See what information Google is collecting about you – 03/27/2023
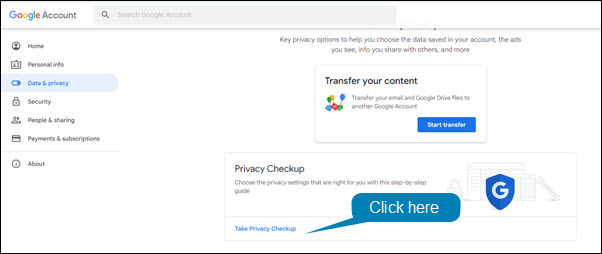
On a weekly basis, we hear about evil Google and its data collection practices. Fortunately, you can see exactly what data Google is collecting and limit it. To make this whole process easier, Google has a Privacy Checkup that you can run.
To run the Privacy Checkup:
- Open Chrome or Gmail.
- Click on your profile picture in the upper right hand corner of the window.
- Select Manage your account from the drop down menu.
- In the left hand menu, click Data & Privacy.
- Click Take Privacy Checkup.
The use and care of your MRU email address – 12/07/212
We are regularly notified that Mount Royal email addresses have been involved in a data breach through Have I been pwned. When we receive that notification, we are told what account provider was affected and which email addresses were involved. This allows us to contact those who had their accounts compromised and ask them to change their passwords.
With multi-factor authentication enabled, this is less of an issue. Even if a password is stolen, the attacker will not be able to get into a MRU email account without the second factor. However it is still important that compromised passwords are changed, especially if the same one is being used for multiple accounts. So we are still receiving data breach notifications.
Usually the data breaches are for work related services. However, once in while we are notified that a gaming site, dating website or a site with adult content has been breached. If you have used your Mount Royal email address to access that site, we will be notified. It is awkward for everyone when that happens.
Please keep your private life private and only use your MRU email address for work purposes. We don’t need to know what you do for hobbies, how you spend your time outside of work or where you shop. Save us all the embarrassment and use another email address for your personal pursuits. The security team thanks you.
Google Chrome Privacy Settings you Should Check – 03/17/21
A while ago I posted an article on Data Privacy Day. Out of that article, several readers requested recommendations on privacy settings for Google Chrome. As much as I would love to tell readers to lock down everything and shut down the great Google data collection, privacy is a very personal thing. One person may be willing to give up functionality of their tools to ensure their private information stays private, while another is just fine with all knowing Google collecting their data if it means their life is easier. In short, I cannot tell you wonderful people what to lock down. Each one of you has to make that decision for yourselves.
That said, I can tell you what settings to check and where they are currently located. Google, just like most other service providers, likes to make them hard to find. A cynical person would say that was done on purpose. I have decided to be more positive today and I am going to blame poor interface design… I am trying here. Work with me.
Decide how your browsing history is used in Chrome
Most of the privacy goodies are hidden under Settings>Sync and Google Services. The first stop should be Control how your browsing history is used to personalize Search, ads and more. Click on the little square next to this monster and you find the Activity Controls.

At first glance, all you see is Web & App Activity. Scroll down a bit and click the See all activity controls link to find the motherload.

