An unlocked computer can be compromised in 30 sec or less
With educational records fetching up to $265 on the black market and competing nations trying to catch up in the knowledge race, higher education institutions have become prime targets for cyber attacks.
We are entrusted with a treasure trove of intellectual assets that attackers are constantly trying to gain access to. Locking your computer screen when stepping away, even momentarily, is an easy but effective way to protect them. This simple measure ensures that your academic work stays safe from prying eyes, maintaining the integrity of your research, student data, and other sensitive information.
Locking your computer screen is this easy
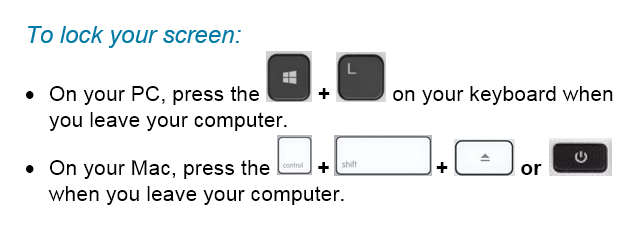
When you take the time to lock your screen, it not only prevents unauthorized individuals from gaining access to your data but it also demonstrates your professionalism and commitment to safeguarding the trust placed in you as a member of the Mount Royal community.
Developing the lock screen habit is easier if it is implemented into your regular routine regardless of where you are working and what device you are using. Lock your screen even when working from home or using your personal devices. This will help develop the habit. Everytime you stand up to leave your computer, remember this motto “Leave it? Lock it!”
By embracing this habit, you contribute to the resilience of the academic community against malicious actors attempting to profit at the expense of students privacy and academic research. Stay vigilant and protect your devices so that you can continue to help shape the minds of future generations.
Phone recharge led to wiping a laptop clean – 07/26/2023

Last week Carrie (not her real name) lost three days of productivity when her laptop had to be reimaged. For those of you who don’t know what reimaging is, it is when ITS has the pleasure of wiping everything off of your machine and then reinstalls the standard applications.
I know what you are thinking, “If they reinstalled everything, why did she lose three days of productivity?”. Simple, no one has just the standard applications with the default settings on their computer. Every department and every person has their own special applications and settings that allow them to do their job more effectively. It takes time to get your machine back to where it was before it was reimaged. In Carrie’s case, it was three days.
What caused all this inconvenience and frustration for Carrie? A stranger’s smartphone. Yup, you read correctly. A smartphone. When Carrie left for a two day vacation, she left her laptop tucked under the shelf of her standing desk plugged into the docking station. Carrie works in reception and she doesn’t have a door that she can lock. She thought if she just left it tucked out of the way, her laptop would be safe. Afterall, her department’s offices are behind doors that are locked every night.
While she was gone, her colleagues heard an alarm going off at her desk. When they investigated, they discovered the source of the alarm was a smartphone plugged into her laptop. They contacted Carrie to see if the phone belonged to her. When she assured them that it didn’t, they checked with the rest of the department. The smartphone didn’t belong to anyone there either. Security was called but they were unable to determine who the smartphone belonged to. Because there was no way to know if this was a malicious act or not, it had to be assumed that the smartphone had downloaded something nasty onto Carrie’s laptop.
The laptop was reimaged according to ITS security protocols. They require that If a device could be compromised, it is reimaged … period. Even if a malware scan finds nothing, we do the safest thing which is to wipe the machine clean.
Sadly, it is most likely that some MRU employee from another department innocently plugged their phone in for a quick charge and then forgot about it. In their rush, it never occurred to them they would be causing such grief.
This story is a reminder to everyone.
- If your phone needs charging, please use your own computer or the public charging stations around campus. DO NOT use a colleague’s computer.
- Secure your device as much as possible when you leave for the day. If you have a laptop. take it home or lock it away. If you have a desktop, lock your office door or make sure the common area door is locked.
- Do not store files on your desktop or C: drive, otherwise you will lose them if your machine has to be reimaged.
- If you find a strange device plugged into your machine, do what Carrie’s colleagues did, contact Security and ITS. Do not use your computer until ITS has determined it is safe to do so.
These simple steps will protect our network while saving you and your colleagues a lot of time and frustration.
Chrome’s latest update includes a confusing pop up – 06/01/22
Chrome has been updated. As part of the update, a pop up appears when you login

This pop up is simply reminding you that Mount Royal University is managing your MRU Workspace account and that we have access to it. This new pop up is part of Google’s new privacy features. There hasn’t been any changes to your account, the University has always had access to it. The pop up isn’t malicious and your computer has not been hacked.
Click to select Keep local browsing data to save your current bookmarks. Then click the Continue button to close the pop up and use Chrome/Google Workspace as usual.
Innocent looking webpage hides malware – A true story – 05/25/22

