Smishing attack thwarted by faculty member – 03/14/2023
It was just after 11:00 AM on a Friday when Kelly Sundberg received this text message
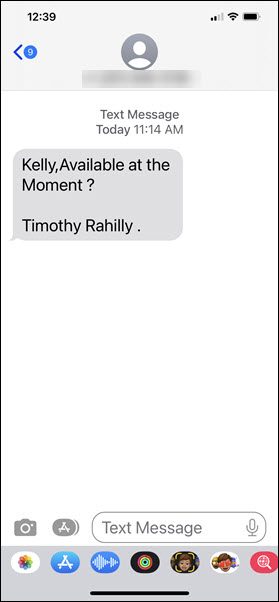
This was an odd request as the text was coming to Kelly’s personal phone. However, if something was urgent, maybe it was Tim texting him. What Kelly did next saved him from being scammed out of thousands of dollars, he contacted the Presiden’ts office and asked if it really was Tim that had texted him.
As it turns out, Tim wasn’t even in the city. The text had definitely not come from him. It had come from a scammer whose next move would have been to convince him to purchase gift cards as rewards for hard working colleagues.
Before you say, “I would never fall for that scam”, know that more than one person on campus has. It isn’t because they are stupid or because they didn’t take their cybersecurity awareness training. They became victims because the attackers are just that good at confusing you, creating urgency and getting you to react instead of think.
Kelly did two very important things right, firstly he stopped and let his rational thought kick in before he took action. As a result, the attackers did not have a chance to confuse or manipulate him. Secondly, he followed the guidelines in the cybersecurity awareness training, verify before you take action.
No matter how certain you are that a text or email is coming from your boss, if an unexpected request is made, call the sender and make sure the message actually came from them. That one step saved Kelly, it could save you too.
AHS offer of $100 for getting vaccinated is fake – 03/11/22
There is a particularly devious smishing attack currently being circulated. Check it out.

This one is extremely well done for several reasons. First, the chances are high that whoever receives this text is vaccinated. Second, the Alberta Government was indeed sending out $100 debit cards to those who got vaccinated last fall. Third, the link appears to go to Alberta Health Services. Lastly, we have all seen the sign-in partner prompt when dealing with the CRA or when receiving an e-transfer.
So what are the red flags? If you hover over the link, it will display a different URL than what you see in the link. In addition, the Alberta Government’s program was to distribute debit cards, not deposit money directly into your bank account. Also, that program ended in the fall and there is no new program to encourage you to get your booster.
No one I know has clicked the link to see what will happen. However, I can make a pretty good guess from the way the information is presented. Likely, the link takes you to a page that asks for your banking credentials.
As much as we could all use an extra $100 right now, this one falls into the “Too good to be true”, category.
Fake TD texts try to nab your banking credentials – 12/15/21
Look at what showed up on the phone of an MRU community member.

The links in this text do not go to the TD Canada Trust website. The person who received this text does not bank with TD so they knew it was a fake alert right away. However, if you do bank with them and receive this text, the odds are pretty good you will click. The whole alert received thing tends to make people panic. When they panic, they react. Rational thought never has a chance to kick in.
We don’t know for sure what will happen if you click one of the links. However, as it tells you to login, the odds are good that you will be directed to a fake TD login page. When you enter your username and password, the criminals will likely record and store your credentials to either use themselves or sell on the dark web. Either way, they can drain your bank accounts.
This is a reminder that if you receive an email or text from your bank, count to 10. Then call them directly using a phone number that you know is legitimate to ask them if there is a problem with your account. Resist the urge to click, no matter how great it is. Salvation is only a phone call away.
Beware text messages promising returns from your mobile provider – 11/28/20
Just when I thought it was going to be a quiet week, this showed up on my phone.

Considering how much we pay for cellular service in Canada, this is a mighty enticing message. I will admit it, I desperately wanted it to be true. I have two university students on my plan so you can just imagine what my monthly bill is. Having money returned to me by my blood sucking mobility provider is a dream. A message like that makes your whole day.