These settings determine how much functionality you want from Chrome vs how much data you want to keep from their prying eyes. It may take a few tries to find the right balance for you. Don’t be afraid to turn on some controls. You can always turn them off if they are making your life difficult. Personally I prefer to give them as little information as possible and find things on my own. I don’t like to be fed my content. You can stumble upon some pretty interesting stuff when you don’t have someone curating your content for you. However, that might not be your jam. Totally okay.
Further down the Sync and Google Services page, there are some other settings that you should check. Do you want to help Google be a better service, or send them your URLS or the text you type into the browser? Once again, try turning them off and see what happens to the functionality of Chrome.
Decide how you will be tracked
Cookies are used by websites to identify you for a variety of reasons. Some of them are useful like keeping track of what is in your shopping cart. Others are more concerning like tracking what you click on. As with all browsers, Chrome lets you decide what types of cookies are okay and which are to be disabled or blocked.
Chrome’s cookie settings can be found in Settings>Cookies and other data. I do not recommend selecting Allow all cookies or Block all cookies. However you may want to experiment with Blocking third party cookies.
Another setting you can consider is the Send a “do not track” request with your browsing traffic. As it suggests, it simply sends a request to a website that you not be tracked. How they respond to the request depends on the website. However, I feel better knowing that I have at least asked for some privacy. The odds that they honor that request are probably pretty slim. There I go being all cynical again. Sorry, I slipped.
Cover your tracks
Your browsing history including cookies, cached pages and autofill data can be cleared out manually or you can set it up to perform a cleaning at regular intervals. Ideally things should be cleaned out once a week, however the best cleaning interval for you depends on how you work. Do be aware that if you clean out cookies regularly, it may mean you have to re-enter things on sites over and over again. As with the other settings, experiment with it to find what works best for you. You can find these settings under Settings>Clear Browsing data.
Inconclusion
Even if you try out these settings and decide to not enable any of them, that’s perfectly okay. The important thing is you are aware of them and know how to change them. You are taking control and making decisions about your privacy instead of having them made for you.
Unfortunately, account providers regularly change their privacy settings and Google is no different. The information in this article may be out of date in a week, a month or tomorrow. Therefore, I suggest that every quarter you take a look at your privacy settings and make sure they are still at a comfortable level. A little proactivity goes a long way when maintaining your privacy.
Why is someone you know asking for your phone number? – 03/10/21
The MRU community have been finding emails in their spam folder similar to this one.

The email looks like it comes from a colleague or instructor. However the email contains some red flags. The biggest one being they are asking for your personal phone number. If they don’t already have it, they shouldn’t be asking for it. In addition, it was found in the Spam folder.
Google puts emails that it thinks are suspicious but they aren’t sure of into the Spam folder. If you see an email in your Spam folder, assume it is malicious and always confirm legitimacy with the sender before you respond. Confirmation is best done over the phone, however in situations like this where an MRU email wasn’t used, it is enough to contact the sender through an MRU email.
It is hard to say what the end game of this scam is. However, this is often step one in a gift card scam where they compel you to purchase gift cards and then give them the redemption codes. These redemption codes can then be sold on the dark web.
It was Data Privacy Day, have you checked your privacy settings lately? – 01/28/21
January 28, was Data Privacy day. This is the one day a year that we are reminded how valuable our data is. We should protect it like we protect our money. However, account providers regularly change their privacy policies, settings and terms and conditions which makes that challenging.
When account providers make those types of changes, they sent out a notification email or we see a popup appear when we login to our account. Both are annoying and both require us to acknowledge we are aware of the changes before we can use their service. When we receive that notification we usually don’t have time to wade through the legalese to find the changes, we just click accept and move on with our day.
Data Privacy Day is a great time to take a pause and check those changes. Check both the terms and conditions and privacy settings. That way you know what data the account provider has access to and how much control you have over it. While this is a pain, taking a few minutes to check things now can save a lot of heartache later. In addition, if you are not comfortable with the changes it gives you an opportunity to let the account provider know and if necessary find a new service.
An easy way to see if your Google Drive files are findable by others – 11/03/20
Documents in Google Drive can just be shared or shared and findable. A shared document is one that you are giving a specified person or group of people access to. If you don’t have the link to the document or the document isn’t shared exclusively with you then you can’t access it. In other words you have to specifically been given permission to see the document.
A findable document is one that anyone with an @mtroyal.ca email address can search for. All they need to do is enter a term in the search field in Google Drive and Google will find all the documents that contain that term in the filename or contents. Therefore they don’t need to have the link to access the document, they can just search for it.
Currently, the option to make a document findable is buried in the settings wheel that is only accessible when you want to generate a document link that can be used by members of the Mount Royal University group.