It was just another day for an MRU staffer. He was fielding calls and sorting through emails when he received an invite to a conference. He just needed to double check the session time. However, it was listed with a different time zone than his. It was early in the morning and his brain wasn’t fully functioning so he was unable to covert the time in his head. He Googled “time zone converter” and clicked the first link listed in the search results.
As soon as the webpage loaded, mayhem erupted on his computer. Three hundred and seventy four pop-ups appeared. Big scary alerts with flashing arrows pointing to a button said he had a virus. Click here said the button to remove the virus. You must click NOW flashed across the screen. Everything that could light up and flash was lit up and flashing. His computer screen looked like a slot machine that was about to pay out, only this pay out was malware not money.
He started to panic. He thought, “What do I do, what do I do? What did Bernadette say to do in training”. Then he remembered the first step.
Don’t touch anything
“Okay”, he thought, “I wont touch anything. what did she say to do next?”
Disconnect from the Internet
“Right.” He dug around behind his computer and yanked the network cable out from the back of it. “Okay, what is next?”
Contact the IT Service Desk
He picked up the phone and called the Service Desk. It took almost no time at all and a technician was there checking his computer. Thankfully, there was no harm done. Because he had followed his training and did not click on anything on the webpage the malware was never loaded onto his machine.
He was immediately grateful for the training he received. Had he forgotten to not touch anything on the screen, he would have lost a lot of his day and his data, getting his computer reimaged. While he knew the training was helpful, he didn’t realize just how much until he found himself experiencing a cyberattack. He was so glad he had taken his annual training. He was never going to consider it a waste of time again.
Restart your machine and save your data – 07/08/21
With the latest zero day threat PrintNightmare, putting printing on pause across the globe; it has become more important than ever to to keep your devices updated. While there is no update yet available to patch this vulnerability, it is a good idea to make sure your computer is ready when it is released.
The best way to do that is to ensure automatic updates on your Windows machine is enabled. MRU devices are automatically updated when you connect to the network so you don’t have to worry about them. This is a system setting controlled by ITS and it can’t be changed. However, you can mess with automatic updates on your home machine. You can pause them on a Windows 10 machine and turn them off all together on a Windows 8 machine. It is strongly recommended that if you have paused the updates or tuned them off , you enable them again. This ensures that as soon as the patch for PrintNightmare is available, it will be downloaded.
If you have a Windows 7 or older machine, the automatic updates feature is not an option, you will have to check for and download the update manually. For the most part, operating systems of this age don’t receive updates anymore and are vulnerable to attack. Which is why it is a good idea to upgrade to a newer one. The exception is when a really, really nasty vulnerability comes along. PrintNightmare falls into this category. Even Windows XP will receive a patch for this one. However, you Windows 98 and 95 holdouts are out of luck.
To complete the installation process, you have to restart your machine. This is true for MRU devices as well as your home machine. Depending on how your version of Windows is set up, you may or may not be notified that a restart is required. So it is a good idea to restart your machine daily. Daily restarts ensure that you both have the latest security patch downloaded and it has been installed as well. Also, it takes less time to restart a machine that has only one update to install versus one that has five. In just a few minutes you can save hours of heartache. Restart your machine and save your data.
Keep your devices updated with the latest security patches – 01/21/21
With criminals constantly coming up with new ways to hack into our systems, keeping your devices updated with the latest security patches is more important than ever. When you are on campus keeping your workstation up to date and secure is easy. Shut down your machine at the end of the day Friday and start it up Monday morning. However once you are working from home and your computer is always on keeping your machine updated isn’t so straight forward.
If you are remoting in to an MRU workstation you can’t shut it down. Instead, logout of the workstation and disconnect from GlobalProtect at the end of each work day. The updates are downloaded in the background as you work. Once you log out, your workstation is automatically restarted to install them.
If you have an MRU laptop assigned to you, it is setup to automatically download updates as you work. Once the updates are downloaded you are prompted to restart your machine to install them. As long as you don’t ignore the prompts, you are good to go. If you choose to ignore them and call the Service Desk for support, you won’t be helped until you restart your machine.
If you are using your personal computer, make sure you have automatic updates enabled on Windows/Mac OS and all your applications. From the Windows Start menu, select Settings>Updates and security to check your Windows update settings. On a Mac, select System Preferences>Software Update and click the Automatic Updates checkbox. Just like MRU laptops, updates are downloaded in the background and you are asked to restart your machine to install them.
Once you know what to do, installing your security patches is pretty easy. While it can be annoying, it is well worth your time. With a little bit of effort you make it exponentially more difficult for attackers to compromise your data and mess with your life.
Only you can use your MRU account – 02/26/20
When we tabulated our survey results, we were delighted to find a significant reduction in password sharing on campus. However, our victory lap did not last long. Password sharing is happening less but there are scary numbers of people logging in and letting someone else use their account.
We understand that you have guests that come on campus and need wifi access, that you have new employees that you need to train and that sometimes a colleague’s or friend’s account isn’t working. However regardless of the reason, credentials should not be shared. Your credentials are only for your use. They give you exactly what you need to have access to, no more and no less. This protects you, your colleagues and the institution.
Stop for a minute and think about all the things only you can access with your login credentials that no one else has access to. Do you really want someone else to be able to access those things? Think about how embarrassing, uncomfortable or alarmed you would feel if a colleague or friend started exploring. I know what you are thinking, I can trust them. They wouldn’t do anything malicious with my account.
Regularly we hear about horror stories of friendships gone wrong, bitter colleagues, bad breakups and the resulting fallout. When things go bad it is impossible to predict how someone will react. You would be unpleasantly surprised to know the damage that has been caused when these things occur.
Even if letting someone else use your account doesn’t result in data armageddon, it is against the Acceptable Use of Computing and Communication Resources Policy. The good news is there is no reason to do so. IT Services can arrange access for anyone for any reason. We have a solution for every situation. Find yours in the Credential Use Guidelines. If you aren’t sure what to do, just call the IT Service Desk and let them know what your time frame is. They will get back to you right away and provide you with a solution.
Don’t give up control by logging in for someone else. Reserve your account for your use only, not the other 114 people who are looking for access.
Logging into a machine or account and then letting someone use it is against our AUP – 10/29/19
This quarter our main message has been Keep your Password Secret. The reason is, sharing your password is against our Acceptable Use Policy (AUP) and puts yourself and our network at risk. The purpose of keeping your password secret is to prevent other people from having access to information and applications that they shouldn’t as well as to provide accountability.
Much to my surprise, it has been discovered that employees are logging into applications, workstations and systems with their own credentials and then letting someone else use those same applications, workstations and systems. While they are indeed keeping their passwords secret, they are still violating our AUP and exposing themselves to the same risks just as if they had just handed over their password. They risk is not just the loss of data, but also being held accountable for something that they did not do.
That is exactly what happened this week. A supervisor logged into an application using their credentials and then let their reports use the application. While one of the reports was using the system, they made changes to data they were not authorized to make. Because the supervisor’s credentials were used, they were questioned about the changes. The supervisor denies they made the changes, however there is no way to track who in fact made them.
I am also aware of similar situations occurring when guests are brought on campus. Some departments have been asking their administrative assistants to login to a workstation and then turn the workstation over to a guest speaker. This is also a violation of the AUP.
If you have a guest coming to speak on campus, they are required to bring their own laptop and then connect to the visitor WiFi, MRvisitor. If they do not have a laptop, they can borrow one from the library. At no point are visitors allowed to have access to our internal WiFi, MRsecure, our workstations or computers stored in smart cabinets.
Repeatedly sharing passwords or logging in and letting others use workstations or applications will result in your account being locked down. If you have any questions regarding the sharing of passwords or credentials, please refer to our AUP or contact the IT Service Desk at 403-440-6000.
Must Read – No we don’t have a secret email service – 04/23/19
A new phishing email is showing up in MRU Inboxes and Spam folders. It looks like this:

