Keep your devices updated with the latest security patches – 01/21/21
With criminals constantly coming up with new ways to hack into our systems, keeping your devices updated with the latest security patches is more important than ever. When you are on campus keeping your workstation up to date and secure is easy. Shut down your machine at the end of the day Friday and start it up Monday morning. However once you are working from home and your computer is always on keeping your machine updated isn’t so straight forward.
If you are remoting in to an MRU workstation you can’t shut it down. Instead, logout of the workstation and disconnect from GlobalProtect at the end of each work day. The updates are downloaded in the background as you work. Once you log out, your workstation is automatically restarted to install them.
If you have an MRU laptop assigned to you, it is setup to automatically download updates as you work. Once the updates are downloaded you are prompted to restart your machine to install them. As long as you don’t ignore the prompts, you are good to go. If you choose to ignore them and call the Service Desk for support, you won’t be helped until you restart your machine.
If you are using your personal computer, make sure you have automatic updates enabled on Windows/Mac OS and all your applications. From the Windows Start menu, select Settings>Updates and security to check your Windows update settings. On a Mac, select System Preferences>Software Update and click the Automatic Updates checkbox. Just like MRU laptops, updates are downloaded in the background and you are asked to restart your machine to install them.
Once you know what to do, installing your security patches is pretty easy. While it can be annoying, it is well worth your time. With a little bit of effort you make it exponentially more difficult for attackers to compromise your data and mess with your life.
Is the etransfer notice from MRU malicious or legit? – 12/07/20
This past year, Student Fees began issuing refunds through Interac e-transfers. Although students are notified in advance that a refund is coming, there is still some confusion about the legitimacy of these emails.
A sure fire way to ensure the refund is legitimate is to login to MyMRU and check your account balance. If you have been issued a refund, the amount will be posted there. If it matches the amount in the notification email then you know the e-transfer is legitimate.
If you are still not sure, you can email Student Fees at studentfees@mtroyal.ca and ask them if they sent you an e-transfer.
Password Managers, myths and misconceptions – 12/09/20
Now a days it seems like no matter what you do online, you need to create an account. With all those accounts comes the impossible task of remembering all those passwords. It is understandable why many of you (71%), are reusing password across multiple accounts. Unfortunately, password reuse leaves you vulnerable to credential stuffing.
So how do you create dozens and dozens of strong, unique passwords? The answer is use a password manager. A password manager generates, stores and autofills passwords for you. It saves you time as well as your sanity while ensuring your accounts are secured. It is a win, win. So much so that 73% of security experts use one.
Unfortunately, there are a lot of misconceptions around password managers. As a result, only 24% of non security experts choose to use one. Most of the reluctance is around convenience and security. It is generally thought that password mangers are too cumbersome to bother using and they aren’t secure anyway. Both of those assumptions are incorrect. I am going to set the record straight by debunking common password manager myths.
Myth #1 – Password managers aren’t secure
While no application is 100% secure, the odds that a password manager would be hacked is less than the odds that the sticky on your monitor will be read. Password managers store passwords in an encrypted file that can only be unencrypted by the password used to login to the password manager. If a hacker gains access to your password file but doesn’t have the password for it, all they will see is a jumbled mess. So unless you reuse the password for your password manager or use a weak password, the rest of your passwords should remain secure.
Myth #3 – Letting my browser save my passwords is just as secure as a password manager
Unless your browser requires you to enter a separate password to access passwords it stores then no, it is not secure. Your passwords stored in your browser are linked to your browser account. That allows you to take them with you from one device to the next. However if you forget to logout of your browser on a shared device, the next person who uses the device will have access to them. It is frightening the number of laptops that have been returned to the library displaying the last user’s passwords.
