Phishing email appearing to come from Mailchimp targeting MRU – 08/14/19
A rather clever phishing email is showing up in inboxes around campus. Take a look.

This one is so very clever as the links on the bottom are legitimate. They take you to Mailchimp’s contact info, terms of use and privacy policy. Where things get interesting is if you click on the other links. They all take you to a Google site masquerading as a Mailchimp login page. A lot of work went into this one. It is so close to the real thing that only the sender’s email address and hovering over all the links gives you any clue there is something amiss. The email itself is perfect.
This is quite admirable really, if you forget that they are trying to steal your Mailchimp credentials and your information that Mailchimp has on file. When the emails are this good it is hard know whether they are legitimate or not. The best way to deal with them is to visit the organization’s website using a bookmark or search result and check your account information that way.
Kudos to the employee who identified this bad boy and forwarded it to abuse@mtroyal.ca. If you find a nasty like this sitting in your inbox, do what your colleague did and forward it to us. We will send you a super cool sticker and give you the title of cybersecurity superhero in return.
Iranian hacker group using LinkedIn to deliver malware – 08/06/19
FireEye has identified a new phishing campaign targeting oil, gas and energy companies as well as utilities and government organizations. The rather clever criminal contacts victims through LinkedIn claiming to be a researcher at the University of Cambridge. Once contact is made, the victim is offered a job and asked to provide a resume. As part of the application process, they are also asked to go to cam-research-ac.com to download and fill out a document. Of course once they do, malware is loaded onto their computer.
What makes this campaign so concerning is the assumed legitimacy that comes with using LinkedIn to communicate with potential victims. People tend to trust the platform and therefore trust those that use it to communicate. Unfortunately, this trust is misplaced.
When you are contacted by someone you don’t know on any social media platform, treat that communication with the same skepticism as you do with any email message. Just because they say they are from a trusted organization, does not mean they are. Before you engage in conversation, call their organization and confirm that they are in fact employed there. A little homework can save a lot of headache.
Watch out for fake Equifax settlement emails – 08/01/19

Cybercriminals are sending out fake Equifax settlement emails. These emails are promising free credit monitoring and/or compensation. To make matters worse, they are spoofing the real Equifax settlement page. So if you click on the link in the email, you are sent to a very convincing web page encouraging you to file a claim. Of course, if you fill in their form with all of your personal information you are just sending your data to the criminals.
If you need to file a claim, do so by visiting the FTC website. You can find information there about the data breach and the settlement as well as a legitimate link to the Equifax site. Do not click on any links in any email that appears to come from Equifax. Visit their site directly using a browser search result or a bookmark. Everything that you need to know you should be able to find there. If not, there will be legitimate contact information you can safely use.
No, your password is not going to expire – 08/01/19
The latest phishing email to hit MRU inboxes is a classic. Check it out.
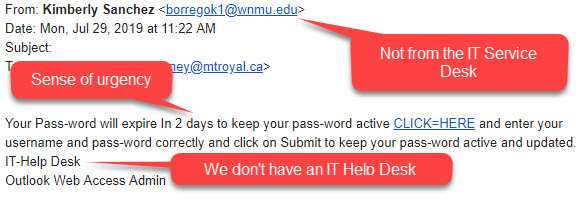
A big thank you to everyone who reported this phish by forwarding it to abuse@mtroyal.ca. You are all superheros! Should this bad boy arrive in your inbox, you can delete it as we are aware of it. However, if something new shows up please do what your colleagues have done and forward it to abuse@mtroyal.ca. You too can be a superhero!
How to create emails that don’t look malicious – 07/26/19
Communicating with everyone on campus is challenging. A lot of work goes into what information should be included, making sure the email is as succinct as possible and making it easy for the readers to act on your request. Unfortunately, we often have these emails reported as phishing emails or they are deleted by readers.
So how do you create an email that makes it easy for the reader to act without making them think you are trying to steal their data? It is a delicate balancing act. Fortunately, there are some guidelines you can follow.
First, make sure that people can verify the legitimacy of the email, by including the name of a contact person at Mount Royal that can be found in the directory. That way if someone is not sure about an email, they can just call the contact person and confirm that the email is legitimate. This is especially important if the email is coming from a third party.
Second, if you are using a tool to track who clicks on what in the email, make sure the URL that appears when you hover over the links looks like a Mount Royal URL. If you are not sure, contact the IT Service Desk and ask them for help. We can work with your tool vendor to make sure your links look legitimate.
Third, avoid including links if you can. Instead of using links, type out the Mount Royal URL or tell them where on mtroyal.ca they can find the information. Stay away from URLs that look vague, are excessively long or do not send readers to a G suite or mtroyal.ca webpage. Even better, include the relevant information in the email itself.
Fourth, do not use your personal email address for Mount Royal correspondence. Anything not coming from an official Mount Royal email address will be considered suspicious.
Next, if you are using a tool to send the email make sure that the sender’s email address appears as a legitimate Mount Royal address. If your tool does not allow you to do that, contact the IT Service Desk. We can work with most vendors to fix that.
Lastly, avoid including other phishing red flags in your email such as generic salutations, a sense of urgency, triggering emotions and asking people to do something against established procedures.
By following these simple guidelines you will greatly decrease the chances readers will report or trash your email instead of acting on it. If you are planning on sending out a campus wide email and you aren’t sure if it will get flagged as malicious or not, please contact the IT Service Desk and ask for help. We would be happy to preview the email and let you know if anything needs to be changed.
Happy emailing!!
Scammers targeting MRU are getting very creative – 07/17/19
In September last year, the first of several targeted email scams arrived in Mount Royal inboxes. Since that time we have see a plethora of these scams spread across campus. Up to now that have all been emails from a supervisor asking a report to do a favor for them.
However, we must have ended up on some “the Best People to Scam” list as this week the scams have gotten very creative. First up is a dude in Indonesia contacting Wellness Services to help him sell a helicopter (I actually think this might be legit). Second up is an email to the MRFA insisting a charge from their store has appeared on a bank statement (definitely not legit). Check out the pics!!

