An unlocked computer can be compromised in 30 sec or less
With educational records fetching up to $265 on the black market and competing nations trying to catch up in the knowledge race, higher education institutions have become prime targets for cyber attacks.
We are entrusted with a treasure trove of intellectual assets that attackers are constantly trying to gain access to. Locking your computer screen when stepping away, even momentarily, is an easy but effective way to protect them. This simple measure ensures that your academic work stays safe from prying eyes, maintaining the integrity of your research, student data, and other sensitive information.
Locking your computer screen is this easy
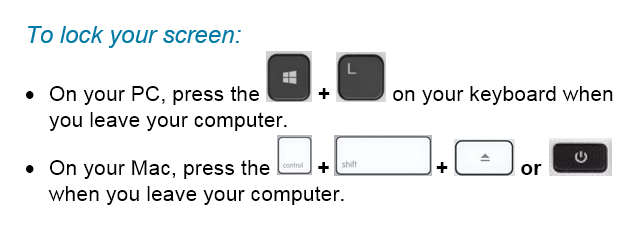
When you take the time to lock your screen, it not only prevents unauthorized individuals from gaining access to your data but it also demonstrates your professionalism and commitment to safeguarding the trust placed in you as a member of the Mount Royal community.
Developing the lock screen habit is easier if it is implemented into your regular routine regardless of where you are working and what device you are using. Lock your screen even when working from home or using your personal devices. This will help develop the habit. Everytime you stand up to leave your computer, remember this motto “Leave it? Lock it!”
By embracing this habit, you contribute to the resilience of the academic community against malicious actors attempting to profit at the expense of students privacy and academic research. Stay vigilant and protect your devices so that you can continue to help shape the minds of future generations.
Keep your devices updated with the latest security patches – 01/21/21
With criminals constantly coming up with new ways to hack into our systems, keeping your devices updated with the latest security patches is more important than ever. When you are on campus keeping your workstation up to date and secure is easy. Shut down your machine at the end of the day Friday and start it up Monday morning. However once you are working from home and your computer is always on keeping your machine updated isn’t so straight forward.
If you are remoting in to an MRU workstation you can’t shut it down. Instead, logout of the workstation and disconnect from GlobalProtect at the end of each work day. The updates are downloaded in the background as you work. Once you log out, your workstation is automatically restarted to install them.
If you have an MRU laptop assigned to you, it is setup to automatically download updates as you work. Once the updates are downloaded you are prompted to restart your machine to install them. As long as you don’t ignore the prompts, you are good to go. If you choose to ignore them and call the Service Desk for support, you won’t be helped until you restart your machine.
If you are using your personal computer, make sure you have automatic updates enabled on Windows/Mac OS and all your applications. From the Windows Start menu, select Settings>Updates and security to check your Windows update settings. On a Mac, select System Preferences>Software Update and click the Automatic Updates checkbox. Just like MRU laptops, updates are downloaded in the background and you are asked to restart your machine to install them.
Once you know what to do, installing your security patches is pretty easy. While it can be annoying, it is well worth your time. With a little bit of effort you make it exponentially more difficult for attackers to compromise your data and mess with your life.
Which email address to use when – 09/15/20
Who would have thought that 2020 would have everyone who can, working and taking classes from home? In a few short weeks we had to find a workspace, navigate chaos at home and learn a whole new set of skills. In the shuffle, it is easy to have work/school seep into our home life and vice versa. While it is normal to have this happen occasionally, as a general rule you should make sure you are using your email accounts appropriately. Here are a couple of tips that will help you sort through the work/school/home mess.
Use your MRU email only for work/school purposes
While this was a good idea before the pandemic, it is even more important now. Criminals know our home networks don’t have all the security bells and whistles that are on our corporate networks. Attacks are on the rise as they look for vulnerabilities. One of those is using your MRU email for personal purposes.
The more places you use your MRU email address the greater the chances you are going to reuse passwords and expose yourself to credential stuffing. As we are notified when your MRU email address has been used for a login credential of a breached account provider, we sometimes find out more about your personal life than we would like. Save us both the risk and embarrassment. If an account is for personal use, use your personal email address for your username.
Don’t use your personal email address for work/school
Since we have begun working at home, it feels like I have responded to 55.1 requests to view Google documents. The requests have come for quick reference guides, user manuals, registration forms, you name it. Every time I have had to reply with…
This document is only viewable by those with a Mount Royal email address. Please login to your Mount Royal email to access the document.
It gets mighty tiresome. I don’t know who the requester is unless they use their Mount Royal email address. For that reason, I do not grant non MRU email addresses access to documents. Everyone on campus should be following this protocol.