Myth #4 – Password managers are inconvenient to use
Every password manager has different features and works a little bit differently. If you find one that doesn’t work for you, try another. Almost all of them allow you to try them out for free for 30 days. Once you find one that you like, you will find that it actually saves you time and effort. You don’t have to wrack your brain to come up with strong, unique passwords anymore, the password manager does that for you. You don’t have to enter in your login credentials anymore, most password managers do that for you. You don’t have to sort through stickies to find the right password, the password manager finds it for you. You get the idea, all the annoying things you used to have to do to login to an account, website or application are done by the password manager. It makes life so much easier.
So there you have it. Password managers are secure, safer than using your browser and convenient. Most of all they make it easy for you to have a different password for every account. Now you just have to decide which one to use. KeePass is free to download and it is on all MRU workstations. However there are other web based tools that are a bit easier to sync between your devices. You can find a list of them on PC Mag’s website. I suggest that you take a look at them, compare features and pricing and then choose one or two to try for 30 days.
Unfortunately, IT Services does not reimburse you if you purchase a password manager. However, most are very affordable and can be used by your whole family.
The annual cybersecurity survey – 12/03/20
This week you will have received an email asking you to complete the cybersecurity survey for 2020. This annual survey lets us know what the MRU community has learned over the past year and helps us determine the direction and focus for the year ahead.
This year the survey is being administered through the Security Education Platform. This allows us to more easily analyze the data that we collect. The survey appears in your assignment list. Although it looks like an assessment, it is not. Completion is voluntary. No one sees the individual results except the IT security team and the data will be anonymized for reporting purposes.
We want to know what your cybersecurity habits are as well as what you know. The goal is to determine if the information and tips we are giving you are helping you practice cybersafe behavior or if we need to approach things differently to provide you the support that you need. As a thank you for helping make the program better, everyone who completes the survey by December 21, 2020 receives two contest entry codes into the Cybersecurity Challenge draw for a $250 Best Buy gift certificate.
Not sure an MRU email is legit? Contact the sender. – 12/02/20
With phishing attacks on the rise and everyone being vigilant sometimes legitimate communications are flagged as suspicious. This week we had a student report their e-transfer refund notification. Last month it was Cybersecurity Awareness Month notifications and the month before that it was a survey. While I am absolutely delighted that people are erring on the side of caution, I thought I would share a little tip that might make it easier to determine if a communication is official or not.
Without exception, official communications include who to contact if you have questions. There may not be a name but there will always be a department or email. Senders know that you may have questions and in true Mount Royal University fashion, we want to be able to help. If you are not sure if an email is legit, look for that contact information. Take note of it and then search the Mount Royal website or directory to find an email that either matches the one in the message or is for the department that sent the email.
Once you know you have legitimate contact information, create a new email asking for verification that the email is official. It only takes a couple of minutes and it will get you an answer faster than if the IT security team does the same thing.
Note that I am not telling you to use the links in the email to contact the sender. That is because some emails are sent using services and the URL for the links take you to that service before you are sent to the final destination rather than directly to the intended URL. This makes it difficult to determine if the links are legit or not. To be on the safe side, just create a new email to contact the sender for verification.
I am hoping that my little tip, will empower some of you and make you feel more in control of your inbox. That said, we will always be happy to have you report those emails that you just aren’t sure of. Keep up the good work!
An easy way to see if your Google Drive files are findable by others – 11/03/20
Documents in Google Drive can just be shared or shared and findable. A shared document is one that you are giving a specified person or group of people access to. If you don’t have the link to the document or the document isn’t shared exclusively with you then you can’t access it. In other words you have to specifically been given permission to see the document.
A findable document is one that anyone with an @mtroyal.ca email address can search for. All they need to do is enter a term in the search field in Google Drive and Google will find all the documents that contain that term in the filename or contents. Therefore they don’t need to have the link to access the document, they can just search for it.
Currently, the option to make a document findable is buried in the settings wheel that is only accessible when you want to generate a document link that can be used by members of the Mount Royal University group.

This makes it difficult to accidentally make a document findable. However, a few years ago this option was part of a drop down that included other sharing permissions. This made it much easier to select it when you didn’t intend to. The good news is, only MRU community members can search for the document. The general public cannot. So if you accidentally made the document findable, you are somewhat protected.
