Student Sponsorship dodges a gift card scam – 02/09/2024

Spoofing is when an attacker sends an email that appears to come from someone you know. We have seen this attack method used to target the MRU community before. This time, the target was Student Sponsorship and the attacker was spoofing a well known sponsor. Here is the original email they received.
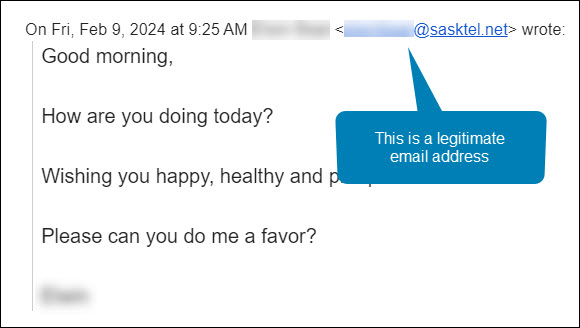
Maha was manning the Student Sponsorship inbox that morning. She was very familiar with both the sender’s name and email address. She hit the Reply button and asked the sponsor how she could help. Here is her response.
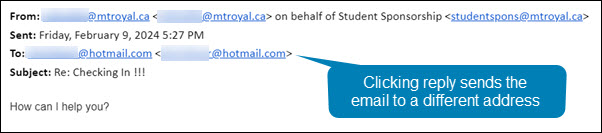
Notice how even though she hit reply, the email address in the To: field is no longer an @sasktel.net email address, but is now an @hotmail.com email address. This could only happen if the sender had edited the email header information so that the displayed sender email address was different than the replied to email address. In other words, they spoofed the legitimate email address.
There are legitimate reasons why this may be done. For example, a company wants to send with one email address to increase deliverability and a second one to receive emails because it is easier to remember. However, both emails will have the same domain name (the name that appears after the @). In this case, the second email address was created by a generic email provider. This is the reply that Maha got back.
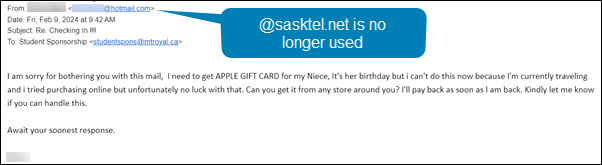
This confirmed her suspicions that something wasn’t quite right. The response she received back was no longer using the @sasktel.net email address and was asking her to make gift card purchases, it was a gift card scam. She forwarded the email to cybersecurity@mtroyal.ca immediately. Her quick actions saved her hundreds if not thousands of dollars.
When replying to emails, take a quick peek at the To: field. If the email address is different than the one that sent the email, proceed with caution. Someone may be trying to steal your money and/or your data.
New employees being targeted by the gift card scam – 11/02/2023

Universities are seeing another increase in gift card scams. However, this time they are targeting new employees. Those new to the University are unaware of policies and procedures around gift cards as well as the reporting structure. This makes them an easier target for criminals.
This is how the scam works. Attackers scan LinkedIn for those announcing they have started a new position at a university. Then they research the university and find the people most likely to be the new employee’s supervisor/chair/dean. They use this information to craft a very convincing email asking if the new employee is available.
Once the employee responds, they ask them to purchase gift cards for an employee reward program or some other plausible reason. The fake supervisor/chair/dean is usually in a “meeting” and only reachable by email. They add this detail to discourage the new employee from trying to reach the impersonator by other means.
If you are a new employee, be aware that no one at MRU will ask you to purchase gift cards with your own credit card. Suspicious emails that you receive can be reported by using the PhishAlarm button or by forwarding it to cybersecurity@mtroyal.ca
If you have a newer employee on your team, please let them know about this scam. Encourage them to contact their supervisor/chair/dean by phone or in person to confirm any requests to purchase gift cards. Your advice could save someone thousands of dollars.
Alert – Scammers user Flickr accounts in sextortion scam – 10/10/2023
Attackers are using compromised Flickr accounts to send email messages containing malicious links. The emails appear to list links to explicit images of the recipient. When they panic and click on the links to determine if the images are of them, malware is loaded onto their machine. The malware steals their login credentials.

If you receive an email demanding money and threatening to expose embarrasing or compromising images or information, report the email to IT Services using the PhishAlarm button. If the button is not available, you can report by forwarding the email to cybersecurity@mtroyal.ca. To remove the email from your inbox, report it to Google by clicking on the three dots in the upper right corner of the email and selecting Report phishing from the drop down menu.
Campus slammed with fake performance reviews and faculty bonuses – 06/15/2023
This past week was a busy one for the cybersecurity team. The campus was slammed with document share invites from Google that were designed to look like they came from campus chairs and supervisors . Here is an example of one of the emails.