As important as it is to use your work email address to access documents, it is even more important for attending Google Meetings. Don’t make your meeting host guess who you are or whether you should be attending. Make it clear you are supposed to be participating by using your Mount Royal email address.
When you must use your MRU email address
To access some accounts, you must use your Mount Royal email address as a username. In these instances it is especially important to use a unique password. It prevents criminals from gaining access to your email by using a password that they have stolen from another account provider.
By following these simple rules you will decrease your vulnerability to cyberattacks, protect your privacy and make your colleagues, instructors and students lives easier. Happy days for everyone!
File management when working from home – 08/25/20
I know it is hard to believe, but it has been five months since all of us were sent home to work and attend classes. Being jettisoned into a working from home environment with little preparation has its challenges. With the lines between work/school and our personal lives being blurred, it is normal for our file management to become a little chaotic. The introduction of the new VPN service in the middle of all that certainly didn’t help. I helped over 51 people transition to GlobalProtect. Now that things have calmed down a bit and it is apparent we are going to be working from home for the foreseeable future, I thought a few file management tips would be helpful.
Give everyone their own profile on shared computers
Not everyone has the ability to have a separate computer for every member of the family. Often we have to share with others in the household. By creating a separate profile for each person, you limit what they can access. To use the computer they login to their profile which is secured with a password. What applications they can use and what documents they have access to depends on which user profile they are logging into. While this doesn’t completely protect your data, it does limit the damage that can be done. You can find more information on setting up user profiles on How To Geek.
Use a different browser for work
Keeping your work/school and personal life separate is not easy when you are using the same computer for both. If you have a personal Gmail account, you have seen how easy it is to accidentally send an email to your boss/instructor with your personal email address and save that report you were working on in your personal Google Drive. Both confuse your colleagues/instructors into thinking you are a hacker trying to gain access to the network. As well it makes it difficult for you to find things.
By using a separate browser for work/school, all your work bookmarks are in one easy to find place. In addition when you send an email or save a document, it will be your Mount Royal email and Google Drive login credentials that will be auto-filled rather than your personal ones.
Save your documents in Google Drive or the MRU Network
When we are in a hurry, it is easy to click the Save button and then put that document on the default drive. Unfortunately, that is often the C: drive or your desktop. If your hard drive crashes, the files will be lost unless you back them up onto another drive. In addition, if you are an employee due for a new machine, you will lose any data stored locally. Remember, IT Services does not back anything up when they replace your machine.
Make your life easier, save files on your MRU Google Drive. If you find the Google Drive too onerous to use, download Google Drive File Stream. It will add a G: drive to file explorer allowing you to save and open documents just like you do with the C: drive. A Mac version of Google File Stream is also available.
If you don’t like using the Google Drive, you can download files from the MRU network using Webfiles. Once your work is done, don’t forget to upload them back onto the network. Remember files left on your C: drive or desktop are vulnerable. Don’t leave them there.
Limit access to shared documents to those with a Mount Royal email address.
If you are sharing documents with colleagues, instructors or students; limit who can access them by choosing to share them with those who have a Mount Royal email address or a specific email address. This ensures that even if someone outside of the University community gets a hold of the link, they cannot access the document.
If someone requests access to this document later on, deny them access and remind them to use their Mount Royal login credentials to view it. This prevents hackers who are using a generic Gmail account from impersonating a colleague, instructor or student and tricking you into giving them document access.
If you have VPN access don’t download files to your home machine
Some employees need VPN access to remote in to their MRU workstation. If you have this type of access, you are working with sensitive data. That data must stay on the Mount Royal network. Do not download it to your machine at home.
Remember to give yourself a pat on the back
We are all working in less than ideal conditions trying to deliver ideal results. I hope these tips make that a bit easier. Don’t forget to give yourself a pat on the back for doing a great job. You rock!
How to video conference safely – 04/16/20

With everyone working from home, video conferencing has gone from being a novelty to being a necessity. Many of you are working virtually for the first time. With new experiences come new challenges. Mistakes are being made, that is to be expected.
To help you make your video conferencing experience as safe as possible, I have found these terrific tips from SANS on how to keep your data safe and prevent accidental expose of sensitive information. With a little knowledge, you can become a video conferencing security expert. As always, feel free to share this information with your family, friends and colleagues.
VideoConferencingTips-ForAttendees-1Pager
No Chrome doesn’t scan for viruses – 04/08/20

While it is a blessing that most of us are able to work from home, it has its downsides. One of those is the level of security on our home machines and networks. To take advantage of this less than ideal situation, cybercriminals are going into full swing. One of their favorite methods of attack is the compromised or malicious ad.
