Another variation of the MRU imposter phishing email – 04/02/19
Once again miscreants are trying to catch our employees off guard by hitting them with a phishing email that appears to come from a fellow Mount Royal employee. Fortunately for us, our employee identified the odd email address and stopped the attack cold.
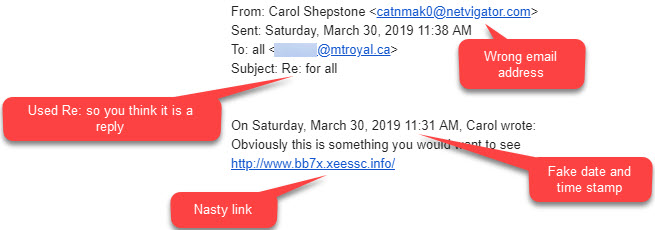
The clever criminals added some distracting details to try and trip up their intended victim. They added a Re: to the subject line plus a fake time and date stamp to make it look like the email was a reply to a previously read email. They know we tend to trust email replies and they bet that the odd email address wouldn’t be noticed. They were wrong.
Our superhero employee saved the day by forwarding this bad boy to us instead of clicking on the nasty link. Keep a look out for this one.
If it shows up in your inbox, be a superhero and forward it to abuse@mtroyal.ca.
Must Read – MRU inboxes receive malicious Google Drive file share 03/20/19
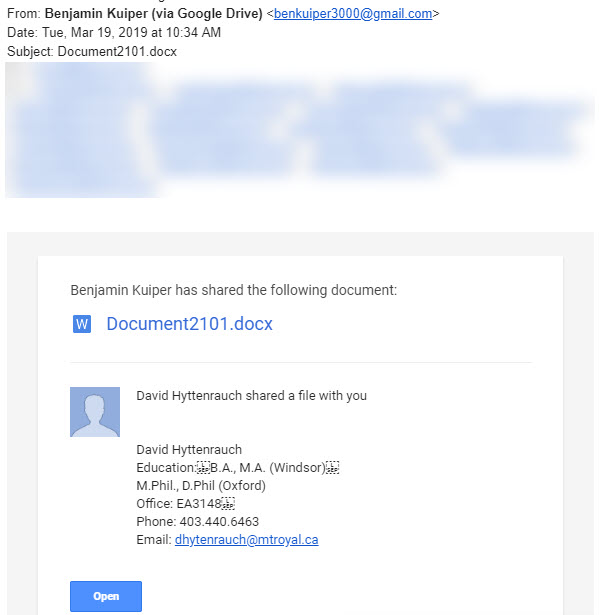
Another day, another clever criminal trying to break into our network. This time they tried using the Google Drive to do it. Tuesday morning several employees found this in their inbox.
The Word Doc link is totally legit. If you click the link, it takes you to this document.

Clicking the link in the Word document takes you to a legitimate website that has been compromised. The site asks you to login to Office 360 to access the document. Of course if you do, you are giving some miscreant your Office 360 login credentials. They can then sell your credentials on the dark web or use them themselves to wreak havoc on your data as well as the data of others. Fun, Fun, Fun.
Because the Google Drive file share and the website are legitimate, they won’t be flagged by anti-virus or the firewall. It is actually very clever. However although it may get by the technology, a person can easily spot this as malicious. In fact, we had two different reports sent to abuse@mtroyal.ca about this one. Way to go MRU!!
For those of you who aren’t already yelling at the screen, “Come on, that is so obvious”, I am going to walk you through the red flags. First one is the email is sent by Benjamin Kuiper from the email address benkuiper3000@gmail.com. Clearly not a Mount Royal email and he is not listed in the directory. Fail number one.
Second, the doc says it was being shared by Benjamin and David Hyttenrauch. This doc was sent to people on David’s team so even though they didn’t know who Ben was, they sure as heck knew who David was. This got the desired attention. However, you can’t send an invite to share one file from two people. Clearly, this Word doc was shared by Benjamin and the sneaky dude entered the rest of the deceiving information into the Add a note field in the Share with others dialog box to make it looks like Dave was involved. Fail number two.
Third, when you open the document it tells you that you have a file waiting for you on the OneDrive. OneDrive file shares are not sent with links in Word documents. Fail number three.
Lastly, if you were to hover over the link in the Word document you would see that it does not go to OneDrive. Fail number four.
As clever as criminals are, most of them can be stopped by alert employees who take the time to look at emails with links and attachments critically. As we have seen in this example, the majority of the time phishing emails contain clear clues that something is not right. Don’t get caught up in the emotion of the moment. Like our wonderful employees, take the time to really look and make sure that the email is what it appears to be. Your data, your colleagues and your IT department will thank you.
Must Read – How to print sensitive documents on public printers – 03/07/19
Just don’t. Okay, I admit I am being rather unreasonable. However if you have any other alternative to printing tax receipts, pay stubs, benefits statements and the like, please use it. We are human beings after all and we get distracted. On a regular basis our techs pick up abandoned print jobs with sensitive information that should not be on public display. Here is the latest one.

