Credential harvesting emails are hitting the campus hard. Here is how to protect yourself – 02/05/2024
What is credential harvesting?
Credential harvesting is a time honored hacking technique. Attackers send you an email that looks like a document share or they send an attachment with a document that contains a link. When you click on the link, you are asked to enter your login credentials to view the document. When you do, the attackers takes your credentials and sells them on the dark web or uses them for their own purposes. Either way, you have been compromised.
Credential harvesting red flags
Fortunately, there are some red flags that you can look for:
- The Fake Document Share – The email says that they are sharing a document with you, but the sending email address does not belong to a file sharing service like Google, Onedive or Dropbox. Check for look-a-like domains like googldriv.com and dr0pbox.com as well as the use of a personal email address.
- The ChatGPT Composed Email – If the grammar and spelling are correct but the language is odd, then you might be looking at an email created by ChatGPT. For example, the email says there is an attachment but gives you a link instead.
- The Google Form Credential Capture – If you access a shared document or click a link and it is a Google Form asking for your login credentials, close the form and report the email. Google Forms are easy for the attackers to set up, they come from the right domain and they don’t trigger anti-malware tools. This makes them an attackers favourite. Google forms are easy to identify, the bottom of the form is labeled.
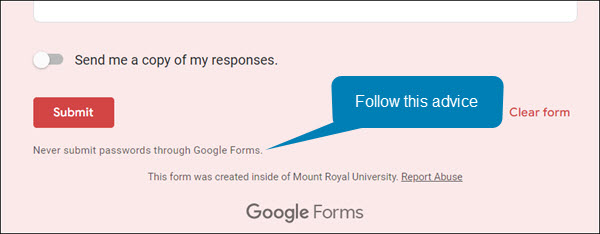
How to protect yourself
While looking for red flags can help, attacks are becoming so sophisticated that sometimes it is hard to find them. However, there are some things that you can do to protect yourself. If the email comes from someone at MRU and a personal email address has been used, you can send them an email to their MRU email address and verify it’s legitimacy. If the email comes from someone outside of MRU, it is best to call them on the phone and ask if they are trying to share a document with you.
The good news is you don’t have to confirm every document share that comes your way, just the ones that come out of the blue or seem odd. If you do fall prey and enter your credentials, quick action is essential. Email cybersecurity@mtroyal.ca immediately. We will walk you through next steps. Please don’t just change your password and get on with life.
Depending on the type of attack used, a keylogger may have also been installed on your machine. If you contact us, we can properly assess the situation and let you know if your machine needs to be reimaged. Otherwise, you will keep changing your password and they will keep stealing it.
Alert – Scammers user Flickr accounts in sextortion scam – 10/10/2023
Attackers are using compromised Flickr accounts to send email messages containing malicious links. The emails appear to list links to explicit images of the recipient. When they panic and click on the links to determine if the images are of them, malware is loaded onto their machine. The malware steals their login credentials.

If you receive an email demanding money and threatening to expose embarrasing or compromising images or information, report the email to IT Services using the PhishAlarm button. If the button is not available, you can report by forwarding the email to cybersecurity@mtroyal.ca. To remove the email from your inbox, report it to Google by clicking on the three dots in the upper right corner of the email and selecting Report phishing from the drop down menu.
Phone recharge led to wiping a laptop clean – 07/26/2023

Last week Carrie (not her real name) lost three days of productivity when her laptop had to be reimaged. For those of you who don’t know what reimaging is, it is when ITS has the pleasure of wiping everything off of your machine and then reinstalls the standard applications.
I know what you are thinking, “If they reinstalled everything, why did she lose three days of productivity?”. Simple, no one has just the standard applications with the default settings on their computer. Every department and every person has their own special applications and settings that allow them to do their job more effectively. It takes time to get your machine back to where it was before it was reimaged. In Carrie’s case, it was three days.