These ads can be placed on tons of web pages and appear to be like any other digital advertisement. However, they are far from benign. They contain malicious code that can do a variety of nasty things to your machine. Ransomware, key loggers and plain old viruses are just a few examples of the goodies these innocent looking adverts can hide.
The attack vector of choice, is to have these lovelies display some sort of dialog box when you visit the site to get you to click and download malware. Some creative cyberthugs have come up with a rather clever twist to this tactic, a fake virus alert. That’s right folks, you visit a website and after a bit of browsing a dialog box appears tell you that you have no less than 5 viruses on your machine. Just to make it look all official, the dialog box appears to be coming from Chrome itself.
Here’s the thing Chrome doesn’t scan for viruses, it is a browser. So if you are getting a virus alert from Chrome, it is definitely a scam. Close the browser and avoid the website. Stay alert out there. Use common sense and wash your hands.
Coronavirus based attacks are rampant – 03/19/20
As employees all over the world are working from home, criminals are ramping things up hoping to take advantage of the less secure networks that people tend to have at home. We have surges in phishing emails on campus and across the world related to working from home as well as an increase in malicious websites. It has gotten so bad the US Secret Service has issued a warning. Here are some things to watch out for.
The fake VPN
As employees struggle to setup a home office, they are signing up and downloading VPN services at record rates. While all of our employees have the advantage of using SRAS, many smaller organizations do not have their own VPN tool and are asking employees to install one on their home computer. If your spouse or roommate are in this situation, warn them to be very careful about what VPN they download. Cyberattackers are offering fake VPN services that download malware onto your machine in record numbers. Make sure they check reviews of the service to ensure it is reputable before they install it on their machine.
Fake COVID-19 trackers
As people attempt to live their lives and stay safe, many are turning to maps that track the location and incidence of infections. Criminals are getting wise and creating their own versions of these tracking websites that infect your computer with malware.
Some enterprising scammers have also created phone apps that supposedly track the infection rate but load your device with ransomware instead. Stick to well known and reputable websites such as Alberta Health Services and the World Health Organization to get your information about the virus and stay away from any apps related to it including ones that tell you how to get rid of it.
Phishing emails about working from home and COVID-19
Phishing email attacks are off the scale. Everything from fake emails from your organization about working from home, to offers of vaccines and cures. One of their favorites is fake GoFundMe pages with coronavirus victims pleading for medical help. Another is pretending to be a colleague who is quarantined and needs help.
You name it, the depraved are going to try it. During this time it is especially important to be vigilant. If you receive an email that doesn’t come from a Mount Royal email address, question its validity. While you are working at home, make sure you use your Mount Royal email address to send business correspondence. DO NOT use your personal email address. This will make it easier for your colleagues to stay safe.
Sources:
https://www.securityweek.com/researchers-track-coronavirus-themed-cyberattacks
https://www.securityweek.com/other-virus-threat-surge-covid-themed-cyberattacks
Authenticator apps, the good, the bad and the ugly 04/03/19
With compromised passwords floating around the dark web like masses of lemmings, two-factor authentication is moving from nice-to-have to a must. Unfortunately, the most commonly used second factor is a SMS text message. Although this method is easy for account providers to implement, it can also be compromised.
Fortunately, more and more account providers are recognizing this and they are integrating with authenticator apps. An authenticator app is a phone app that either generates an authorization code for you or provides the user with a prompt they can respond to. As the phone number is not used to deliver the code, the 2FA cannot be bypassed by a SIM swap.
There are several well known authenticator apps on the market. The top ones are Google Authenticator, Microsoft Authenticator, 1Password, LastPass Authenticator and Authy. All are free to try out. For the most part, they work pretty much the same way. You set them up by either scaning a QR code or entering a key to register your account with the app. When you go to login, the code appears in the app with a count down showing you how long it is valid for. You enter the code and shazam, you are in!
What sets them apart are the added features. Lets start with Google Authenticator. As it is free, simple to use. As it is by Google it is often highly rated by reviewers. However, the devil is in the details and one huge detail is you cannot backup your authenticator keys. This is a big problem if you get a new phone. It is also the reason why it is so poorly rated on the Apple Store. No one wants to spend days re-authenticating dozens of sites. This puts it squarely in the category of ugly.
