Must Read – Scammers pretending to be Mount Royal employees – 09/27/18
It has been a busy week. There are two phishing emails going around campus at the moment. The first one starts out rather innocently.
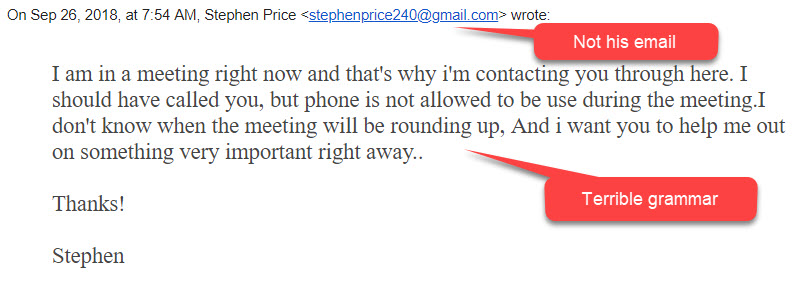
However if you respond to it, like half a dozen people did, you receive a second one.
You are probably wondering why anyone would respond to the first email. First of all the email was from a department head, so that tends to get people’s attention and generate an emotional response. Also, almost all who responded were looking at the email message on their phone. They were unable to clearly see the sender’s email address or the grammar errors. This is just another reminder as to why it is so important to wait until you get to a large screen to take action on an email. It is also a reminder to not respond to our emotions. If you read an email and are responding emotionally to it, that is your cue to pause for a minute and take a closer look.
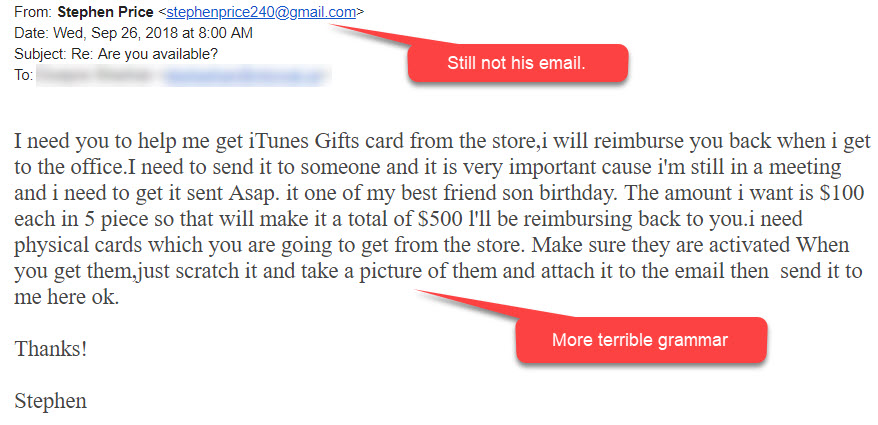
Impersonator number two is a bit more sneaky. Check out this bad boy.

I just love how they added the signature line to this one. They must have received an email from Mount Royal at some point. This is the stuff that keeps me up at night. The grammar is perfect. The content is plausible and looks legitimate. The fuzzy logo is a bit of a tell, but other than that it’s not an easy one to spot.
That was the bad news. Now for the good news. In both cases IT services was notified of the threat by Mount Royal University employees who forwarded the email to abuse@mtroyal.ca. Their quick thinking gave us a heads up right away so we could block both email addresses and prevent further attacks. They are superheros!!
Keep an eye out for these types of emails in the future. If you find one, forward it in its entirety (no screenshots please) to abuse@mtroyal.ca and you can be a superhero to!!
ALERT – Mount Royal targeted with fake Sharefile requests – 04/12/18
A college that we communicate with regularly has had one of their email accounts compromised. As a result, several people around campus have received emails with requests to Download Attachments from Sharefile. The emails look like this:

The name of the college and the email sender have been blurred out to protect their privacy.
What makes these emails so devious is that they come from someone that Mount Royal staff have been conversing with recently. This makes it much more challenging to identify them as malicious.
This is a gentle reminder to everyone to contact the email sender when you receive an unexpected email with a link or attachment using a contact number that you have used in the past or have found through Google. Even if you have been speaking with them recently if you aren’t expecting the email, call to confirm its legitimacy. Just because an email looks like it comes from someone you know, doesn’t mean it does.
That is what our brave Mount Royal employee did and as a result prevented a potentially serious cyber security incident. Had they simply clicked on the Download Attachments button and followed the instructions, they would have given the hacker their Docusign credentials. Who knows what that would have led to.
ALERT – Mount Royal staff victimized by phishing email that is a reply to an old thread – 03/26/18
Mount Royal employees are receiving emails from a vendor that are actually replies to a legitimate message. As the message is a reply and it is from someone we do business with, employees have been tricked into opening the attachment more than once putting our network at risk.