What caused all this inconvenience and frustration for Carrie? A stranger’s smartphone. Yup, you read correctly. A smartphone. When Carrie left for a two day vacation, she left her laptop tucked under the shelf of her standing desk plugged into the docking station. Carrie works in reception and she doesn’t have a door that she can lock. She thought if she just left it tucked out of the way, her laptop would be safe. Afterall, her department’s offices are behind doors that are locked every night.
While she was gone, her colleagues heard an alarm going off at her desk. When they investigated, they discovered the source of the alarm was a smartphone plugged into her laptop. They contacted Carrie to see if the phone belonged to her. When she assured them that it didn’t, they checked with the rest of the department. The smartphone didn’t belong to anyone there either. Security was called but they were unable to determine who the smartphone belonged to. Because there was no way to know if this was a malicious act or not, it had to be assumed that the smartphone had downloaded something nasty onto Carrie’s laptop.
The laptop was reimaged according to ITS security protocols. They require that If a device could be compromised, it is reimaged … period. Even if a malware scan finds nothing, we do the safest thing which is to wipe the machine clean.
Sadly, it is most likely that some MRU employee from another department innocently plugged their phone in for a quick charge and then forgot about it. In their rush, it never occurred to them they would be causing such grief.
This story is a reminder to everyone.
- If your phone needs charging, please use your own computer or the public charging stations around campus. DO NOT use a colleague’s computer.
- Secure your device as much as possible when you leave for the day. If you have a laptop. take it home or lock it away. If you have a desktop, lock your office door or make sure the common area door is locked.
- Do not store files on your desktop or C: drive, otherwise you will lose them if your machine has to be reimaged.
- If you find a strange device plugged into your machine, do what Carrie’s colleagues did, contact Security and ITS. Do not use your computer until ITS has determined it is safe to do so.
These simple steps will protect our network while saving you and your colleagues a lot of time and frustration.
What to do about those annoying pop-ups

It has happened to everyone, you visit a website and then shortly one or more pop-ups show up on your screen. Admittedly, with the availability of popup blockers this happens a lot less than it used it. However, it still happens. Those popups are not just annoying, they are often dangerous. Cyberattackers use them to trick us into downloading malware onto our machines.
While there are many ways attackers try to trick us. They have two favourite methods. The first is to fill the popups with pornography. There is nothing more horrifying than having naked people flash on your screen especially when you are at work. The idea is to make you panic so you will click on the X in the popup window to close it. It can be very effective. Anyone in that situation would do exactly as the attackers want and click to close the offending windows as quickly as possible. Unfortunately, once you click you download malware onto your computer.
The second method they like to use is the fake virus alert. The popups appear with flashing read text and flashing arrows directing you to click to remove a virus that they have detected on your machine. They are playing everyone’s worst nightmare in technicolor. It is understandable if someone panics and clicks. However, as before, once you do malware is loaded onto your machine.
The terrifying thing is popups can show up anywhere, not just on dodgy sites you have never visited. Legitimate websites can also be compromised by attackers. One day you are checking the Daily Kitty with no issues, the next day you visit and obscene images fill your screen.
The good news is, there is an easy way to get rid of the unexpected popups without downloading malware. The next time your screen comes alive with dozens of panic inducing popups, just close your browser. Don’t click on anything inside the browser window, just click the little x on the browser window itself and close the thing. Once the browser is closed, the problem is gone.
To make sure it doesn’t reoccur, don’t visit the website that you were on again. As long as you close the browser window and not the popup window, no harm is done. Even better, nothing else needs to be done. No report needs to be made to IT. You don’t have to scan your machine for viruses. You don’t have to spend the day wringing your hands hoping that you didn’t mess up. You can just enjoy the rest of your day in blissful serenity knowing that you stopped the criminals in their tracks.