Next up is Microsoft Authenticator. It works pretty much like the Google one for non Microsoft accounts. However, with Microsoft accounts you can use your phone’s biometrics or PIN to login instead of entering a password. This is a slick feature if you use a lot of Microsoft products and its free. Unlike Google Authenticator you can backup your authorization keys, but you must have a Microsoft account to do it. I put this one in the good category for Microsoft users and in the bad category for everyone else.
On to 1Password. This app is actually a password manager with an authenticator built in. If you are looking for a full feature password solution, this would be your tool. It is free to try, but you have to purchase it once your trial is over. Like the Microsoft app you can backup your keys and it generates authentication codes for its second factor. This one is also rated good.
We finally arrive at my favorite, LastPass Authenticator. The free version functions on its own like the Microsoft and Google products. However, if you purchase the LastPass password manager you can backup your keys plus you get this nice little feature that lets you respond to a prompt instead of entering in a code. Winner, winner chicken dinner!! No more entering codes puts this one at the top of my list. Not only is it a full feature password solution, but it makes securing your accounts way less work.
Lastly, is Authy. This little app is free to use, does the job and you can backup your codes. It is a solid solution that is always highly rated. if you don’t want to pay for an authenticator, this is your app. It definitely falls on the good side.
As determining which app is better for you can largely depend on your personal likes and dislikes I recommend you try them out before you commit long term.
On a final note, although authenticator apps may be more secure they still use your phone for the authentication process. If you lose your phone or forget it, you won’t be able to get into your account. Therefore before you enable any type of phone based two-factor authentication, make sure you can print off backup codes and store them in your wallet or purse. If you lose or forget your phone, you can use the the codes to get into your account. Not all accounts have backup codes, the LastPass password manager is one of them, so do your homework before you enable 2FA.
Why enabling two-factor authentication is more important now than ever – 02/28/19
Two-factor authentication (2FA) and it’s cousin, two-step verification is available on a variety of accounts such as Google, Facebook, LinkedIn, Yahoo, Twitter and Instagram. When it is enabled, after you successfully enter your password on a strange computer you are asked to respond to a prompt or enter a verification code sent to your phone. This ensures that even if your password is compromised, your account will stay secure. That is unless the criminal has your phone as well.
If that is the case, you are having one heck of a day and require support that is outside the scope of this article. I hope your phone is password protected and I wish you good luck. I digress. Back to why enabling 2 FA has become so important.
Last month we saw enormous lists of login credentials popup on the dark web. While previously miscreants had to purchase this valuable information, these large collections of usernames and passwords are now available for free. Aspiring Kevin Mitniks the world over can now try their hand at cybercrime, no upfront credential purchase needed.
As a result we have seen a big jump in credential stuffing attacks. Some of them on home security cameras with terrifying results. Ideally you should have a unique password for each account. However if this particular habit has not yet been entrenched, two-factor authentication will save your bacon
Although registering your email on Have I Been Pwned, will let you know if your password has been compromised, it takes time before a data breach shows up on their radar. With 2FA as soon as you receive a verification code or prompt on your phone, you know someone has stolen your password. This early warning system allows you to change the passwords on your accounts that don’t have 2FA before any damage is done.
Hopefully I have convinced you that two-factor authentication is no longer something that is nice to have, but is essential to securing your data. The next question is, “How do I start using it?”. Thankfully, there is this really great quick reference guide that walks you through the steps on how to enable 2FA on your Mount Royal email account. And yes, I wrote it…that’s why it’s really great. If you have any questions or need some help with the process, please feel free to contact me.
You can also come down to Main Street on March 13, April 10 or May 7. I will be there with my prize wheel. If you talk to me about two-factor authentication, you can spin and win.
What is credential stuffing and why should you care? – 02/14/19
Credential stuffing is where hackers take a list of usernames and passwords and use them to try and login to a site. They use computer programs that allows them to test thousands of login credentials in minutes. If someone is reusing passwords or using common or weak passwords they will have no problem accessing those accounts.
So how do you protect yourself against credential stuffing?
- Use unique passwords for every account. I know it is inconvenient and a pain but it really is the only way to protect yourself.
- Use a password manager. This takes the sting out of my first recommendation. Password managers not only store your passwords, but make generating them and logging in a breeze.
- Register with haveibeenpwned.com. If you register your email with them, they will email you when your email address shows up in a data breach. If you are still reusing passwords, this gives you time to change it. Credentials stolen in data breaches often show up on the dark web for sale before the breached company even knows their user’s data has been compromised.
- Enable multi-factor authentication on every account that has it available. Multi-factor authentication and its cousins two-step verification and two factor authentication requires you to enter an authentication code, respond to a prompt from an authentication app or insert an authentication key when you enter your password.
Updated 03/01/22