How the heck did they manage to reply to a message that the vendor had sent ages ago? Simple, the vendors email account was hacked. Once the hackers had access to the email account all they had to do was scroll through the emails in the sent folder until they found one that mentions an invoice and reply to it. Of course they attached an edited invoice containing a nice little keylogger trojan onto it first.
Those that opened the attachment found a blank document and then contacted the Service Desk to see why. The Service Desk calmly explained all their keystrokes were being recorded by malware they had unintentionally installed and then sent support staff to re-image (wipe clean and re-install) their machines.
Unfortunately this is not the first time that Mount Royal University has been targeted by this type of attack. Late last year another vendor had their email account compromised and multiple Mount Royal staff members received replies to an old meeting invite containing a document that “required their input”. That document contained malware as well and once again we were re-imaging machines.
How do you know when an email from a vendor contains a malicious link or attachment? Truthfully, you don’t. The only red flag on either of these emails was the date of the original message. The email thread was months old and was used in the attack because it contained a subject that would allow an attachment to be added to it without looking odd. However, a recent message could also have been used if it had contained the right content.
So how do you protect yourself from such attacks? You call the vendor when you receive an email with a link or attachment and confirm that they sent the email. You do not reply to the email as if their email account has been compromised, you will be conversing with the hacker. Do not use the contact information found in the email to contact the vendor either. The hacker may have changed the email signature. Use a contact number that you find in a Google search or that you have used before.
Yes, horrors, you have to actually pick up the phone and talk to a person. However, it will practically eliminate the risk of having your machine wiped clean and the operating system re-installed. Not a fun way to spend the morning.
Mount Royal Community Member gets fake CRA call – 03/09/18
One sure sign that spring is on its way…tax scammers pop up along with the tulips. Although we are a ways away from enjoying the tulips, the scammers are out in full force. One Mount Royal employee came into work to find this on his voicemail.
Click the far left of the bar to listen to the voicemail message.
Pretty nasty huh? So how to do you know this is a scam? Simple, the CRA will never phone you and threaten legal action or arrest. They will never send someone to your house to collect payment or to arrest you either. This was a voicemail, so it was easy to calmly listen to the message and analyze it to determine if it was legitimate.
What do you do if they have you on the phone and they are threatening you? The scammers can be very insistent and believable causing considerable stress and confusion. If you experience a call like that from the CRA, tell them you will call them back and hang up. You can then contact the CRA at 1-800-959-8281. If there are any issues with your taxes, whoever answers the phone will be able to address them.
Watch out for phishing emails from the CRA as well. As I mentioned in a post last year, the CRA will never email you unless you have given them previous permission to do so and they will never send you an email with links unless you have specifically requested a document.
For more information on how to identify CRA fraud and protect yourself, visit the CRA website.
Threatening voicemail left at Mount Royal – 11/21/17
Yesterday one of our staff members checked her voicemail and found a nasty message from an “Officer” Robert William asking her or her attorney to call him immediately before “the legal situation unfolds”. Our quick thinking staff member Googled the number, 905-581-1528 and discovered that it was a phone scam.
Had she called them, she would have been asked her personal information including her SIN. Armed with that info, the crooks would have applied for credit cards and loans in her name, leaving her on the hook for the payments. Only after months of paperwork and expensive legal fees would she have been able to clear her credit record and name.
This is just a reminder to never give out information people already should have, over the phone, in an email or text. If someone calls you and tells you they are from your bank, a vendor, the CRA, RCMP or Calgary Police Service:
- Ask for their name.
- Tell them you will call them back.
- Call the organization’s switchboard directly using a number that you obtain from a Google search or that you have used before.
- Ask for the individual by name.
If they insist that the only way to reach them is through a number that they give you, you know that it is not a legitimate call. If they tell you that they may not be available when you call back, you should be able to have your account or file reviewed by someone else in the same department.
Remember, no legitimate agency threatens legal action over the phone.
ALERT – Word macro virus circulating through Mount Royal University – 11/20/17
Last week I posted about a scary new phishing email making the rounds. This phishing email is hard to detect because if appears as a reply to a previous email and it comes from someone you know. The email reads as follows:
Morning,
Please see attached and confirm.
A Word document is attached to the email. If you open the email you get the following notification.

If you follow these instructions, you give Word permission to run the malicious macro embedded in the document and your machine is infected with malware. To make matters worse, it will then send out a similar email reply to select people on your contact list spreading the infection.
Several people in the Mount Royal community have already received this email and opened the attachment. Their machines were infected and are being re-imaged. We are unable to determine who will receive this phishing email next and it is too new for our anti-virus software to detect.
This is only one example of a whole family of malware that uses Word macros to infect your computer. The good news is, if you have macros disabled by default and you do not Enable Editing or Enable Content as instructed, you cannot be infected.
