Must Read – Mount Royal targeted with pdf containing malicious link – 03/25/19
The last few weeks there are been an unusually high number of targeted attacks on post secondary institutions. The latest phishing email shows a continuation of the trend. The email that arrives in your inbox looks innocent enough.

Innocent enough if you don’t notice the totally wrong email address. For fun, lets pretend that you did indeed ignore the email address and opened the attachment. You are presented with this document.

Once again the crooks are using a malicious link in a legitimate document to bypass the firewall and antivirus. Clicking the Open button takes you to a compromised website. As our firewall recognizes the malicious URL, I can’t tell you what awaits as the site is being blocked. However, from the email content I assume you will be given a fake login page for Outlook or OneDrive designed to steal your credentials. This is just a gentle reminder to check the sender’s email address before you click on a link or open and attachment.
Must Read – MRU inboxes receive malicious Google Drive file share 03/20/19
Another day, another clever criminal trying to break into our network. This time they tried using the Google Drive to do it. Tuesday morning several employees found this in their inbox.
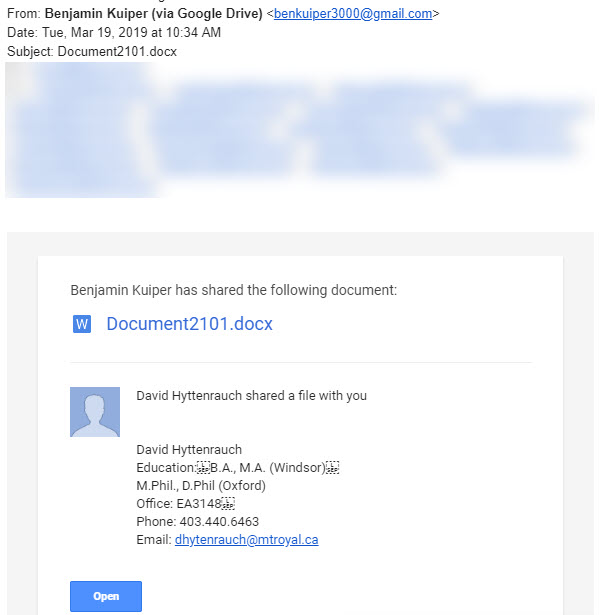
The Word Doc link is totally legit. If you click the link, it takes you to this document.

Clicking the link in the Word document takes you to a legitimate website that has been compromised. The site asks you to login to Office 360 to access the document. Of course if you do, you are giving some miscreant your Office 360 login credentials. They can then sell your credentials on the dark web or use them themselves to wreak havoc on your data as well as the data of others. Fun, Fun, Fun.
Because the Google Drive file share and the website are legitimate, they won’t be flagged by anti-virus or the firewall. It is actually very clever. However although it may get by the technology, a person can easily spot this as malicious. In fact, we had two different reports sent to abuse@mtroyal.ca about this one. Way to go MRU!!
For those of you who aren’t already yelling at the screen, “Come on, that is so obvious”, I am going to walk you through the red flags. First one is the email is sent by Benjamin Kuiper from the email address benkuiper3000@gmail.com. Clearly not a Mount Royal email and he is not listed in the directory. Fail number one.
Second, the doc says it was being shared by Benjamin and David Hyttenrauch. This doc was sent to people on David’s team so even though they didn’t know who Ben was, they sure as heck knew who David was. This got the desired attention. However, you can’t send an invite to share one file from two people. Clearly, this Word doc was shared by Benjamin and the sneaky dude entered the rest of the deceiving information into the Add a note field in the Share with others dialog box to make it looks like Dave was involved. Fail number two.
Third, when you open the document it tells you that you have a file waiting for you on the OneDrive. OneDrive file shares are not sent with links in Word documents. Fail number three.
Lastly, if you were to hover over the link in the Word document you would see that it does not go to OneDrive. Fail number four.
As clever as criminals are, most of them can be stopped by alert employees who take the time to look at emails with links and attachments critically. As we have seen in this example, the majority of the time phishing emails contain clear clues that something is not right. Don’t get caught up in the emotion of the moment. Like our wonderful employees, take the time to really look and make sure that the email is what it appears to be. Your data, your colleagues and your IT department will thank you.
Must Read – They’re back and this time they’re impersonating David Docherty – 12/12/18
The MRU impersonators are at it again. Apparently they didn’t get bites just pretending to be a supervisor so they have upped their game. Their third attempt uses an email that appears to come from Dr. Docherty himself.

