Phone recharge led to wiping a laptop clean – 07/26/2023

Last week Carrie (not her real name) lost three days of productivity when her laptop had to be reimaged. For those of you who don’t know what reimaging is, it is when ITS has the pleasure of wiping everything off of your machine and then reinstalls the standard applications.
I know what you are thinking, “If they reinstalled everything, why did she lose three days of productivity?”. Simple, no one has just the standard applications with the default settings on their computer. Every department and every person has their own special applications and settings that allow them to do their job more effectively. It takes time to get your machine back to where it was before it was reimaged. In Carrie’s case, it was three days.
What caused all this inconvenience and frustration for Carrie? A stranger’s smartphone. Yup, you read correctly. A smartphone. When Carrie left for a two day vacation, she left her laptop tucked under the shelf of her standing desk plugged into the docking station. Carrie works in reception and she doesn’t have a door that she can lock. She thought if she just left it tucked out of the way, her laptop would be safe. Afterall, her department’s offices are behind doors that are locked every night.
While she was gone, her colleagues heard an alarm going off at her desk. When they investigated, they discovered the source of the alarm was a smartphone plugged into her laptop. They contacted Carrie to see if the phone belonged to her. When she assured them that it didn’t, they checked with the rest of the department. The smartphone didn’t belong to anyone there either. Security was called but they were unable to determine who the smartphone belonged to. Because there was no way to know if this was a malicious act or not, it had to be assumed that the smartphone had downloaded something nasty onto Carrie’s laptop.
The laptop was reimaged according to ITS security protocols. They require that If a device could be compromised, it is reimaged … period. Even if a malware scan finds nothing, we do the safest thing which is to wipe the machine clean.
Sadly, it is most likely that some MRU employee from another department innocently plugged their phone in for a quick charge and then forgot about it. In their rush, it never occurred to them they would be causing such grief.
This story is a reminder to everyone.
- If your phone needs charging, please use your own computer or the public charging stations around campus. DO NOT use a colleague’s computer.
- Secure your device as much as possible when you leave for the day. If you have a laptop. take it home or lock it away. If you have a desktop, lock your office door or make sure the common area door is locked.
- Do not store files on your desktop or C: drive, otherwise you will lose them if your machine has to be reimaged.
- If you find a strange device plugged into your machine, do what Carrie’s colleagues did, contact Security and ITS. Do not use your computer until ITS has determined it is safe to do so.
These simple steps will protect our network while saving you and your colleagues a lot of time and frustration.
How to mark an email as unread on your phone – 07/18/2023
When reading an email on your phone, it is challenging to determine if the email is malicous or not. The screen is just too small to see the red flags, increasing the chances you will become a victim of a cyberattack.
Reading an email on your phone is perfectly safe. However when you are asked to take action, mark the email as unread and read it again later on a larger screen. While this is great advice, how exactly do you mark an email as unread on the Gmail app?
To mark an email as unread on the Gmail app:
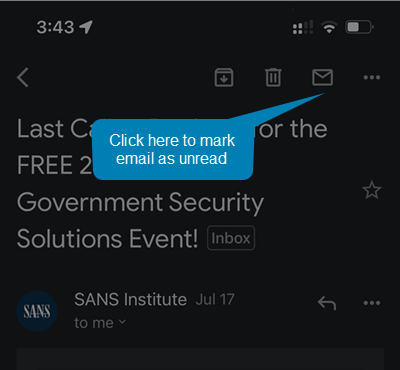
- Open the email
- Click on the envelope in the upper right hand corner
Smishing attack thwarted by faculty member – 03/14/2023
It was just after 11:00 AM on a Friday when Kelly Sundberg received this text message
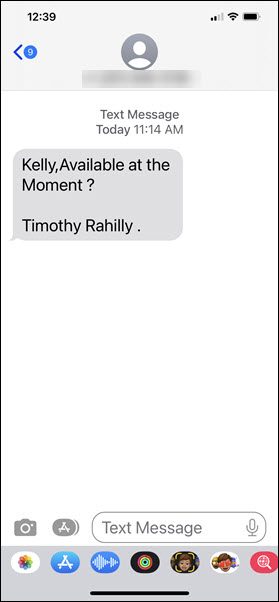
This was an odd request as the text was coming to Kelly’s personal phone. However, if something was urgent, maybe it was Tim texting him. What Kelly did next saved him from being scammed out of thousands of dollars, he contacted the Presiden’ts office and asked if it really was Tim that had texted him.