Now for more good news. While there is no easy way to determine which documents have been shared. There is an easy way to determine which of your documents are findable, just type owner:me source:domain in the Google Drive search bar and press Enter on your keyboard. It will bring up all the documents that you own that are marked findable. As a document can’t be findable unless it is shared with the whole campus, this should help you track down some of your accidentally shared documents and folders as well.
You are welcome!
Issues with the PhishAlarm button? Clear your cache – 11/03/20
This week the phishing training program resumed. This gave everyone a chance to use the new PhishAlarm button to report the suspicious emails. For most of you, it worked great!. For some of you, not so much.
As the PhishAlarm button is a browser based tool (it works through your web browser), it can act up when your browser acts up. This is true for all browser based tools. When this happens it can usually be remedied by clearing your cache.
Your cache is where images and content are downloaded and stored. Your browser does this to save time loading a web page. The first time you visit it, it will load some key information into your cache. The next time you visit that page, instead of downloading it from the internet again, it goes to the cache and loads it from there. This makes the webpage load much faster. This is true whether the page is a just a boring website or a web based application.
So the next time the PhishAlarm button gives you an error message or any other web based application gives you trouble, clear your cache. It will empty all the information stored there and download it from the Internet again. This basically resets the application and it usually starts working. For details on how to clear your cache, check your browser’s help files.
Happy Reporting!!
Check the sharing permissions on your files stored on the Google Drive – 10/21/20
With the move to working from home, many of our business processes have changed. For example, documents that we used to save on the J: drive have had to be moved to the Google Drive to ensure everyone has access to them. However unlike the J: drive where everything saved on it is viewable only by your colleagues in your department, the Google Drive allows you to share a single file or a whole folder with anyone. To quote Winston Churchill
Where there is great power there is great responsibility…
It has come to our attention that many of you are struggling with this power. We have found there are many documents sitting in the Google Drive that are viewable by anyone with a Mount Royal email address that really shouldn’t be. Submitted student assignments, job offer letters and lecture recordings are just some of the documents that are viewable by the entire MRU community.
We appreciate that you are doing the best that you can with what you have. We have all been thrown into a working situation that none of us were expecting. In the middle of which, Google decided to change its file sharing dialog box. So even if you were familiar with how to share files, you have had to relearn it. Throw in Shared Drives and it is no wonder so many documents are viewable by the wrong people.
If you have read this far and are thinking, “I know how to share files, I am sure that no one has access to them who shouldn’t”, please take a moment to check the sharing permissions on your files that contain sensitive information. As I said before, Google has changed their Sharing dialog box and we have oodles of sensitive documents that are viewable by the whole campus. You may think that your documents are secured, but they may not be. Don’t assume, check.
If on the other hand you have read this far and tears of frustration are streaming down your face, I come with a message of hope. File sharing is easy once you understand a few key concepts.
The Google Drive is one massive server
When you save or create a document on the Google Drive, you are placing it on a huge server that the whole world has access to. You only see the files and folders that you have been given permission to see. By default that is all the files and folders you create. The same is true for anyone else who uses Google Drive. So when you create or save a document to the Drive, is it unviewable by anyone except you until you share it with someone else.
A document has the same sharing permissions as its folder
When you save or create a document in a folder, it takes on the sharing permissions of the folder. To help you keep track of which folders you have shared and which you haven’t, Google gives you a confirmation dialog box to remind you that the document you are creating in a folder will be shared.
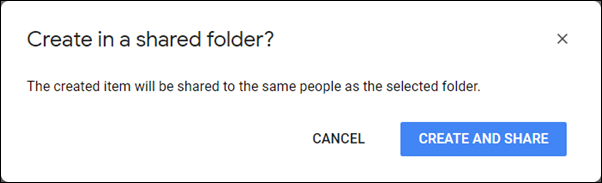
It also gives you one when you move a document to a folder that is shared.