With the tax season in full swing, we are seeing a lot of these types of documents left abandoned by their owners. If you do not have any other means of printing sensitive documents other than using public printers, please take the following precautions:
- Check twice to ensure you are sending the print job to the correct printer.
- Be standing by the printer as the document is being printed.
- If the document does not print, assume you have sent it to the wrong printer and immediately look for it. Do not attempt to print the document again until you are 100% sure it has not been sent to another printer.
Taking these simple inconvenient steps will help prevent miscreants from using your student number, SIN or other personal information for their gain and your misfortune. It will also keep how much you earn from being the latest water cooler gossip.
Must Read – The MRU impersonators are ramping things up – 02/28/19
Phishing emails that appear to come from Mount Royal University supervisors are making their appearance again. This time they are throwing in the whole, “I am going into a meeting with limited phone calls, so just reply to my email” nonsense to try and keep you from calling the person directly to verify the legitimacy of the email.
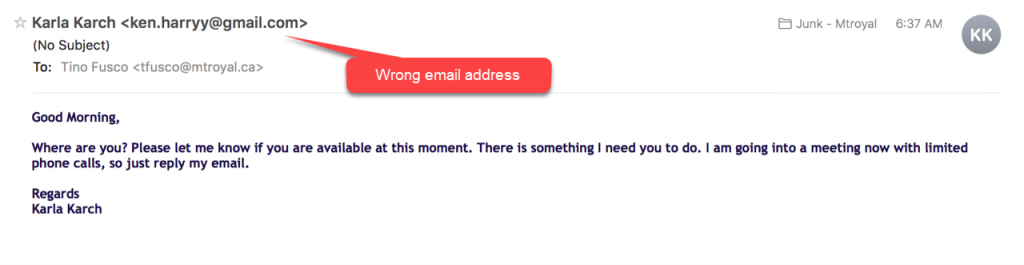
Thankfully they are still using lame sender email addresses, so they are pretty easy to spot if you take the time to look. However, they have started to use a new tactic that is concerning. They some how have gotten a hold of cell phone numbers and are now texting Mount Royal employees asking them to contact the texter immediately as they have a task for them. The messages appear to come from the employee’s supervisor.
How do you protect yourself from social engineering via text message?
- Don’t click on links in text messages
- Be suspicious of requests that are outside of regular procedures or processes
- Don’t give out information that the person you are talking to should already have
A good rule of thumb is, if it doesn’t feel right it probably isn’t. If you get a strange request from your supervisor, politely let them know you will get right back to them and hang up. Then contact them using an email or phone number that you know is legitimate.
Must Read – Check the email address before responding to an email – 02/06/19
Once again Mount Royal inboxes are receiving emails from scammers impersonating Mount Royal employees. The email appears to come from a colleague and asks if the recipient is available. If the recipient responds, the scammer then asks for gift cards.
These emails are easy to identify as the email address is not a Mount Royal email address. Thing is, people are in such a rush these days they don’t bother checking it. They see the name of their colleague and respond.
While responding to the scammer is not necessarily risky, it does encourage them. They now know that you don’t check email addresses. Next time they may be a bit more clever and include a malicious link or attachment.
When reading any email, the first place your eyes should go is to the email address. If it doesn’t match the sender’s name, delete the sucker immediately. You don’t even have to read it. It is easy, it saves you time and it will make your IT department very very happy.
Must Read – Hard to detect MailChimp phish hits MRU 01/15/19
The latest phishing attack to hit inboxes on campus is absolutely diabolical. It looks 100% legitimate and contains legitimate looking links. In addition, the technique the clever criminals are using by-passes our protective measures preventing us from keeping it out of inboxes. If we block it, we block all MailChimp emails.
Lets take a closer look at this bad boy.