While it clearly states, in big letters at the top, that Benjamin Clark is sharing the document, the document description says that it is Ranjan Datta who is doing the sharing. This can confuse you just enough to make you open the file. If you do, you will be asked to enter your Google login credentials before you are able to view the document. Once you enter your login credentials, you are indeed able to view it. However, your login credentials will have also been sent to the attackers. If the attackers are clever enough, you aren’t even aware that anything is amiss.
Fortunately, It is fairly easy to spot these impersonators if you pay attention to what Google is saying and ignore the description that the attacker has entered. Google will always post the name and email address of the person sharing the document in big letters at the top of the email. In addiition if that person does not have a Mount Royal email address, a pale yellow banner appears above the Open button letting you know. In comparision, the description is in a normal size text and appears just above the name of the shared file.
By taking a pause and analyzing the email, you can avoid having your email compromised. That said we are all human and make mistakes. If you think your login credentials may have been stolen, change your password immediately by visiting the MyMRU login page and clicking the Change Password link.
If you find one of these suspicious looking emails in your inbox, please report it using the PhishAlarm button or by forwarding it to cybersecurity@mtroyal.ca. Your quick actions allow us to alert your colleagues and prevent them from becoming victims.
Emails that appear to come from MRU can be malicious – 11/30/2022

Using Jabber on your computer? You need to update, NOW! 09/10/20
Cisco has released an update to their Jabber for Windows application. This update fixes a critical vulnerability that would allow an attacker to potentially execute arbitrary code on your computer without requiring any action on your part while the application was running in the background.
If you use Jabber for Windows please update it immediately. The Jabber for Windows update can be downloaded here. Enter your MRU login credentials when prompted to gain access to the download. Although Jabber for Mac has not been effected, it is still a good idea to keep it updated. The latest version can be downloaded here.
If you are only using Jabber on your iphone or Android smartphone, you are not affected by this vulnerability. For more details, read the Latest Hacking News article.
Coronavirus based attacks are rampant – 03/19/20
As employees all over the world are working from home, criminals are ramping things up hoping to take advantage of the less secure networks that people tend to have at home. We have surges in phishing emails on campus and across the world related to working from home as well as an increase in malicious websites. It has gotten so bad the US Secret Service has issued a warning. Here are some things to watch out for.
The fake VPN
As employees struggle to setup a home office, they are signing up and downloading VPN services at record rates. While all of our employees have the advantage of using SRAS, many smaller organizations do not have their own VPN tool and are asking employees to install one on their home computer. If your spouse or roommate are in this situation, warn them to be very careful about what VPN they download. Cyberattackers are offering fake VPN services that download malware onto your machine in record numbers. Make sure they check reviews of the service to ensure it is reputable before they install it on their machine.
Fake COVID-19 trackers
As people attempt to live their lives and stay safe, many are turning to maps that track the location and incidence of infections. Criminals are getting wise and creating their own versions of these tracking websites that infect your computer with malware.
Some enterprising scammers have also created phone apps that supposedly track the infection rate but load your device with ransomware instead. Stick to well known and reputable websites such as Alberta Health Services and the World Health Organization to get your information about the virus and stay away from any apps related to it including ones that tell you how to get rid of it.
Phishing emails about working from home and COVID-19
Phishing email attacks are off the scale. Everything from fake emails from your organization about working from home, to offers of vaccines and cures. One of their favorites is fake GoFundMe pages with coronavirus victims pleading for medical help. Another is pretending to be a colleague who is quarantined and needs help.
You name it, the depraved are going to try it. During this time it is especially important to be vigilant. If you receive an email that doesn’t come from a Mount Royal email address, question its validity. While you are working at home, make sure you use your Mount Royal email address to send business correspondence. DO NOT use your personal email address. This will make it easier for your colleagues to stay safe.
Sources:
https://www.securityweek.com/researchers-track-coronavirus-themed-cyberattacks
https://www.securityweek.com/other-virus-threat-surge-covid-themed-cyberattacks
Scammers targeting MRU are getting very creative – 07/17/19
In September last year, the first of several targeted email scams arrived in Mount Royal inboxes. Since that time we have see a plethora of these scams spread across campus. Up to now that have all been emails from a supervisor asking a report to do a favor for them.
However, we must have ended up on some “the Best People to Scam” list as this week the scams have gotten very creative. First up is a dude in Indonesia contacting Wellness Services to help him sell a helicopter (I actually think this might be legit). Second up is an email to the MRFA insisting a charge from their store has appeared on a bank statement (definitely not legit). Check out the pics!!