As it turns out, Tim wasn’t even in the city. The text had definitely not come from him. It had come from a scammer whose next move would have been to convince him to purchase gift cards as rewards for hard working colleagues.
Before you say, “I would never fall for that scam”, know that more than one person on campus has. It isn’t because they are stupid or because they didn’t take their cybersecurity awareness training. They became victims because the attackers are just that good at confusing you, creating urgency and getting you to react instead of think.
Kelly did two very important things right, firstly he stopped and let his rational thought kick in before he took action. As a result, the attackers did not have a chance to confuse or manipulate him. Secondly, he followed the guidelines in the cybersecurity awareness training, verify before you take action.
No matter how certain you are that a text or email is coming from your boss, if an unexpected request is made, call the sender and make sure the message actually came from them. That one step saved Kelly, it could save you too.
Checking an email? Get a bigger screen – 12/08/2023
Updated 07/18/2023

Phishing emails are the bane of our existence. They take our precious time as we slow down to take a close look and make sure that email from our colleague is really coming from our colleague. This whole experience is a lot more challenging when we are attempting to do our analysis on a smartphone.
While reading an email on our phone is perfectly harmless, things can become dangerous when the email asks us to take action. To click or not to click? Do we send the requested information or not? How is one to know when it is hard to see the link URL or sender’s email address on that small screen?
It is so challenging to spot a malicious email on a phone, that even IT professionals get tricked. That’s right … Information Technology professionals get tricked. The people that get tricked repeatedly in IT are ALL trying to see phishing red flags on a smartphone screen and fail.
The next time you read an email on your phone that has a link, contains an attachment or is asking for sensitive information, mark it unread. When you are able to view it on a larger screen; re read it and look at the sender’s email address , hover over the links and check the grammar. While taking the extra time is inconvenient, it is far less painful than loosing half a day of work while you factory reset your phone or deal with the fallout of a data breach.
Fake TD texts try to nab your banking credentials – 12/15/21
Look at what showed up on the phone of an MRU community member.

The links in this text do not go to the TD Canada Trust website. The person who received this text does not bank with TD so they knew it was a fake alert right away. However, if you do bank with them and receive this text, the odds are pretty good you will click. The whole alert received thing tends to make people panic. When they panic, they react. Rational thought never has a chance to kick in.
We don’t know for sure what will happen if you click one of the links. However, as it tells you to login, the odds are good that you will be directed to a fake TD login page. When you enter your username and password, the criminals will likely record and store your credentials to either use themselves or sell on the dark web. Either way, they can drain your bank accounts.
This is a reminder that if you receive an email or text from your bank, count to 10. Then call them directly using a phone number that you know is legitimate to ask them if there is a problem with your account. Resist the urge to click, no matter how great it is. Salvation is only a phone call away.
Identity theft in 2020: Everyone is a target (a MRU employee tells their story) – 03/04/20
As coordinator of the cybersecurity awareness program here at MRU, I often have colleagues call me with their own personal tales of horror. One of the more recent ones involved a Port-out-scam. Here is a their tale, written in their own words…
Until recently, identity theft was definitely something that we never thought could happen to us. It’s something that we warned our grandparents, our parents and even our security-relaxed friends about. But we were totally safe, or so we thought.