As with the other attempts, if you respond to this email you are asked to purchase gift cards. This is just another reminder to check the sender’s email address when you find yourself responding emotionally to an email.
Must Read – Iranian Hackers are trying to steal university research – 08/31/18
Iranian hackers are sending out phishing emails that appear to come from within a targeted university. The emails contain a link and urge the recipient to sign in to an internal resource, the favorite being the library system. The link is to a fake login page that records login credentials.
The hackers appear to be trying to steal research data. The campaign is world wide with over 16 universities targeted and over 300 fake websites created. Canadian universities are among the targets.
If you receive an email asking you to login to one of our internal resources, do not click on any links in the email. Instead, access that resource using a bookmark or a link on www.mtroyal.ca. You can also contact the department in charge of that resource and ask them if they sent out an email. Pay special attention to emails asking you to login to the library system.
If you are unsure of the legitimacy of any email, you can forward it to abuse@mtroyal.ca and IT Services will be happy to investigate for you.
When a stranger calls, it may not be who you think – 07/19/18
Have you checked on the computer? *Tech support scams are the bread and butter of many criminals organizations. The latest version is rather creative. It starts with you clicking on something you shouldn’t which installs malware on your machine.
The malware waits for you to type “bank” in the browser. When it sees you going to your banking login page, it redirects you to a fake banking web page that records your credentials while you try to login. It then slows your computer down making you think there is something wrong with it. Then a pop up conveniently appears telling you that you have a technical problem and asks you for your name and phone number so tech support can call you.
Surprise, a real life bad guy calls and tries to manipulate you into giving them more information so they can immediately transfer money out of your account. It is a rather slick scam. You would admire them if they weren’t stealing money from you.
This is just another reminder that no legitimate tech support company will ever call you or prompt you to call them. If you get a 1-800 number, are offered technical assistance without asking for it or have someone call you to offer help; the stranger is there to help themselves, not you.
*I am hoping you get the reference. If not, this will help.
Source : https://blog.knowbe4.com/alert-there-is-a-new-hybrid-cyber-attack-on-banks-and-credit-unions-in-the-wild?utm_source=hs_email&utm_medium=email&utm_content=63936946&_hsenc=p2ANqtz–Lu3QkGYcRkjzH-KDpYeGQLy41mfHaS4MgK7rbDIoBHwAw0BrbU5HwxlZAioadMBoGis9xB0uePy8yw7mUMBwXdMNC9Q&_hsmi=63936946
Your customer service complaints on social media might be setting you up – 06/28/18
Most people have heard of the irate consumer that complains about a product or service on social media and is then contacted by the company who offers them something wonderful to make them happy. This isn’t just an urban legend. Many companies keep an eye out for disgruntled customers on social media so they can address complaints before they cause backlash.
Criminals are taking advantage of this by masquerading as customer service representatives. Just like the legitimate companies, they set up alerts to be notified when someone posts about a company. They then contact the disgruntled consumer with an official looking text or email containing a link that will resolve their issue.
When annoyed consumers click on the link, they get malware loaded onto their machine or device instead of getting help with their complaint . This is called Angler Phishing.
If you have a complaint with a company, I suggest that you contact them directly. If you decide to make a fuss on social media, be aware that anyone who contacts you could be a wolf in sheep’s clothing.
Adidas is not giving away free shoes – 06/19/18
From the Too Good to Be True file, comes the Adidas anniversary giveaway. Messages are currently circulating in WhatsApp promising a free pair of Adidas shoes in celebration of their anniversary. Initially messages referred to a 93rd anniversary, however the hacker decided to do some basic math and more recent messages correctly refer to a 69th anniversary.
You might be asking, why on earth would someone fall for this? Well once the scammers sorted out their math, they were clever enough to spoof the official Adidas site. The fake URL is exactly like the legitimate one with only the i replaced with a vertical line with no dot. This is an easy thing to miss when one is being tempted with free footwear.
In addition the scam is quite sophisticated. They don’t just come right out and say, give me your personal information and I will give you free shoes. Instead, they give the whole thing a legitimate feel by making the victim qualify first by answering a short survey and requiring them to share the offer with their WhatsApp contacts (just for the record, there is no way for them to determine if you have shared a message or not). Once you qualify, you are told you can claim your shoes for a dollar. Of course as payment is now required (but it’s only a dollar, so it’s nearly free), you are sent to a webpage that collects your payment card information. Having jumped through multiple hoops to claim your prize, you now feel like you have earned the free shoes and all thoughts that this are a scam are gone from your mind.