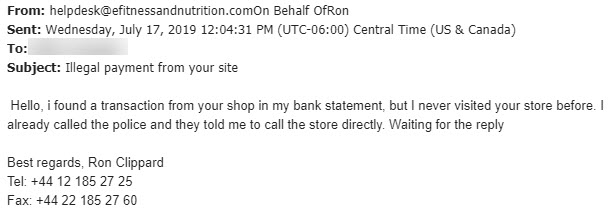
As entertaining as these emails are, that is not the reason why I am sharing them with you (well maybe a little bit). I am sharing them to give you a heads ups that MRU is being actively targeted and we all need to be on our toes. If you receive any email that is out of the ordinary, please take a closer look at it. If you aren’t sure if it is malicious, forward it to abuse@mtroyal.ca like your colleagues did and we can take a look. Everyone who reports an email gets a cool sticker. Be a superhero and report those malicious emails!
Must Read – MRU inboxes receive malicious Google Drive file share 03/20/19
Another day, another clever criminal trying to break into our network. This time they tried using the Google Drive to do it. Tuesday morning several employees found this in their inbox.
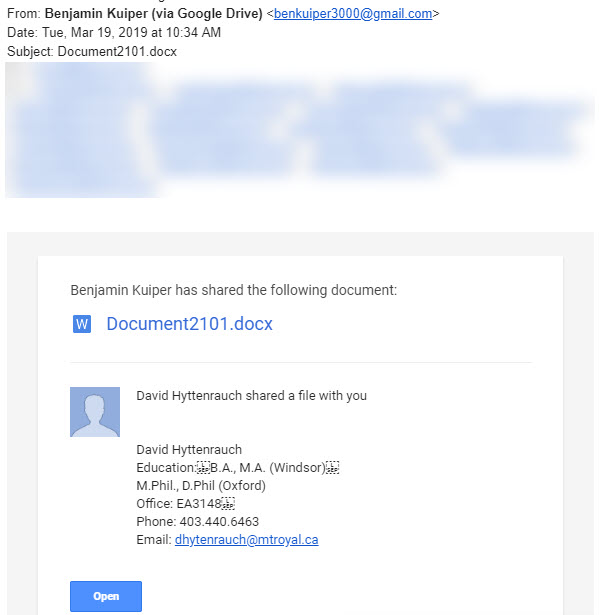
The Word Doc link is totally legit. If you click the link, it takes you to this document.

Clicking the link in the Word document takes you to a legitimate website that has been compromised. The site asks you to login to Office 360 to access the document. Of course if you do, you are giving some miscreant your Office 360 login credentials. They can then sell your credentials on the dark web or use them themselves to wreak havoc on your data as well as the data of others. Fun, Fun, Fun.
Because the Google Drive file share and the website are legitimate, they won’t be flagged by anti-virus or the firewall. It is actually very clever. However although it may get by the technology, a person can easily spot this as malicious. In fact, we had two different reports sent to abuse@mtroyal.ca about this one. Way to go MRU!!
For those of you who aren’t already yelling at the screen, “Come on, that is so obvious”, I am going to walk you through the red flags. First one is the email is sent by Benjamin Kuiper from the email address benkuiper3000@gmail.com. Clearly not a Mount Royal email and he is not listed in the directory. Fail number one.
Second, the doc says it was being shared by Benjamin and David Hyttenrauch. This doc was sent to people on David’s team so even though they didn’t know who Ben was, they sure as heck knew who David was. This got the desired attention. However, you can’t send an invite to share one file from two people. Clearly, this Word doc was shared by Benjamin and the sneaky dude entered the rest of the deceiving information into the Add a note field in the Share with others dialog box to make it looks like Dave was involved. Fail number two.
Third, when you open the document it tells you that you have a file waiting for you on the OneDrive. OneDrive file shares are not sent with links in Word documents. Fail number three.
Lastly, if you were to hover over the link in the Word document you would see that it does not go to OneDrive. Fail number four.
As clever as criminals are, most of them can be stopped by alert employees who take the time to look at emails with links and attachments critically. As we have seen in this example, the majority of the time phishing emails contain clear clues that something is not right. Don’t get caught up in the emotion of the moment. Like our wonderful employees, take the time to really look and make sure that the email is what it appears to be. Your data, your colleagues and your IT department will thank you.
Facebook breach – logout of your account 09/28/18
Today Facebook announced that they have discovered hackers have stolen 50 million access tokens. These tokens allow them to take over an account without having to login with a password. They did it by taking advantage of a vulnerability in the View As feature that allows users to see what their account looks like when viewed by others.
To solve the problem, they have logged out all the users who they believe were affected and disabled the View As feature. As often happens in these types of breaches, there is a possibility that at a later date they may find there are more people affected than originally thought.
To be on the safe side I suggest that you logout of Facebook by going to Settings and selecting Security and Login. There you can logout of all your devices at once with a single click. Alternatively, this might be a good time to get rid of Facebook all together.