Through this experience our lives have definitely changed forever. We have learned a great deal and are now more aware, and will be more vigilant. It was shocking to discover how easy it might be to lose everything.
Upon landing at the airport in Calgary at 2 AM following a holiday early in January, my boyfriend (for privacy we will call him James) turned his phone on to discover that he had no carrier service. We didn’t think it would be anything serious and joked about something being wrong with his last payment.
The next morning James called Telus and a Customer Service Agent informed him that he had ported his number out to Bell on Tuesday, to which he quickly replied that he had been out of the country, so that was impossible. After some convincing that this action was not taken by James, Telus quickly, and easily, ported the number back from Bell. We knew at this point that something was very wrong. He was also unable to get into his Microsoft Outlook email account; his password was denied.
Once James had his number back, he was able to use his phone (with SMS two-step authentication) to reset his password and get into his email accounts, where we quickly realized the horrifying truth that his identity was compromised. Someone had accessed his email account with his phone number, changed the password, and taken over. James’s email account is connected to everything: PayPal, Amazon, personal & joint banking, investments, taxes, etcetera. I am sure you can imagine the anxiety James and I felt in that moment of realization.
You’re probably thinking that James did something to be a target. He must have been lenient with his security questions, or displayed some weakness with online purchases or social media. We have gone over everything meticulously to try to figure this out, and with the help of many people, our conclusion is that he actually did nothing wrong. All the hackers needed to access his email was his phone number. He is not a prominent person and does not hold a prominent position, so not your typical target according to experts. Further, he is very private and careful, with the strongest security settings on his social media accounts where he is also conscious about everything he posts, and any business he does online shopping with.
Next came the long process of regaining control…. cancelling credit cards, bank accounts, informing all business and friends of the identity theft…setting up security watches on James’ Social Insurance Number through various government services…..hours of waiting on hold, explaining the situation and the frustrating experience of having to convince people of the seriousness of the situation.
We talked to Calgary Police Service (CPS), and while they made some good suggestions of things to change, credit checks to put in place, it was also frustrating that there was nothing they could do. Because no physical property was actually taken there will not be an investigation. We were also informed that we should maintain a close eye on all of James’ accounts for at least six to eight years as we don’t truly know what information the hackers obtained and they may resurface at a later date.
Microsoft Outlook support was useless because the same security measures that should help in this situation caused serious issues. The hackers were able to change the security settings in the account before James got it back. They added their own email addresses and phone numbers as new two-factor authentication security. It is part of the Microsoft Outlook security plan that when changes are made there is a 30-day freeze before further changes can occur. Despite hours speaking with Microsoft Outlook staff at all levels, they refused to close the accounts before the 30-day freeze.
Through all of this we learned that this is called a Port-out Scam. In this case, Telus confirmed to James that his account number was provided to Bell in the port. There was an incredible lack of due-diligence to verify one’s identity in this case. This type of scam has been known to play on the emotions of customer service agents at telecommunications companies and the lack of security measures in place to protect customers.
How does it work? The hacker would have acquired James’s name and phone number from somewhere to start – not difficult given the world we live in. Next they might have called Telus, pretending to be James, claiming they want to make a payment on their account, but they are not at home and didn’t have their account number – can they have it? The customer service agent should refuse, or ask detailed security questions only James can answer, but instead they provide the number. (CPS told us that hackers can also get addresses, email addresses and more this way) Next, armed with everything they need, they simply call another company (Bell in this case) and pretend to be James, saying they want to port their number over from Telus. Just like that the hacker owns your number and now they can get into anything your number is tied to for two-step authentication.
James called Bell to inform them of the theft and that they were used in the process of the theft, and, surprisingly, they brushed him off. Told him it was not their problem. Wanting to understand how this could possibly happen, I called Bell to casually inquire about moving over from my existing carrier and told the customer service agent I wanted to keep my phone number. She was more than happy to assure me it was no problem to keep my number – all I needed was my number, and to ensure my account with my previous carrier was in ‘good standing.’ It was way too easy.