Unfortunately, it does not give you a reminder when you upload a file into a shared folder. How do you remember which folders are shared and which aren’t? It can be confusing. A neat little trick I use is color coding. I color all the shared folders red. That way I can quickly and easily see which folders are viewable by others and which are only viewable by me.
Any folder in the Shared with me section may be viewable by others
When someone shares a document with you, it appears in your Shared with me section of your Google Drive.

Any folders found here were not created by you. If they are shared with you, they likely are shared with other people as well. Before you create or add a file to one of these folders, check its sharing permissions so you know who will be able to access your document.
Documents in Shared Drives may be shared with people who are not members
When Shared Drives first came out, they were called Team Drives and only people who were members of the Team could access the documents. Google has updated this feature. Along with a new name, you can now share folders and files in the Shared Drive with people who are not Team Members. Once again, this makes it challenging to determine which folders are shared with who. Unfortunately you cannot change the color of the folder icon in Shared Drives. Instead, ask all Team Members who create folders to put SHARED in the folder title if it is shared with people outside the Team.
The fewer people that have access to a document, the more secure it will be
Only share a document with the entire Mount Royal community or everyone who has a link, if that document really needs to be accessible by all those people. There is no need to share a contact list with the whole campus when only your department needs access to it. Don’t share a recording of your lecture with the whole campus if only your students need to access it. As soon as you open up document access to a large audience, you start to loose control over its contents. Before you know it, you have people contacting you asking for more information about about a topic that they should have no knowledge of. Keep your documents secured, only share them with those who absolutely must access them.
I hope that this information has cleared up some of the confusion around safely sharing files on Google Drive. For details on how to share files, visit the Google Drive Help webpage.
Workshop and Cybercafe held next week 09/17/20
Next week we have two events being held. September 22, 2020 is the Protecting yourself against cybercrime 2021 workshop from 2:00 pm to 3:30 pm. This is a great opportunity to complete your mandatory training and ask as many questions about cybersecurity as you like.
If you are not able to make the training but still would like to discuss cybersecurity, join us for the Cybercafe on September 24 at 3:00 pm. For 30 minutes you can ask all your burning cybersecurity questions. Our Security Administrator will be joining us, so the questions can get as technical as you like. While you can ask anything you like, I will also be presenting a current news item as a topic of discussion. Check back on September 23 to see what that topic will be.
See you there!
Don’t take candy from strangers – 09/16/20
All malware is not created equal. This week a particularly devious piece landed in an MRU inbox. It was wrapped up in a zip file attachment. Here is what the malicious email looked like:
This malicious email is hard to identify as it contains a previously sent email thread. Interestingly enough, there is no human behind this email. It was sent by malware. When it gets on your machine it picks an email in your inbox and replies to it. Sending a copy of itself to an unsuspecting recipient.
The email is generic enough to work with pretty much any email. However it is the vagueness that flags it as suspicious. The other tell is the sender’s email address. Because this is malware and not a person sending out the email, the sender’s email address is incorrect.
If you decide to click and open the attachment, you see an Excel spreadsheet with this in the first cell.

If you missed the other two red flags, this one is your last chance to dodge the bullet. This very official looking graphic is asking you to enable editing and content to be able to “decrypt” the document It is also telling you what type of device to use to view it. Anytime you have this kind of instruction given to you to view a document, close it immediately and report it.
The instructions are not there to enable you to view the document. They are there to ensure the malware can be installed and will function. By asking you to enable editing and content, it is bypassing the safety controls we have in place to prevent the running of macros. It is not “decrypting” anything. If you can’t open a document just by clicking on it, consider it a threat.
This is another reminder how important it is to check the sender’s email address before you open an attachment or click on a link. If you recognize it, contact the sender using another method and confirm that they sent the email. If you don’t recognize it, don’t click. You wouldn’t take candy from a stranger, you shouldn’t take attachments from them either; no matter how enticing they are.
