Should Check – 03/17/21
A while ago I posted an article on Data Privacy Day. Out of that article, several readers requested recommendations on privacy settings for Google Chrome. As much as I would love to tell readers to lock down everything and shut down the great Google data collection, privacy is a very personal thing. One person may be willing to give up functionality of their tools to ensure their private information stays private, while another is just fine with all knowing Google collecting their data if it means their life is easier. In short, I cannot tell you wonderful people what to lock down. Each one of you has to make that decision for yourselves.
That said, I can tell you what settings to check and where they are currently located. Google, just like most other service providers, likes to make them hard to find. A cynical person would say that was done on purpose. I have decided to be more positive today and I am going to blame poor interface design… I am trying here. Work with me.
Decide how your browsing history is used in Chrome
Most of the privacy goodies are hidden under Settings>Sync and Google Services. The first stop should be Control how your browsing history is used to personalize Search, ads and more. Click on the little square next to this monster and you find the Activity Controls.

At first glance, all you see is Web & App Activity. Scroll down a bit and click the See all activity controls link to find the motherload.

These settings determine how much functionality you want from Chrome vs how much data you want to keep from their prying eyes. It may take a few tries to find the right balance for you. Don’t be afraid to turn on some controls. You can always turn them off if they are making your life difficult. Personally I prefer to give them as little information as possible and find things on my own. I don’t like to be fed my content. You can stumble upon some pretty interesting stuff when you don’t have someone curating your content for you. However, that might not be your jam. Totally okay.
Further down the Sync and Google Services page, there are some other settings that you should check. Do you want to help Google be a better service, or send them your URLS or the text you type into the browser? Once again, try turning them off and see what happens to the functionality of Chrome.
Decide how you will be tracked
Cookies are used by websites to identify you for a variety of reasons. Some of them are useful like keeping track of what is in your shopping cart. Others are more concerning like tracking what you click on. As with all browsers, Chrome lets you decide what types of cookies are okay and which are to be disabled or blocked.
Chrome’s cookie settings can be found in Settings>Cookies and other data. I do not recommend selecting Allow all cookies or Block all cookies. However you may want to experiment with Blocking third party cookies.
Another setting you can consider is the Send a “do not track” request with your browsing traffic. As it suggests, it simply sends a request to a website that you not be tracked. How they respond to the request depends on the website. However, I feel better knowing that I have at least asked for some privacy. The odds that they honor that request are probably pretty slim. There I go being all cynical again. Sorry, I slipped.
Cover your tracks
Your browsing history including cookies, cached pages and autofill data can be cleared out manually or you can set it up to perform a cleaning at regular intervals. Ideally things should be cleaned out once a week, however the best cleaning interval for you depends on how you work. Do be aware that if you clean out cookies regularly, it may mean you have to re-enter things on sites over and over again. As with the other settings, experiment with it to find what works best for you. You can find these settings under Settings>Clear Browsing data.
Inconclusion
Even if you try out these settings and decide to not enable any of them, that’s perfectly okay. The important thing is you are aware of them and know how to change them. You are taking control and making decisions about your privacy instead of having them made for you.
Unfortunately, account providers regularly change their privacy settings and Google is no different. The information in this article may be out of date in a week, a month or tomorrow. Therefore, I suggest that every quarter you take a look at your privacy settings and make sure they are still at a comfortable level. A little proactivity goes a long way when maintaining your privacy.
Criminals are creating look-a-like MRU webpages – 04/23/20
We have been notified that cybercriminals have registered and are using the domain www.mroyalu.ca as well as several other look-a-like domains. They are attempting to fool people into visiting their malicious websites.
While working from home, it is very important that you double check all links that you receive in emails and the sender’s email address.
If the link does not have mtroyal.ca, mru.ca, mrucougars.com or mymru.ca before the first single / in the URL, it is malicious.
Examples of legitimate URLs are:
mru.ca/cybersecurity
mru.ca/wellness
https://www.mtroyal.ca/AboutMountRoyal/WhyMRU/
https://www.mymru.ca/web/home-community
Examples of fraudulent URLs are:
https://www.mroyalu.ca/AboutMountRoyal/WhyMRU/
https://www.mymur.ca/web/home-community
https://www.my.mtroyal.ca/Home
Please do not let curiosity get the better of you, and attempt to visit any of these fraudulent websites. They will harm your machine and/or steal your data.
If the sender’s email address ends in anything other than @mtroyal.ca, then it is malicious.
Examples of legitimate email addresses are:
bpasteris@mtroyal.ca
cybersecurity@mtroyal.ca
Examples of fraudulent email addresses are:
bpasteris.mtroyal.ca@gmail.com
bpasteris@mroyalu.ca
bpasteris@mtroyal.email.ca
Please be extra cautious at this time.
Updated 04/27/20
No Chrome doesn’t scan for viruses – 04/08/20