The comical part in this experience is that while it was so easy for the hacker to steal James’s number, in order to cancel his phone number (once he got it back) the Telus Customer Service Agent’s protocol was to hang up and call James back to verify that it was his number, as well as asking for detailed account information and his driver’s licence number. This means that there is protocol that exists, but no assurance that it is followed regularly.
We are sharing this story as we hope that others will learn from this. We want telecommunications companies to start taking security seriously and we want you to be vigilant. Instead of assuming you are taking precautions and you are safe from identity theft, in 2020 it is safer to assume you are a target and take precautions for the day you will be attacked.
Mystery Blogger
(MRU Employee)
Is there a way to use 2FA that will provide security even if you are a victim of a port-out or SiM swap scam? Yes there is. Read How to prevent a two factor authentication compromise to find out.
More malicious apps found on the Play Store – 12/13/18
Google has removed 22 apps from the Play Store that together have had over 2 million downloads. The most popular being Sparkle, an Android flashlight. The apps seem to work as described. However in the back ground they are clicking on ads which generates revenue for the advertisers.
Not only does this slow down your phone, use up battery power and is just down right annoying, but it also is fraudulent. Companies pay online advertisers only when someone clicks on their ad. The idea is if the advertiser does their job and places the online ad in the right locations, then a click on the ad should lead to a sale.
That is what companies think they are paying for, potential customers. Instead this app acts as a bot, clicking on ads thousands of times and raking up the charges for the company. The company receives nothing in return as bots aren’t big shoppers.
What should you do if you have an Android phone? First of all, check the list of affected apps to see if you have downloaded one of them. You can find the list in the Sophos article. Then uninstall the app. As an extra precaution you can perform a full factory reset.
Although downloading apps from reputable sources reduces the chances of you downloading something malicious, it does not guarantee it. Remember to check reviews for an app before you download it. If you find a reduction in your phones performance after the download, uninstall the app. If it continues then perform a factory reset.
Buying tech this Christmas? Check out its creepy factor – 11/20/18
This year, there are tons of cool tech gadgets on the market. Everything from teddy bears that connect to the internet to personal alarms. As neat as all of these devices are, some of them have the potential to leave the users feeling exposed and violated.
Thankfully, the good folks at Mozilla have put together a terrific website that examines the privacy risks of the hottest tech gifts. At privacy not included you can find out what information a device collects, what is done with that data and what kind of security the device has. They also rate customer service. To make it extra fun, consumers can give each item a creepiness rating based on how comfortable they would be having that device in their home. Check it out.
Scammers using voicemail to steal WhatsApp accounts – 10/17/18

Armed with nothing more than your phone number, criminals can steal your WhatsApp account. How? By registering your phone number on their phone. Here is how it works.
First the attacker makes a request to have your phone number registered to the WhatsApp application on their phone. When WhatsApp receives the request, they text a verification code to your phone. The scammers make their request in the middle of the night or when you are on a flight so you don’t see the verification code. With the text not answered, WhatsApp offers to read out the code and leave it in a voicemail.
If your cell phone carrier has a default password set up for voicemail and you have not changed it, the criminal simply enters the default password and boom…they can hear the verification code. Once they enter that code, the account gets transferred over to their phone. The attacker then sets up two step verification on the account and you have no way of getting it back.
The moral of the story, set strong and unique password for your voicemail. While you are at it, do that with all your accounts.
Porn Hoax messages on WhatApp targeting kids – 09/13/18
There is a disturbing new hoax making the rounds in WhatsApp? Children are receiving messages in in the app from someone named Olivia who claims to know them, but has a new phone number. Once they establish contact, they send the child a link to porn sites. Although this is currently happening in the UK, hoaxes like this can quickly spread.
This would also be a good time to review with your child how to stay safe online, and remind them to not forward hoax messages.