That is until you see the confirmation of payment web page that includes a line in the footer saying you will be charged $50 per month if you don’t cancel your subscription in seven days. Of course they now have your payment card information and will charge you what they want for as long as they want until you cancel the card. Even worse if you fail to read the footer, they will have access to your card until you notice the charges.
Anytime someone is giving something away, assume it is a scam. If you are tempted by the sparkly giveaway being dangled in front of you, visit the company’s website using a bookmark or search engine result. If they are giving something away, it will be advertised on their official site. Remember if it is too good to be true, it probably is.
Hackers using calendar events to deliver malicious links – 05/23/18
Hackers have discovered a new way to deliver malicious links, through your Google calendar. How? Simply by creating a calendar event and inviting you.
By default when you are invited to a Google calendar event, the event appears in your calendar whether you have responded to an invite or not. The sneaky hackers know that if you receive an email with an invite from someone you don’t recognize, the odds are great that you will simple delete it or ignore it. So, they create an event with a vague description and include a link to the meeting agenda but choose to not email the guests.
What the hackers hope is days or weeks later when you receive a meeting notification or see the event sitting in your calendar, you will think you have forgotten about a meeting and will open up the event and click on the link to view the agenda. I know what you are thinking, I wouldn’t fall for that because I would check the meeting owner’s email. Ideally that is exactly what you would do, however when humans think they have messed up they tend to panic and click.
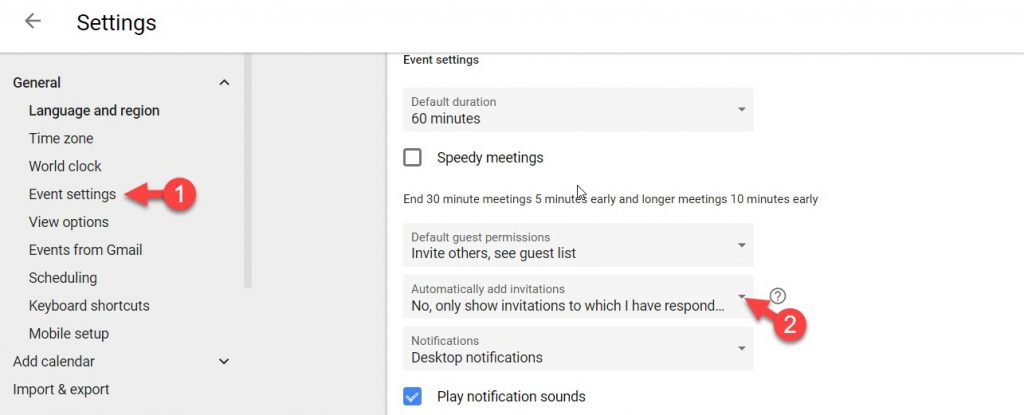
How do you protect yourself from the panic and click? You can change your event settings on your Google calendar. Go to Settings and select Event Settings. In the Automatically add invitations section, select No, only show invitations to which I have responded. This prevents events from being added to your calendar without an email invite so you can’t be ambushed.
Hackers capitalizing on GDPR policy updates – 05/15/18
Airbnb customers were the first reported targets for the GDPR policy update scam. However, hackers are now expanding their targets to include pretty much everybody. As organizations update their privacy policies to meet GDPR requirements, emails are being sent out to their account holders to notify them of the changes. Mixed in with these legitimate notifications are more and more fake requests to accept new privacy policies.
This is just one more reminder to bypass links in an email and visit an organization’s web site directly using a URL that you know is legitimate whenever you are being asked to confirm anything. If you visit the web site and there is no notification, congratulations you have just dodged a cyber attack!
Airbnb phishing attack using GDPR regulations as the hook – 05/07/18
With May 25 around the corner, the entire world is panicking about how the EU’s General Data Protection Regulation (GDPR) will affect them. Hackers are taking advantage of the confusion to send Airbnb customers phishing emails asking them to accept new privacy policies based on the GDPR regulations. They are told that they are not able to make further bookings until they do so.
This is a reminder to visit an organization’s website using a URL that you have bookmarked or find with a Google search, when you receive an email with a link or attachment in it. Any information that you need you will be able to access from their website. If you cannot find the information, the website will have a legitimate contact number listed that you can use to call them. Under no circumstances should you ever click on a link in an email from an organization or company.