Pretty impressive isn’t it? What is even more impressive is hovering over the links displays Mandrill.com which is MailChimps legitimate tool for tracking clicks, dealing with payments and account settings etc. However, if you click the link you get sent to:
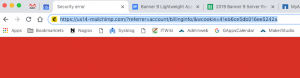
While us14-mailchimp kinda looks legit, it is the wrong URL for MailChimp. However, the page looks like a MailChimp login page. We didn’t follow along further to see what happens after you enter your username and password. However, we are pretty sure the next page would be asking for credit card information. The crooks are pretty darn smart. If you login and then get wise and not enter your credit card information, they still get access to your MailChimp account which they can use to send out more phishing emails to other unsuspecting users. It’s brilliantly done.
As smart as the hackers are, Mount Royal employees are smarter. This email was forwarded to abuse@mtroyal.ca by one of our own. That’s right, one of our own employees tagged this bit of nastiness. I couldn’t be prouder! They didn’t recall having a paid MailChimp account and recognized that the sent email address was off.
So how do you protect yourself from an attack this well executed? Do what your colleague did, don’t click the links in the email. If you have a MailChimp account, login to it directly using a bookmark or search result. If there is a problem with your account, the information will be available there. If everything turns out to be in order, you know the email is a phish. Forward it in it’s entirety to abuse@mtroyal.ca and your work as a cyber security superhero is done!
Must Read – They’re back and this time they’re impersonating David Docherty – 12/12/18
The MRU impersonators are at it again. Apparently they didn’t get bites just pretending to be a supervisor so they have upped their game. Their third attempt uses an email that appears to come from Dr. Docherty himself.

As with the other attempts, if you respond to this email you are asked to purchase gift cards. This is just another reminder to check the sender’s email address when you find yourself responding emotionally to an email.
How we get notified of an account breach – 11/23/18
Not every hacker makes their money by breaking into accounts and stealing funds or ransoming your data. Some hackers are content to simply break into servers and steal usernames. passwords and other personal information that they then sell on the dark web. It is quite a niche business.
To combat this evil, an enterprising fellow name Troy Hunt created a tool that scans the dark web looking for stolen data that is for sale. You can access this information for free at have i been powned. Simply visit the website and enter your email address. It will tell you if any of your accounts using that email have been breached.
This gives you the opportunity to change your password and username or delete the account. This is an easy process if you don’t reuse passwords. It is a huge headache if you do. What’s even cooler, you can subscribe to an alert service so they will automatically notify you when there is a new account breach. This is so awesome, Mount Royal even subscribes.
We get notified when anyone with an @mtroyal.ca email is involved in a breach. We also get told which account was breached. We are aware that password reuse still happens. By being notified of breaches we can make sure our users change their passwords so hackers cannot use their accounts to gain access to the network.
So if you are using your @mtroyal.ca account to sign up for the adult furry website High Tail Hall, we will know about it. To make matters worse, we have to contact you to let you know about the breach. It gets awkward for everyone.
This is a friendly reminder, only use your @mtroyal.ca email account for business. IT Services thanks you.
Must Read – You are our first line of defense – 11/15/18
As part of our phishing training program, I visit repeat clickers and analyze their business processes to determine why they are having difficulty identifying phishing emails. An interesting trend is appearing. Time after time, I hear people say that they thought IT Services had tools that filtered out all malware so anything that reached their inbox was safe to click.
I am going to set the record straight. There is no anti-virus, anti-malware or other type of software or technology that can identify all malware or malicious links. While IT Services has wonderful tools that help them stop most attacks, they cannot stop everything. Every organization is vulnerable to new strains of malware and hundreds of new strains are developed every day. Whether at work or at home, you cannot rely on anti-virus/anti-malware to protect you 100% of the time.
You are our first line of defense. If you avoid clicking or opening something that you shouldn’t, the odds of being victimized decreases exponentially. Simply by pausing when you are triggered emotionally by an email or when an email contains a link or attachment, you can reduce your chances of a cyber attack by 75%. We can’t do it alone, we need your help. Join us in the fight against cyber crime, stop and think before you click.
Must Read – Phishing emails are targeting educational organizations – 10/26/18
A new type of phishing email is making the rounds. This one targets the employees of a specific educational institution and appears to come from the president. It includes the right signature line and logo to enforce the deception. Subject lines of the emails include:
- Codes of conduct
- Ethical standards
- Proper workplace behavior
- Rules governing conflicts of interest
The emails tends to announce new policies around employee conduct or discusses the renewed focus on ethical professional behavior. They look something like this:

They include an attachment that when opened, takes the employee to a web page that look like a legitimate login page. What makes this one truly diabolical is once the login credentials are entered, the employee is taken to a legitimate website so they think nothing is amiss.
This is a great time to remind everyone to confirm the legitimacy of emails containing links or attachments that they are not expecting. As criminals can now make it look like an email is coming from someone our know, right down to the correct email address, there is no way to tell if an email is a phish or not unless you contact the person who appears to have sent it.
