Email from The Spamhaus Project is fake – 01/31/20
The latest phishing email to arrive in MRU inboxes is this beauty that looks like it comes from The Spamhaus Project, an international organization that creates block lists of spammy and phishy email senders.

This email is a bit clever as they use a link to the real Spamhaus Project website to try and convince you the email is legitimate while threatening to block your email address. Unfortunately the painfully bad grammar, zip file attachment and wrong email address clearly mark it as a phishing attempt.
You have to give them credit for trying though, if you are in a hurry and don’t take the time to read the email carefully, the odds are pretty good you will panic and click. Don’t get caught, slow down and stop and think before you click.
How cybersecurity experts become victims – 11/26/19
Every month I send out a nice little phishing training email to give our wonderful users across campus some practice identifying them. Those people that click and are repeat clickers, work in IT or are a Cybersecurity Champion all tell me the same thing. They were trying to determine whether to click or not while they were in a hurry or while they were on their phones.
The dangers of doing this were highlighted in the Our Community article, I knew I’d been scammed which details how one of Mount Royal’s community members became a victim of a gift card scam. Now KnowBe4 has written its own article describing how one of their cybersecurity professionals clicked in three phishing training emails in two months. In both cases the individuals were well educated in how to identify a phishing email but were in a hurry and using their phones. The message that keeps getting repeated is to SLOW down.
Before you decide what to do with an email, STOP. If you are on your phone, deal with it later at your workstation. If you are in the midst of doing 7 things, deal with it when you have time to evaluate it properly.
Taking theses simple steps will help keep you from becoming a victim.
Watch for payroll related phishing emails – 11/05/19
Tuesday morning was an exciting one for the security team. Over 900 inboxes received the following email.

I am delighted to report that a huge number of you were superheros and forwarded the email to abuse@mtroyal.ca. Thanks to you we were able to block the target page and limit any damage. Even though so many of you spotted the email as a phish right away, with the high number of recipients Marketing and Communications made the unusual decision to issue a campus wide alert.
While we were investigating the incident, we discovered that the attacker spent a lot of time viewing our Payroll webpage. There is an excellent chance that the attacker will use this information in the near future to create another phishing email.
We are asking everyone across campus to keep an eye out for payroll or HR related phishing emails in the next little while. If you receive an email that appears to come from HR or Payroll, please check the email address for accuracy. If it is correct, please call the sender to confirm that they actually sent the email.
Should you find the email to be malicious, do what your colleagues did this morning and forward the email to abuse@mtroyal.ca. You too can be a superhero!
Fake login pages mimic the real thing giving you no clue you have just been compromised – 10/25/19

For a while now, I have been warning about clicking on links in emails from organizations that you know. Instead, I have encouraged all of you to visit the organizations website directly using a bookmark. A report of a new phishing campaign targeting Stripe users shows why this advice is so important to take.
This campaign involves an email that tells the intended victim that there is something wrong with their account details. They are asked to login to their Stripe account to update them and given a handy button that appears to take them to the Strip login page. The page is of course a spoof and although it looks exactly like the real one, all credentials entered are collected by the thieves.
The fraudulent page is set up so that once you have entered your credentials in the fake login page, they use them to log you into your actual account. From your point of view, nothing is amiss. They now have your login credentials, you are non the wiser and they have hours if not days to withdraw funds before you even notice.
Although this campaign is targeting Stripe users at the moment, the same tactic is used to target all sorts of users. This is a gentle reminder to not click on links in emails from organizations that you know, but to use a bookmark instead. If you don’t have the site bookmarked you can use a search results, however proceed with caution as more and more fraudulent sites are appearing there.
New phishing email tactic, the found student pass – 10/17/19
Those clever cybercriminals have come up with another tactic to get you to click on something you shouldn’t. Introducing the “I found an ID pass”, phishing email.

What makes this email so diabolical, is it has no sense of urgency. In fact it asks nothing of you at all. It simply lets you know that a pass was found and it is being mailed. It’s calm, indifferent manner lull’s you into thinking the email is harmless. It counts on the reader being so curious that they throw caution to the wind and click on the link to see whose ID was found. Quite ingenious really.
If you receive an email of this sort, delete it and wait for the mail to arrive.
MRU employee checks for email legitimacy and talks to the hacker – 10/17/19
One sure fire way to avoid becoming a victim of a cyberattack is to call the email sender to verify that they in fact sent the email. That is a message that I preach over and over again all over campus. I am happy to report that my message is being heard and acted upon…sort of.
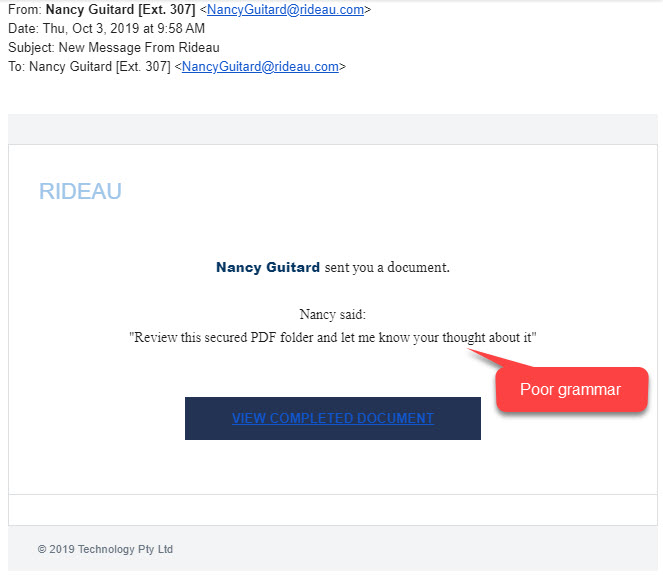
Here is the email that one of our staff received in their inbox.