The first question you should ask is why would you receive an email about unread messages? However, if the panic over missing out on 2 messages throws common sense out the window, a glance at the sender’s email address should alert you. If you miss that clue and click on the REVIEW NOW link in a desperate attempt to avoid missing out, it takes you to this web page:

If you have gotten to this point, there is a good chance you will think that MRU has a secret email service outside of Gmail that you weren’t aware of. As a result, you will have no issues with entering your Mount Royal login credentials to access the mysterious messages. That is exactly what the hackers are hoping you will do. Once you do, Bob is your uncle, and they have control of your Gmail.
Let me assure you that the only email messages you will every receive from Mount Royal University will come through and be received via Gmail. You will never have to login to another email service to receive messages.
If this or a similar emails show up in your Inbox or Spam folder, delete them. If you ever have questions about the legitimacy of an email that you have received from us, please forward the email to abuse@mtroyal.ca and we will be happy to investigate for you.
What to do with email in your Spam folder – 04/23/19
At Mount Royal University, we now have lots of diligent users reporting phishing emails to abuse@mtroyal.ca. The IT security team is over the moon with the wonderful responses we are getting. However, we are getting quite a few that people find in their Spam folder. So I thought I would take a moment to explain how your Spam folder works and what to do with the emails that find their way there.
First off, for those who have no idea what I am talking about, your Spam folder is found in Gmail. Email that Google thinks is malicious or spam is sent there. Often its links and/or attachments are disabled or removed. Google determines if an email is malicious or spam using a variety of criteria. Examples of this criteria include containing known malware or phishing links.
Occasionally newsletters you subscribe to or emails from vendors can end up in the Spam folder by accident. That is why the emails aren’t deleted outright. You have the opportunity to scan through the folder and check and make sure nothing that you actually want to receive has made its way there.
As the Spam folder can fill up pretty quickly with hundreds of emails, I usually recommend that once a week you take a quick scan through your spam and then delete its contents. This prevents you from getting overwhelmed with an overloaded folder.
If you find a phishing email in your Spam folder, Google already knows about it and doesn’t need to be notified. However if you find one that is especially concerning and think the Mount Royal Community should be warned, please forward it to abuse@mtroyal.ca. When you do, let us know that it came from your Spam folder so we know who needs to be notified.
For more information about the Spam folder, how to mark or unmark messages as spam and other spam related questions, check out Gmail Help.