Innocent looking webpage hides malware – A true story – 05/25/22

It was just another day for an MRU staffer. He was fielding calls and sorting through emails when he received an invite to a conference. He just needed to double check the session time. However, it was listed with a different time zone than his. It was early in the morning and his brain wasn’t fully functioning so he was unable to covert the time in his head. He Googled “time zone converter” and clicked the first link listed in the search results.
As soon as the webpage loaded, mayhem erupted on his computer. Three hundred and seventy four pop-ups appeared. Big scary alerts with flashing arrows pointing to a button said he had a virus. Click here said the button to remove the virus. You must click NOW flashed across the screen. Everything that could light up and flash was lit up and flashing. His computer screen looked like a slot machine that was about to pay out, only this pay out was malware not money.
He started to panic. He thought, “What do I do, what do I do? What did Bernadette say to do in training”. Then he remembered the first step.
Don’t touch anything
“Okay”, he thought, “I wont touch anything. what did she say to do next?”
Disconnect from the Internet
“Right.” He dug around behind his computer and yanked the network cable out from the back of it. “Okay, what is next?”
Contact the IT Service Desk
He picked up the phone and called the Service Desk. It took almost no time at all and a technician was there checking his computer. Thankfully, there was no harm done. Because he had followed his training and did not click on anything on the webpage the malware was never loaded onto his machine.
He was immediately grateful for the training he received. Had he forgotten to not touch anything on the screen, he would have lost a lot of his day and his data, getting his computer reimaged. While he knew the training was helpful, he didn’t realize just how much until he found himself experiencing a cyberattack. He was so glad he had taken his annual training. He was never going to consider it a waste of time again.
Restart your machine and save your data – 07/08/21
With the latest zero day threat PrintNightmare, putting printing on pause across the globe; it has become more important than ever to to keep your devices updated. While there is no update yet available to patch this vulnerability, it is a good idea to make sure your computer is ready when it is released.
The best way to do that is to ensure automatic updates on your Windows machine is enabled. MRU devices are automatically updated when you connect to the network so you don’t have to worry about them. This is a system setting controlled by ITS and it can’t be changed. However, you can mess with automatic updates on your home machine. You can pause them on a Windows 10 machine and turn them off all together on a Windows 8 machine. It is strongly recommended that if you have paused the updates or tuned them off , you enable them again. This ensures that as soon as the patch for PrintNightmare is available, it will be downloaded.
If you have a Windows 7 or older machine, the automatic updates feature is not an option, you will have to check for and download the update manually. For the most part, operating systems of this age don’t receive updates anymore and are vulnerable to attack. Which is why it is a good idea to upgrade to a newer one. The exception is when a really, really nasty vulnerability comes along. PrintNightmare falls into this category. Even Windows XP will receive a patch for this one. However, you Windows 98 and 95 holdouts are out of luck.
To complete the installation process, you have to restart your machine. This is true for MRU devices as well as your home machine. Depending on how your version of Windows is set up, you may or may not be notified that a restart is required. So it is a good idea to restart your machine daily. Daily restarts ensure that you both have the latest security patch downloaded and it has been installed as well. Also, it takes less time to restart a machine that has only one update to install versus one that has five. In just a few minutes you can save hours of heartache. Restart your machine and save your data.
MRU community hit by tech support scam – 04/29/21
The tech support scam is back. This week a MRU community member had a virus warning popup on their screen while they were working. The virus warning listed a phone number and appeared to come from Microsoft.
The individual phoned the Service Desk. However, when they couldn’t get through they called the ‘Microsoft’ number in the pop up. The fake Microsoft rep hung up on them when the caller didn’t provide the rep with the information they were looking for. Our MRU community member avoided being scammed simply by not being cooperative. However, had they been dealing with a more patient scammer, this could have gone very wrong very quickly.
This is a reminder if you see a dialog box with a virus warning and a phone number, it is a scam. Most likely there is no virus on your machine. instead, the website that you have visited has been compromised by a hacker to display a fake virus warning to anyone who views it. If this happens to you, close your browser and then open it again. Do not close the pop up. Do not visit that website again.