Some other examples of fake notifications to look out for are:
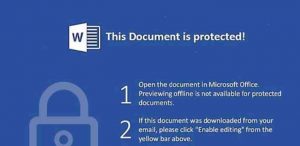
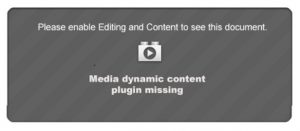



In each one of these instances, following the instructions will infect your machine with malware that could spread to friends, family and colleagues.
How to protect yourself from infection:
- Make sure Word Macros are disabled by default:
- Select File>options>Trust Center.
- Click the Trust Center Settings button.
- Select Macro Settings from the left menu.
- Select Disable all macros with notification.
- Click the OK button to exit the Trust Center Settings.
- Click the OK button to exit the Trust Center.
Note: Disabling macros in Word does not disable them in Excel and vice versa. You must change the settings in each application.
- Verify with the sender before opening any attachments.
- If you are prompted to Enable Editing or Enable Content, ignore the request. You do not need to Enable Editing or Content to view a document.
If you are unsure about the safety of an attachment, please contact the IT Service Desk. If you think you have received a phishing email, please forward the entire email to abuse@mtroyal.ca.
ALERT – Bad Rabbit ransomware attack – 10/25/17
The US Department of Homeland Security has issued an alert for the Bad Rabbit ransomware strain. It has crippled organizations in Russia and the Ukraine and has been found in the US. It is only a matter of time before it begins appearing here.
What does it do?
- It encrypts your files and extracts the login credentials for your computer.
How do I know I have been victimized?
- Your computer will start to run slowly.
- You are directed to a webpage that gives you 41 hours to pay the ransom to get access to your files or the ransom will go up.
How do you get infected?
- When visiting a legitimate website, a pop up appears asking you to install Adobe or the Adobe Flash Player.
- Downloading and installing either of these programs installs the ransomware.
What is IT Services doing to fight this attack?
- Our anti-virus is up to date.
- We are actively monitoring systems to detect any abnormal activity on the network.
What can I do to fight this attack?
- If you are prompted to download Adobe Flash Player or Adobe:
- Close the browser tab that contains the prompt.
- Open a new browser tab and visit www.adobe.com/ca.
- Search the Adobe website for the application and download it from there.
- If you are a victim, disconnect from the network immediately (pull the network cable or disconnect from WiFi) and contact the IT Service Desk at 403-440-6000.
If you have any questions or concerns, please contact the IT Service Desk.
Latest Windows update patches 62 vulnerabilities – 10/11/17
In past posts I have talked about the importance of keeping your computer up to date by shutting it down each night. This week that is more important than ever. On Tuesday MIcrosoft released its latest updates for Windows, Office and other software which includes patches for 62 different vulnerabilities.
What is so important about patching these vulnerabilities? Hackers have known about some of these for a while and have already created malware that takes advantage of them. Keep your machine secure, shut down your machines this afternoon and get your updates.
ALERT – Phone scam targeting Mount Royal University – 10/11/17
Residence Services is reporting voice mail messages are being left on their phones threatening legal action if the call is not returned. The callers are requesting banking information and are calling from a 705 area code.
If you ever receive a threatening phone call requesting banking or personal information over the phone:
- Politely inform the caller you will call the organization or institution directly.
- Hang up.
- Call the organization or institution directly using a phone number that you know is legitimate. Do not use a phone number given to you by the caller.
Remember, if the call is legitimate you will be able to contact the caller through their organization/institution general contact number. If you cannot, you know the call is a scam and can ignore it. For more information on phone scams, check out the Crime Stoppers Telephone Scams page.
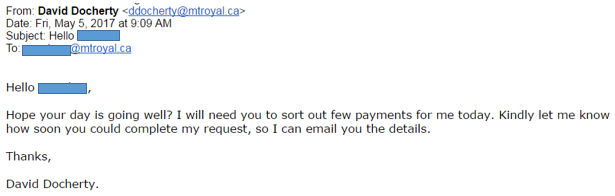
Alert – Mount Royal Target of Spear Phishing – 05/05/17
Mount Royal employees are being targeted in a new high impact email phishing campaign. What makes it so alarming?
- The email sender is David Docherty and it appears to be coming from his Mount Royal email address.
- It disguises its malicious intent by using a friendly tone and it doesn’t contain a link or attachment that usually accompanies a phishing email.
However, it should raise a red flag because normal payments are not requested this way. Take a look:
How do you protect yourself against this type of attack?
- Always pay attention when processing your emails. Do not multitask.
- Be familiar with your department’s procedures and processes. Anytime you receive an email that goes against those procedures or processes, you should contact the sender directly to confirm it’s legitimacy.
Remember, just because an email looks like it comes from someone you know, doesn’t mean it is. Just because an email doesn’t contain links or attachments, doesn’t mean it isn’t malicious.
Huge kudos to our people in Finance who identified this. You are our superheros!!