However, there is this little matter of the link…why does it have to have a link? Crud. Add to that the vagueness of the term mobility provider and you have a real life smishing attack. I have to admit though, I do love how they add the dreaded Data rates may apply in attempt to make it look official. That is rather clever of them.
I am not sure what is more annoying, the fact that I won’t be getting money back from my mobility provider or that the message interrupted my day. Okay I am going to be honest, it’s the money. That is definitely more annoying. For one brief moment I had hope.
Let’s take a closer look at how my hopes dissolved into wisps of despair. Firstly, if this was from my mobility provider, the actual name of the company would have been in the text. No organization is going to be coy about refunding you money. They are going to make sure you know who is blessing your day with a shower of funds. Second if they were issuing me a refund, they wouldn’t send me a text with a link. Unless I was closing out my account, they would just deduct the refund from my bill which is much more efficient and economical.
That said, I am an eternal optimist. I decided to check my account to see if perhaps I had overpaid and the blood suckers were indeed returning funds. I used my mobility provider’s app on my phone to check my account. My assumptions were correct, the text was fake. Nuts.
This is a gentle reminder to never click on links in text messages unless you have asked for the link to be sent to you. Instead access accounts through apps or a bookmark on your computer to verify information. No matter how tempting it is, don’t click.
Must Read – The MRU impersonators are ramping things up – 02/28/19
Phishing emails that appear to come from Mount Royal University supervisors are making their appearance again. This time they are throwing in the whole, “I am going into a meeting with limited phone calls, so just reply to my email” nonsense to try and keep you from calling the person directly to verify the legitimacy of the email.
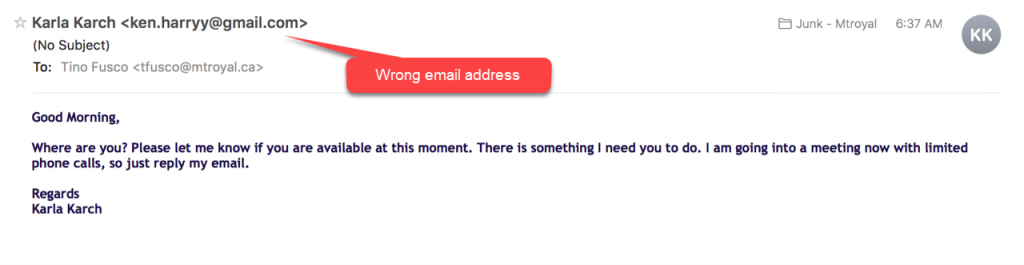
Thankfully they are still using lame sender email addresses, so they are pretty easy to spot if you take the time to look. However, they have started to use a new tactic that is concerning. They some how have gotten a hold of cell phone numbers and are now texting Mount Royal employees asking them to contact the texter immediately as they have a task for them. The messages appear to come from the employee’s supervisor.
How do you protect yourself from social engineering via text message?
- Don’t click on links in text messages
- Be suspicious of requests that are outside of regular procedures or processes
- Don’t give out information that the person you are talking to should already have
A good rule of thumb is, if it doesn’t feel right it probably isn’t. If you get a strange request from your supervisor, politely let them know you will get right back to them and hang up. Then contact them using an email or phone number that you know is legitimate.
Porn Hoax messages on WhatApp targeting kids – 09/13/18
There is a disturbing new hoax making the rounds in WhatsApp? Children are receiving messages in in the app from someone named Olivia who claims to know them, but has a new phone number. Once they establish contact, they send the child a link to porn sites. Although this is currently happening in the UK, hoaxes like this can quickly spread.
This would also be a good time to review with your child how to stay safe online, and remind them to not forward hoax messages.
60 000 Android devices infected with malware – 06/28/18
The latest malicious Android app is a clever thing indeed. So clever that it has managed to infect 60 000 devices at last count. What should you look out for? The whole process starts with a pop up that informs you that you have issues with your device. The make and model of your device is listed in the pop up making everything look very official. It gives you the option of ignoring the issues or cleaning them up by installing an app. Thing is it doesn’t matter what you click, it takes you to a power saver app in the legitimate Google Play store.
It isn’t until you look at the permissions that the app asks for during install that things seem a bit odd. Why would a power saver app need:
- to read sensitive data?