This makes it difficult to accidentally make a document findable. However, a few years ago this option was part of a drop down that included other sharing permissions. This made it much easier to select it when you didn’t intend to. The good news is, only MRU community members can search for the document. The general public cannot. So if you accidentally made the document findable, you are somewhat protected.
Now for more good news. While there is no easy way to determine which documents have been shared. There is an easy way to determine which of your documents are findable, just type owner:me source:domain in the Google Drive search bar and press Enter on your keyboard. It will bring up all the documents that you own that are marked findable. As a document can’t be findable unless it is shared with the whole campus, this should help you track down some of your accidentally shared documents and folders as well.
You are welcome!
Check the sharing permissions on your files stored on the Google Drive – 10/21/20
With the move to working from home, many of our business processes have changed. For example, documents that we used to save on the J: drive have had to be moved to the Google Drive to ensure everyone has access to them. However unlike the J: drive where everything saved on it is viewable only by your colleagues in your department, the Google Drive allows you to share a single file or a whole folder with anyone. To quote Winston Churchill
Where there is great power there is great responsibility…
It has come to our attention that many of you are struggling with this power. We have found there are many documents sitting in the Google Drive that are viewable by anyone with a Mount Royal email address that really shouldn’t be. Submitted student assignments, job offer letters and lecture recordings are just some of the documents that are viewable by the entire MRU community.
We appreciate that you are doing the best that you can with what you have. We have all been thrown into a working situation that none of us were expecting. In the middle of which, Google decided to change its file sharing dialog box. So even if you were familiar with how to share files, you have had to relearn it. Throw in Shared Drives and it is no wonder so many documents are viewable by the wrong people.
If you have read this far and are thinking, “I know how to share files, I am sure that no one has access to them who shouldn’t”, please take a moment to check the sharing permissions on your files that contain sensitive information. As I said before, Google has changed their Sharing dialog box and we have oodles of sensitive documents that are viewable by the whole campus. You may think that your documents are secured, but they may not be. Don’t assume, check.
If on the other hand you have read this far and tears of frustration are streaming down your face, I come with a message of hope. File sharing is easy once you understand a few key concepts.
The Google Drive is one massive server
When you save or create a document on the Google Drive, you are placing it on a huge server that the whole world has access to. You only see the files and folders that you have been given permission to see. By default that is all the files and folders you create. The same is true for anyone else who uses Google Drive. So when you create or save a document to the Drive, is it unviewable by anyone except you until you share it with someone else.
A document has the same sharing permissions as its folder
When you save or create a document in a folder, it takes on the sharing permissions of the folder. To help you keep track of which folders you have shared and which you haven’t, Google gives you a confirmation dialog box to remind you that the document you are creating in a folder will be shared.
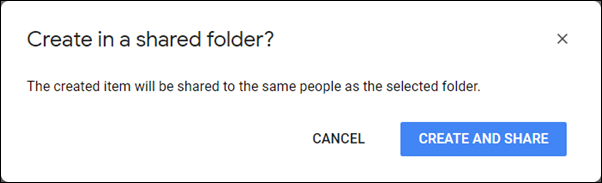
It also gives you one when you move a document to a folder that is shared.

Unfortunately, it does not give you a reminder when you upload a file into a shared folder. How do you remember which folders are shared and which aren’t? It can be confusing. A neat little trick I use is color coding. I color all the shared folders red. That way I can quickly and easily see which folders are viewable by others and which are only viewable by me.
Any folder in the Shared with me section may be viewable by others
When someone shares a document with you, it appears in your Shared with me section of your Google Drive.