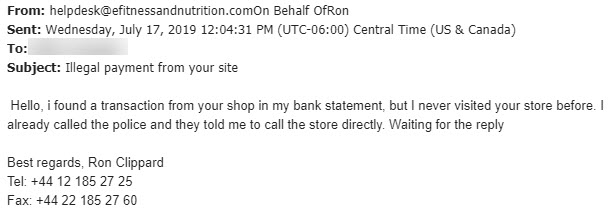
As entertaining as these emails are, that is not the reason why I am sharing them with you (well maybe a little bit). I am sharing them to give you a heads ups that MRU is being actively targeted and we all need to be on our toes. If you receive any email that is out of the ordinary, please take a closer look at it. If you aren’t sure if it is malicious, forward it to abuse@mtroyal.ca like your colleagues did and we can take a look. Everyone who reports an email gets a cool sticker. Be a superhero and report those malicious emails!
Fake benefits enrollment email arriving in MRU inboxes – 06/28/19
The following email is showing up in inboxes around campus.

This fake email is not from the IT Service Desk. Normally I would go through and show you all the things that are wrong with this email. However, as many of you have been readers for a while, I thought it would be nice to have some fun with this one.
Take a look at the email and then comment below on what you think flags this email as phishing. Next Thursday, I will go through the comments and add any that were missed. Let the commenting begin!
Is it spam or is it phishing? 05/23/19
I am truly delighted with the number of malicious emails that are being forwarded to abuse@mtroyal.ca. The Mount Royal community is doing a great job of letting us know what to look for and helping us defend their data. There is one question that people keep asking though, what is the difference between Spam and a phishing email? I thought I would take a moment to clarify.
Spam email
- Goal is to sell you something.
- It is sent to hundreds or thousands of people at a time.
- Reading the email does not generate an emotional response.
- It may or may not contain links
- Clicking on the links will take you to the organizations website.
Phishing email
- Goal is to steal your data or use your workstation as a tool to access data on other people’s devices.
- It can be sent to thousands of people or just one or two.
- Reading the email generates an emotional response.
- It may or may not contain links and or attachments.
- Clicking on the link or opening an attachment takes you to a fake web page and/or loads malware onto your device.
The easiest way to determine if what you are dealing with is spam or phishing is by examining the purpose of the email. If it looks like they are trying to sell you something, then it is probably spam. If it looks like they are trying to confuse or trick you, then it is likely phishing.
Spam emails should be marked as spam by clicking the stop sign icon in the Gmail menu bar. Phishing emails should be forwarded to abuse@mtroyal.ca. If you aren’t sure which one it is, forward it to abuse@mtroyal.ca and we can let you know.
Fake package tracking email found in MRU inbox – 05/14/19
The latest phishing attempt is quite lovely. The criminals have made it purposely vague with the hope that it will peak your curiosity. Here is what is looks like.
![]()
If you have recently ordered something online. curiosity could get the better of you. If you click the link, this is what you find.
![]()
You were promised a PDF, which is usually but not always safe to open. However, you are given a Word document instead. It’s the old bait and switch. Having navigated to this point safely, you are more likely download the document. Of course if you do, malware is downloaded with it.
Remember troops, stop and think before you click. Stay safe out there.
Another Rahilly phish making the rounds – 05/08/19
The gift card scammers are giving another go at trying to convince employees that our new president Dr. Rahilly is trying to contact them.

This time they have managed to get his name correct, replacing the much loved Tin with Tim. They have also changed up the email address going with presidant to make it look more official. Although if they had spelled it right, it would have been more effective.
This is just another attempt at a gift card scam. If you check the sender’s email address before you read the body of the email, you will be less likely to have emotion override rational thought and reply in haste. If you are contacted by the “presidant”, just delete the email.