The staff member knows the sender and aside from the poor grammar, the email is spot on. The attachment was indeed a Sharepoint document, so she opened it. However when she found nothing but a greeting link to another document she paused. She knew that email addresses could be spoofed and realized she should confirm the legitimacy of the email. So she sent this email.
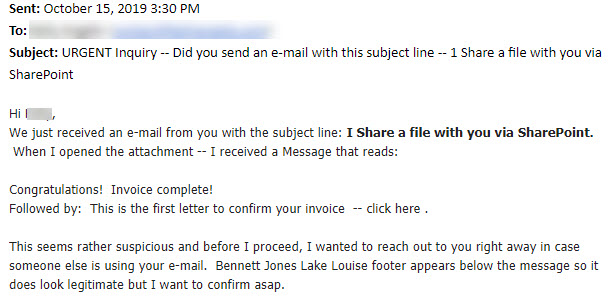
She correctly did not reply to the original email. But created a new one and sent it using an email address in her contact list. This is the reply that she received.

Before she could check the invoice, she received this email.

The sender’s email account had been hacked! It didn’t occur to our staff member that if someone else was using her colleague’s email address, it wouldn’t be her colleague who responded . She gets an A for verifying the legitimacy of the email. But she gets a F for talking to the hacker.
The lesson has been learned. When confirming email legitimacy, use the darn phone. A 30 second phone call can save you from a world of hurt.
Malicious links can hide in legitimate documents – 10/09/19
The tools that cybersecurity professionals use are getting more and more sophisticated. They can now identify a known malicious link or attachment and strip it from the email so it never arrives in your inbox. To get around that limitation, hackers are hiding their malicious links and attachments in legitimate documents. This latest attack is a perfect example of that tactic.
This one is scary in it’s precision. It was sent to only two email addresses. Both recipients have higher level network and financial access. The email looks like this
It looks innocent enough. In fact, if you check the link it goes to a Microsoft site. Clicking the link takes you here.

This is a legitimate OneNote notebook. The icons however are just pictures, not clickable links and the links below them are flagged as malicious. Had the user clicked on the link, their login credentials would have been quietly harvested.
In this type of attack, the hacker often shares or pretends to share a document with you. The email usually asks for your input and is purposely vague and low key. Should you open one of these documents and find only links to another document, close the document and contact the IT Service desk. Your quick action could save your data.
Chase Bank & Amazon phishing emails arriving in MRU inboxes – 09/26/19
A couple of extremely well done phishing emails that appears to come from Chase Bank and Amazon have appeared in Mount Royal inboxes. Interestingly enough, both come from the same email. Here is what they look like:


Criminals are getting better and better at creating emails that trick us into clicking. Remember, if you receive an email from an organization that you know, visit their website using a bookmark or search result and login to your account. You should be able to read any notifications from there. If not, you will be able to find official contact information so you can inquire about the legitimacy of the email that you received. If you find one of these nasty things in your inbox, delete it.
Fake email from Tim Rahilly arriving in spam folders – 09/18/19
This week the campus community is finding a particularly clever phishing email in their spam folders. It looks like this:

This is the third time our illustrious leader has been impersonated. Although this email is mostly landing in spam folders, I thought I should bring it to your attention in case it sneaks into an inbox or two.
Your on-the-ball colleague caught this one because they checked the sender’s email address. This is a gentle reminder to follow their lead. With all emails that ask you to take some sort of action, whether it is opening an attachment, clicking on a link or providing information, always check the sending email address BEFORE you read the email. If the email address is wrong, it is less likely your emotions will be triggered and rational thought will be by passed.
If this darling arrives in your spam folder or inbox, it can safely be deleted.
Clever Staples phishing email showing up in MRU inboxes – 09/05/19
Classes have begun and the hackers are betting that employees across campus will be ordering supplies. They have begun sending out fake order confirmations from Staples. These emails are extremely well done. Take a look.

I especially like the note at the bottom that specifically asks you to reply to the email. Just in case you are suspicious, they have given you some lovely directions that will put you in touch with them. Very clever.
The only real tell, unless you are super familiar with the email that Staples uses for order confirmations, is the View here button URL that takes you to chainetwork.club. Definitely not Staples.
As with all other emails that come from organizations that you are familiar with, visit their website directly to check orders, confirmations and payments. Do not use links in emails even if they look as legitimate as this one.
