File management when working from home – 08/25/20
I know it is hard to believe, but it has been five months since all of us were sent home to work and attend classes. Being jettisoned into a working from home environment with little preparation has its challenges. With the lines between work/school and our personal lives being blurred, it is normal for our file management to become a little chaotic. The introduction of the new VPN service in the middle of all that certainly didn’t help. I helped over 51 people transition to GlobalProtect. Now that things have calmed down a bit and it is apparent we are going to be working from home for the foreseeable future, I thought a few file management tips would be helpful.
Give everyone their own profile on shared computers
Not everyone has the ability to have a separate computer for every member of the family. Often we have to share with others in the household. By creating a separate profile for each person, you limit what they can access. To use the computer they login to their profile which is secured with a password. What applications they can use and what documents they have access to depends on which user profile they are logging into. While this doesn’t completely protect your data, it does limit the damage that can be done. You can find more information on setting up user profiles on How To Geek.
Use a different browser for work
Keeping your work/school and personal life separate is not easy when you are using the same computer for both. If you have a personal Gmail account, you have seen how easy it is to accidentally send an email to your boss/instructor with your personal email address and save that report you were working on in your personal Google Drive. Both confuse your colleagues/instructors into thinking you are a hacker trying to gain access to the network. As well it makes it difficult for you to find things.
By using a separate browser for work/school, all your work bookmarks are in one easy to find place. In addition when you send an email or save a document, it will be your Mount Royal email and Google Drive login credentials that will be auto-filled rather than your personal ones.
Save your documents in Google Drive or the MRU Network
When we are in a hurry, it is easy to click the Save button and then put that document on the default drive. Unfortunately, that is often the C: drive or your desktop. If your hard drive crashes, the files will be lost unless you back them up onto another drive. In addition, if you are an employee due for a new machine, you will lose any data stored locally. Remember, IT Services does not back anything up when they replace your machine.
Make your life easier, save files on your MRU Google Drive. If you find the Google Drive too onerous to use, download Google Drive File Stream. It will add a G: drive to file explorer allowing you to save and open documents just like you do with the C: drive. A Mac version of Google File Stream is also available.
If you don’t like using the Google Drive, you can download files from the MRU network using Webfiles. Once your work is done, don’t forget to upload them back onto the network. Remember files left on your C: drive or desktop are vulnerable. Don’t leave them there.
Limit access to shared documents to those with a Mount Royal email address.
If you are sharing documents with colleagues, instructors or students; limit who can access them by choosing to share them with those who have a Mount Royal email address or a specific email address. This ensures that even if someone outside of the University community gets a hold of the link, they cannot access the document.
If someone requests access to this document later on, deny them access and remind them to use their Mount Royal login credentials to view it. This prevents hackers who are using a generic Gmail account from impersonating a colleague, instructor or student and tricking you into giving them document access.
If you have VPN access don’t download files to your home machine
Some employees need VPN access to remote in to their MRU workstation. If you have this type of access, you are working with sensitive data. That data must stay on the Mount Royal network. Do not download it to your machine at home.
Remember to give yourself a pat on the back
We are all working in less than ideal conditions trying to deliver ideal results. I hope these tips make that a bit easier. Don’t forget to give yourself a pat on the back for doing a great job. You rock!
New Cybersecurity Awareness Training Platform is Launched 08/12/20
It’s that time of the year again. Last year’s cybersecurity awareness training is being archived and the new training program is being launched. This year we not only have a new program, but we have a brand new tool to deliver it, The Security Education Platform by Proofpoint.
Thanks to this new tool, we are able to mandate cybersecurity awareness training for all employees! While everyone has access to the online training tool, depending on your role you may be able to take a workshop to meet your training requirement. On Monday, August 17 the new training goes live!
If you have any questions about the new training platform, contact me at bpasteris@mtroyal.ca or call me at 403-440-6329.
Power outage on campus this weekend will affect remote desktop users at home – 07/14/20
Employees who are set up to use ‘remote desktop’ will need to save their work and power down their campus PCs from home 8 p.m. on Sat., July 18 for an annual maintenance shutdown. PCs will automatically be turned on the following morning at 8 a.m. Employees who are working on campus will need to power down their PCs and empty fridges of any perishables before leaving work on Friday, July 17.
We are rolling out a new VPN Service – 06/12/20
Currently, people across the University use the Pulse Secure VPN also referred to as SRAS to create a secure encrypted connection between their home machine and their MRU workstation. Unfortunately, budget constraints are requiring us to move to a more cost effective service. The new service is called GlobalProtect. The good news is, it is more powerful and easier to use.
The move from Pulse Secure/SRAS to GlobalProtect is happening in phases. Although everyone on campus who has access to Pulse Secure will also have access to the new service, you aren’t required to move over until you have received a notification with instructions on how to install, configure and use the new service.
The Working Off Campus webpage has everything that you need to know about the move and how to use the new service including user manuals and a list of FAQs. As always, you can contact the Service Desk for support.
We know that working from home is frustrating enough without having to deal with a new service, unfortunately it couldn’t be helped. We apologize for any inconvenience.
The PhishAlarm button, the best way to report suspicious emails – 09/23/2022

Updated from 05/26/2022
The PhishAlarm button is the quickest and easiest way to report suspicious emails you find in your Mount Royal inbox. However, you have to be using Gmail as your email client to have access to it. In addition, if you aren’t an employee you will see the button but will get an error message if you try to use it.

