Credential harvesting emails are hitting the campus hard. Here is how to protect yourself – 02/05/2024
What is credential harvesting?
Credential harvesting is a time honored hacking technique. Attackers send you an email that looks like a document share or they send an attachment with a document that contains a link. When you click on the link, you are asked to enter your login credentials to view the document. When you do, the attackers takes your credentials and sells them on the dark web or uses them for their own purposes. Either way, you have been compromised.
Credential harvesting red flags
Fortunately, there are some red flags that you can look for:
- The Fake Document Share – The email says that they are sharing a document with you, but the sending email address does not belong to a file sharing service like Google, Onedive or Dropbox. Check for look-a-like domains like googldriv.com and dr0pbox.com as well as the use of a personal email address.
- The ChatGPT Composed Email – If the grammar and spelling are correct but the language is odd, then you might be looking at an email created by ChatGPT. For example, the email says there is an attachment but gives you a link instead.
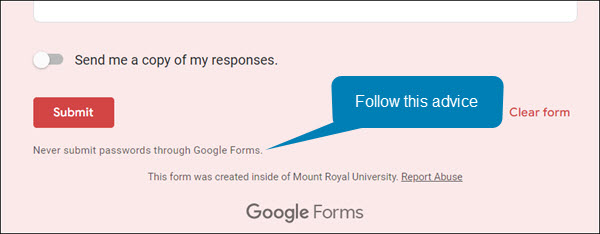
- The Google Form Credential Capture – If you access a shared document or click a link and it is a Google Form asking for your login credentials, close the form and report the email. Google Forms are easy for the attackers to set up, they come from the right domain and they don’t trigger anti-malware tools. This makes them an attackers favourite. Google forms are easy to identify, the bottom of the form is labeled.
How to protect yourself
While looking for red flags can help, attacks are becoming so sophisticated that sometimes it is hard to find them. However, there are some things that you can do to protect yourself. If the email comes from someone at MRU and a personal email address has been used, you can send them an email to their MRU email address and verify it’s legitimacy. If the email comes from someone outside of MRU, it is best to call them on the phone and ask if they are trying to share a document with you.
The good news is you don’t have to confirm every document share that comes your way, just the ones that come out of the blue or seem odd. If you do fall prey and enter your credentials, quick action is essential. Email cybersecurity@mtroyal.ca immediately. We will walk you through next steps. Please don’t just change your password and get on with life.
Depending on the type of attack used, a keylogger may have also been installed on your machine. If you contact us, we can properly assess the situation and let you know if your machine needs to be reimaged. Otherwise, you will keep changing your password and they will keep stealing it.