- to receive text messages?
- to pair with Bluetooth devices?
- full network access?
- to modify system settings?
- to receive data from the Internet?
If you decide to ignore the red flags and install the app anyway a few things will happen. First, a hacker completely controls your device. Second, a little ad-clicker bot runs in the background clicking on ads and generating revenue for the hacker while stealing your data. Third, the app actually does work by stopping processes that are using too much battery power when the battery level is low. So it isn’t all bad. At least the app does what it says it does. It’s the bonus features that you can do without.
If you are have a pop up on your device that you cannot close or that takes you to a web page or the Google Play Store no matter what you do, restart the device. That should get rid of the pop up. If it persists you may have to resort to a factory reset. Either way you do not have to give a hacker control of your phone to get rid of a persistent pop up.
Your customer service complaints on social media might be setting you up – 06/28/18
Most people have heard of the irate consumer that complains about a product or service on social media and is then contacted by the company who offers them something wonderful to make them happy. This isn’t just an urban legend. Many companies keep an eye out for disgruntled customers on social media so they can address complaints before they cause backlash.
Criminals are taking advantage of this by masquerading as customer service representatives. Just like the legitimate companies, they set up alerts to be notified when someone posts about a company. They then contact the disgruntled consumer with an official looking text or email containing a link that will resolve their issue.
When annoyed consumers click on the link, they get malware loaded onto their machine or device instead of getting help with their complaint . This is called Angler Phishing.
If you have a complaint with a company, I suggest that you contact them directly. If you decide to make a fuss on social media, be aware that anyone who contacts you could be a wolf in sheep’s clothing.
Adidas is not giving away free shoes – 06/19/18
From the Too Good to Be True file, comes the Adidas anniversary giveaway. Messages are currently circulating in WhatsApp promising a free pair of Adidas shoes in celebration of their anniversary. Initially messages referred to a 93rd anniversary, however the hacker decided to do some basic math and more recent messages correctly refer to a 69th anniversary.
You might be asking, why on earth would someone fall for this? Well once the scammers sorted out their math, they were clever enough to spoof the official Adidas site. The fake URL is exactly like the legitimate one with only the i replaced with a vertical line with no dot. This is an easy thing to miss when one is being tempted with free footwear.
In addition the scam is quite sophisticated. They don’t just come right out and say, give me your personal information and I will give you free shoes. Instead, they give the whole thing a legitimate feel by making the victim qualify first by answering a short survey and requiring them to share the offer with their WhatsApp contacts (just for the record, there is no way for them to determine if you have shared a message or not). Once you qualify, you are told you can claim your shoes for a dollar. Of course as payment is now required (but it’s only a dollar, so it’s nearly free), you are sent to a webpage that collects your payment card information. Having jumped through multiple hoops to claim your prize, you now feel like you have earned the free shoes and all thoughts that this are a scam are gone from your mind.
That is until you see the confirmation of payment web page that includes a line in the footer saying you will be charged $50 per month if you don’t cancel your subscription in seven days. Of course they now have your payment card information and will charge you what they want for as long as they want until you cancel the card. Even worse if you fail to read the footer, they will have access to your card until you notice the charges.
Anytime someone is giving something away, assume it is a scam. If you are tempted by the sparkly giveaway being dangled in front of you, visit the company’s website using a bookmark or search engine result. If they are giving something away, it will be advertised on their official site. Remember if it is too good to be true, it probably is.
Watch out for the Facebook video scam – 05/15/18
Facebook users around the world are being taken in by the latest video scam. They are receiving Messenger messages containing a video link. When they click on the link, they are taken to a fake Youtube web page and asked to download a browser extension so the video can be viewed. Of course when they do, they load malware onto their machine that harvests their data and then sends out the same message to all their Facebook friends.
This newest scam is just one of several that use Messenger to deliver malicious links. These links as well as those in text messages or other messaging apps should be treated the same as links in email:
- If it is from someone you know, call the sender to make sure they sent it before you click on it.
- If it is from an organization, visit their website directly to get the information.
- If you don’t recognize the person or organization, delete the message.