If you are using Outlook or some other application to view your emails or you aren’t an employee, forward suspicious emails to cybersecurity@mtroyal.ca.
Please don’t forward phishing emails to abuse@mtroyal.ca We can receive 114 phishing reports in a single day and it takes time to filter through them. While we won’t be ignoring emails sent to abuse@mtroyal.ca, forwarding them to cybersecurity@mtroyal.ca will ensure they are identified and responded to in a more timely manner.
To report a malicious email using the PhishAlarm button
- Open the email
- Click the PhishAlarm button in the side panel. If you don’t see your side panel, click the arrow in the bottom right hand of your screen.
- Click Report Phish. A confirmation pane appears.
- Click the X to close the confirmation pane.

Not only is the PhishAlarm button super easy to use, it sends the cybersecurity team more information about the email making it easier to investigate. It’s a win for everyone!
On a final note, the PhishAlarm button is designed to notify us of unknown malicious emails. As a result, you are unable to report emails that are in your spam folder or those that have already been marked by Google as suspicious. This saves the security team time as Google has already taken measures to ensure everyone is aware the emails are malicious so we don’t have to waste resources investigating them. Those messages don’t need to be reported and can simply be deleted.
Show off your cybersecurity prowess with digital stickers – 05/26/20

With everyone working from home, our popular sticker program no longer worked. However, we have come up with a terrific replacement…digital stickers!
Just like before you can earn the stickers by reporting phishing emails. However you can also download them from the MRU Cybersecurity Hub. Instead of putting them on your electronic devices, we are asking people to add them to the end of their email signatures. Everytime you send out an email, the recipient will get a nice reminder of how to stay cybersafe.
As before, you can still earn contest entry codes for the Cybersecurity Challenge. However instead of sending me a picture of your sticker, just send me an email requesting a code with the sticker in the signature.
Every quarter there will be a new sticker and a new code! Happy collecting!!
The online training is changing – 04/24/20
If you haven’t completed your cybersecurity or PCI awareness training for 2020 yet, you might want to do that before the end of the month. We have a new training tool that we will be introducing July 1. As a result we will be losing access to our current training videos and interactive pre-tests on April 30.
To tide us over until the new tool is rolled out, on April 29 I will be uploading new videos with quizzes. However, you will not have the ability to test out of the video and it will take longer to complete the training. I apologize for the inconvenience, however you can look forward to more targeted training once the new tool is rolled out.
The good news is, you still have a few days to complete the current version of the training. If you have any questions , please feel free to contact me at bpasteris@mtroyal.ca.
04/27/20 update: There has been some confusion around the security awareness training completion date. The deadline has not changed, you still have until June 30 to complete your mandatory training. The only difference is if you complete it before April 30, it will be easier.
Criminals are creating look-a-like MRU webpages – 04/23/20
We have been notified that cybercriminals have registered and are using the domain www.mroyalu.ca as well as several other look-a-like domains. They are attempting to fool people into visiting their malicious websites.
While working from home, it is very important that you double check all links that you receive in emails and the sender’s email address.
If the link does not have mtroyal.ca, mru.ca, mrucougars.com or mymru.ca before the first single / in the URL, it is malicious.
Examples of legitimate URLs are:
mru.ca/cybersecurity
mru.ca/wellness
https://www.mtroyal.ca/AboutMountRoyal/WhyMRU/
https://www.mymru.ca/web/home-community
Examples of fraudulent URLs are:
https://www.mroyalu.ca/AboutMountRoyal/WhyMRU/
https://www.mymur.ca/web/home-community
https://www.my.mtroyal.ca/Home
Please do not let curiosity get the better of you, and attempt to visit any of these fraudulent websites. They will harm your machine and/or steal your data.
If the sender’s email address ends in anything other than @mtroyal.ca, then it is malicious.
Examples of legitimate email addresses are:
bpasteris@mtroyal.ca
cybersecurity@mtroyal.ca
Examples of fraudulent email addresses are:
bpasteris.mtroyal.ca@gmail.com
bpasteris@mroyalu.ca
bpasteris@mtroyal.email.ca
Please be extra cautious at this time.
Updated 04/27/20
How to video conference safely – 04/16/20

With everyone working from home, video conferencing has gone from being a novelty to being a necessity. Many of you are working virtually for the first time. With new experiences come new challenges. Mistakes are being made, that is to be expected.
To help you make your video conferencing experience as safe as possible, I have found these terrific tips from SANS on how to keep your data safe and prevent accidental expose of sensitive information. With a little knowledge, you can become a video conferencing security expert. As always, feel free to share this information with your family, friends and colleagues.
VideoConferencingTips-ForAttendees-1Pager
Big yellow banner bad, sometimes – 04/15/20
Have you every opened an email and seen this?
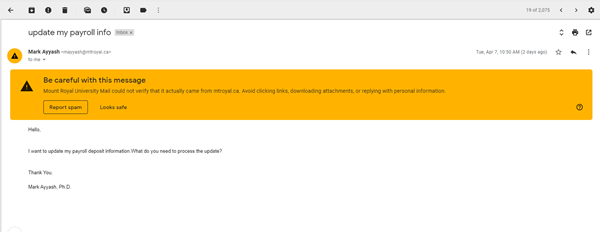
This big yellow banner is a warning that Google has identified the email as coming from outside the Mount Royal network even though it has a Mount Royal email address. This happens when someone on campus is using a cloud based tool to send out communication emails or when someone is pretending to be a Mount Royal student or employee.
We whitelist the cloud based tools used on campus to avoid getting this error on legitimate emails. However, the developers of these tools like to change things once in a while without notice. If we aren’t able to adjust the whitelist in time, this banner will show up even if it isn’t malicious.
What do you do if this warning shows up on in email? Stop and take a closer look at the email. If you have seen the exact notification or newsletter before, then it is probably a whitelisting issue. If it is from a person, then it is probably malicious. Not sure, click the PhishAlarm button or forward it to cybersecurity@mtroyal.ca.
Updated 05/29/20