Any folders found here were not created by you. If they are shared with you, they likely are shared with other people as well. Before you create or add a file to one of these folders, check its sharing permissions so you know who will be able to access your document.
Documents in Shared Drives may be shared with people who are not members
When Shared Drives first came out, they were called Team Drives and only people who were members of the Team could access the documents. Google has updated this feature. Along with a new name, you can now share folders and files in the Shared Drive with people who are not Team Members. Once again, this makes it challenging to determine which folders are shared with who. Unfortunately you cannot change the color of the folder icon in Shared Drives. Instead, ask all Team Members who create folders to put SHARED in the folder title if it is shared with people outside the Team.
The fewer people that have access to a document, the more secure it will be
Only share a document with the entire Mount Royal community or everyone who has a link, if that document really needs to be accessible by all those people. There is no need to share a contact list with the whole campus when only your department needs access to it. Don’t share a recording of your lecture with the whole campus if only your students need to access it. As soon as you open up document access to a large audience, you start to loose control over its contents. Before you know it, you have people contacting you asking for more information about about a topic that they should have no knowledge of. Keep your documents secured, only share them with those who absolutely must access them.
I hope that this information has cleared up some of the confusion around safely sharing files on Google Drive. For details on how to share files, visit the Google Drive Help webpage.
How to avoid having your Google meeting bombed – 04/22/20
Although Google Meet is a more secure platform than Zoom. It isn’t immune to meeting bombers. This week, an MRU employee had a rather disturbing and unfortunate experience with one of their Google meetings.
As the meeting organizer, they followed a registration process that had been established for their department’s meetings to ensure that all attendees were legitimate. However as this is a new platform and there are special circumstances that arise, they knew that there would be individuals signing in who would not be on the registration list. So when they received a request to join the meeting they were not concerned. That is until they attempted to verify the attendees identity and were rewarded with profanity.
The organizer of the meeting removed the trolling attendee. However there were several other attempts by this same individual to join the meeting again. In their brief time as an attendee, they had a grabbed a list of other attendees. They then impersonated one of them and repeatedly asked to join. The poor organizer had to keep asking the impersonated attendees if they were attempting to join using another email address. The whole incident was very disruptive. The organizer handled things very well but wanted to know how to prevent this from happening in the future.
There are a few things that you can do. First if you are using nicknames for your meeting, avoid using common meeting names. Team meeting, department meeting and math class are examples of nicknames to avoid. This prevents trolls from finding your meeting simply by entering nicknames that are commonly used. Second, if at all possible don’t post meeting links in a public location. Try to limit it to meeting invites if you can. Third, simply deny join requests. Join requests are only required if the attendee isn’t using a Mount Royal email account. Let your attendees know that they must use their Mount Royal email address to join your Google meetings and you will avoid this problem all together.
If however you are meeting with people outside of the Mount Royal community, then you will have to rely on the other two measures to keep trolls from bombing your meeting. If you are having meetings of this nature regularly, contact the IT Service Desk to see if another video conferencing solution is available for you to use.
How to video conference safely – 04/16/20

With everyone working from home, video conferencing has gone from being a novelty to being a necessity. Many of you are working virtually for the first time. With new experiences come new challenges. Mistakes are being made, that is to be expected.
To help you make your video conferencing experience as safe as possible, I have found these terrific tips from SANS on how to keep your data safe and prevent accidental expose of sensitive information. With a little knowledge, you can become a video conferencing security expert. As always, feel free to share this information with your family, friends and colleagues.
VideoConferencingTips-ForAttendees-1Pager
Only you can use your MRU account – 02/26/20
When we tabulated our survey results, we were delighted to find a significant reduction in password sharing on campus. However, our victory lap did not last long. Password sharing is happening less but there are scary numbers of people logging in and letting someone else use their account.
We understand that you have guests that come on campus and need wifi access, that you have new employees that you need to train and that sometimes a colleague’s or friend’s account isn’t working. However regardless of the reason, credentials should not be shared. Your credentials are only for your use. They give you exactly what you need to have access to, no more and no less. This protects you, your colleagues and the institution.
Stop for a minute and think about all the things only you can access with your login credentials that no one else has access to. Do you really want someone else to be able to access those things? Think about how embarrassing, uncomfortable or alarmed you would feel if a colleague or friend started exploring. I know what you are thinking, I can trust them. They wouldn’t do anything malicious with my account.
Regularly we hear about horror stories of friendships gone wrong, bitter colleagues, bad breakups and the resulting fallout. When things go bad it is impossible to predict how someone will react. You would be unpleasantly surprised to know the damage that has been caused when these things occur.
Even if letting someone else use your account doesn’t result in data armageddon, it is against the Acceptable Use of Computing and Communication Resources Policy. The good news is there is no reason to do so. IT Services can arrange access for anyone for any reason. We have a solution for every situation. Find yours in the Credential Use Guidelines. If you aren’t sure what to do, just call the IT Service Desk and let them know what your time frame is. They will get back to you right away and provide you with a solution.
Don’t give up control by logging in for someone else. Reserve your account for your use only, not the other 114 people who are looking for access.