While it is a blessing that most of us are able to work from home, it has its downsides. One of those is the level of security on our home machines and networks. To take advantage of this less than ideal situation, cybercriminals are going into full swing. One of their favorite methods of attack is the compromised or malicious ad.
These ads can be placed on tons of web pages and appear to be like any other digital advertisement. However, they are far from benign. They contain malicious code that can do a variety of nasty things to your machine. Ransomware, key loggers and plain old viruses are just a few examples of the goodies these innocent looking adverts can hide.
The attack vector of choice, is to have these lovelies display some sort of dialog box when you visit the site to get you to click and download malware. Some creative cyberthugs have come up with a rather clever twist to this tactic, a fake virus alert. That’s right folks, you visit a website and after a bit of browsing a dialog box appears tell you that you have no less than 5 viruses on your machine. Just to make it look all official, the dialog box appears to be coming from Chrome itself.
Here’s the thing Chrome doesn’t scan for viruses, it is a browser. So if you are getting a virus alert from Chrome, it is definitely a scam. Close the browser and avoid the website. Stay alert out there. Use common sense and wash your hands.
Academic institutions targeted with malicious Chrome extension – 12/06/18
A phishing campaign has been targeting academic institutions. The phishing emails appear to come from a post secondary institution and contain a link to a web page that hosts a harmless PDF. When the link is clicked, the user is asked to download the Font Manager extension in the Chrome Web Store.
Users that checked the reviews for the extension found lots of good reviews as well as a few bad ones. It turns out, the clever criminals copied reviews from other extensions to make the Font Manager look more legit and increase the chances people would download it. The funny thing is they copied the bad reviews as well as the good ones. For the most part the ruse worked with the extension being downloaded hundreds of times. Once downloaded the malicious extension logged keystrokes and allowed hackers to gain access to the network and desktops remotely. Several universities have been compromised as a result.
The malicious extension was only discovered because the criminals blew it. University employees arrived in the morning to find their computers’ browsers opened to English-Korean translators and their Keyboard switched to Korean. As the employees weren’t conducting research on Korean websites, they knew something was up. Had the hackers been more on the ball, who knows how long they would have retained network access.
The Font Manager has been removed from the Chrome Store. However, this a gentle reminder to only download extensions that you know are safe and you absolutely must have.
Browser extensions cause of Facebook data breach – 11/05/18
The BBC Russian Service has found data from 81 000 Facebook profiles sitting on the web. The data is apparently just a small sample of what was taken from 120 million accounts by a hacker selling his haul. It is hard to know if 120 million profiles were indeed hacked or if the breach is limited to what is currently on display. One would think that Facebook would notice 120 million profiles being accessed, so my guess is they don’t have much more than the small sample. After all, criminals aren’t known for their honesty.
Facebook is blaming malicious browser extensions. They are reporting that the extensions were monitoring user’s Facebook activity while shuttling personal information as well as private conversations to the hackers. The majority of information taken was from Ukrainian and Russian users, however profiles from all over the world were also pilfered.
This is a reminder to be wary of browser extensions. As with apps, only download ones that:
- You really need
- Have good reviews
- Have lots of downloads
- Come from reputable sites
Malicious browser extensions can be very difficult to detect as extensions update automatically. This allows hackers to create extensions that are harmless, until their first update. After that your handy extension starts doing all sorts of nasty things.
To reduce the risk, if you really need a particular browser extension consider disabling it when you aren’t using it. Lastly once you no longer need the extension, remove it from your browser.
Adobe Flash update also installs malware – 10/17/18
Criminals have been disguising Adobe Flash updates as malware for a while now. They are quite fond of compromising a legitimate website with a fake update pop up. Now there is a new twist on this old tactic. If you choose to install the fake update it actually does update Adobe Flash. however a cryptominer comes along for the ride.
Because the software does what it says it will do, most people don’t notice what is going on in the background. This allows the malware to go undetected. It isn’t until a few days or weeks have passed and the user finally gets fed up with their slow machine that the malware is discovered.
To avoid fake software updates, remember to visit the application’s site directly for downloads or select check for updates from the software’s menu. Those popups that appear while you are browsing are often loaded with malware.