If you are concerned that your MRU issued device may have a virus, contact the Service Desk. Be patient, they will get back to you. If it is your personal device you are concerned about, run a virus scan. If something appears to be amiss and the virus scan does not find anything, take your device to a repair shop to have it checked.
Don’t take candy from strangers – 09/16/20
All malware is not created equal. This week a particularly devious piece landed in an MRU inbox. It was wrapped up in a zip file attachment. Here is what the malicious email looked like:
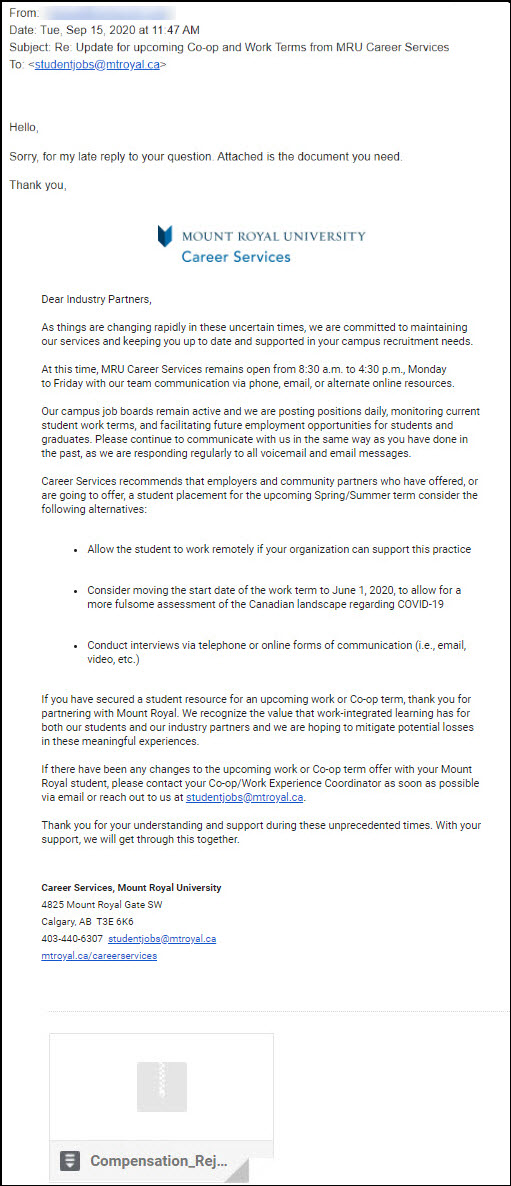
This malicious email is hard to identify as it contains a previously sent email thread. Interestingly enough, there is no human behind this email. It was sent by malware. When it gets on your machine it picks an email in your inbox and replies to it. Sending a copy of itself to an unsuspecting recipient.
The email is generic enough to work with pretty much any email. However it is the vagueness that flags it as suspicious. The other tell is the sender’s email address. Because this is malware and not a person sending out the email, the sender’s email address is incorrect.
If you decide to click and open the attachment, you see an Excel spreadsheet with this in the first cell.

If you missed the other two red flags, this one is your last chance to dodge the bullet. This very official looking graphic is asking you to enable editing and content to be able to “decrypt” the document It is also telling you what type of device to use to view it. Anytime you have this kind of instruction given to you to view a document, close it immediately and report it.
The instructions are not there to enable you to view the document. They are there to ensure the malware can be installed and will function. By asking you to enable editing and content, it is bypassing the safety controls we have in place to prevent the running of macros. It is not “decrypting” anything. If you can’t open a document just by clicking on it, consider it a threat.
This is another reminder how important it is to check the sender’s email address before you open an attachment or click on a link. If you recognize it, contact the sender using another method and confirm that they sent the email. If you don’t recognize it, don’t click. You wouldn’t take candy from a stranger, you shouldn’t take attachments from them either; no matter how enticing they are.

