Student Sponsorship dodges a gift card scam – 02/09/2024

Spoofing is when an attacker sends an email that appears to come from someone you know. We have seen this attack method used to target the MRU community before. This time, the target was Student Sponsorship and the attacker was spoofing a well known sponsor. Here is the original email they received.
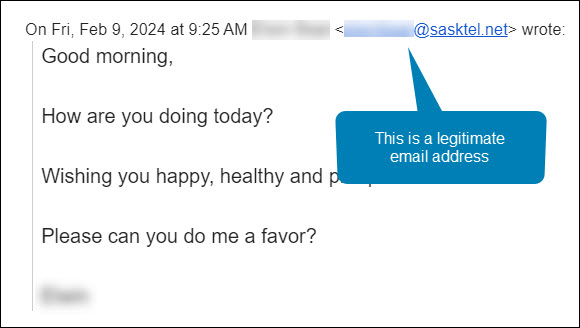
Maha was manning the Student Sponsorship inbox that morning. She was very familiar with both the sender’s name and email address. She hit the Reply button and asked the sponsor how she could help. Here is her response.
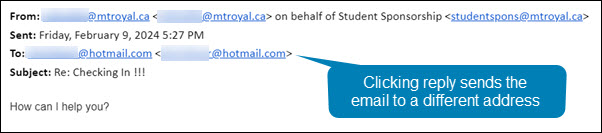
Notice how even though she hit reply, the email address in the To: field is no longer an @sasktel.net email address, but is now an @hotmail.com email address. This could only happen if the sender had edited the email header information so that the displayed sender email address was different than the replied to email address. In other words, they spoofed the legitimate email address.
There are legitimate reasons why this may be done. For example, a company wants to send with one email address to increase deliverability and a second one to receive emails because it is easier to remember. However, both emails will have the same domain name (the name that appears after the @). In this case, the second email address was created by a generic email provider. This is the reply that Maha got back.
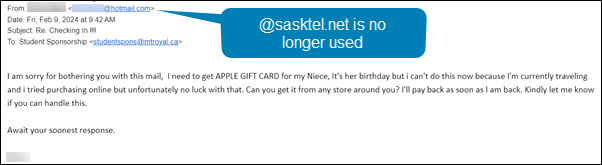
This confirmed her suspicions that something wasn’t quite right. The response she received back was no longer using the @sasktel.net email address and was asking her to make gift card purchases, it was a gift card scam. She forwarded the email to cybersecurity@mtroyal.ca immediately. Her quick actions saved her hundreds if not thousands of dollars.
When replying to emails, take a quick peek at the To: field. If the email address is different than the one that sent the email, proceed with caution. Someone may be trying to steal your money and/or your data.
Credential harvesting emails are hitting the campus hard. Here is how to protect yourself – 02/05/2024
What is credential harvesting?
Credential harvesting is a time honored hacking technique. Attackers send you an email that looks like a document share or they send an attachment with a document that contains a link. When you click on the link, you are asked to enter your login credentials to view the document. When you do, the attackers takes your credentials and sells them on the dark web or uses them for their own purposes. Either way, you have been compromised.
Credential harvesting red flags
Fortunately, there are some red flags that you can look for:
- The Fake Document Share – The email says that they are sharing a document with you, but the sending email address does not belong to a file sharing service like Google, Onedive or Dropbox. Check for look-a-like domains like googldriv.com and dr0pbox.com as well as the use of a personal email address.
- The ChatGPT Composed Email – If the grammar and spelling are correct but the language is odd, then you might be looking at an email created by ChatGPT. For example, the email says there is an attachment but gives you a link instead.
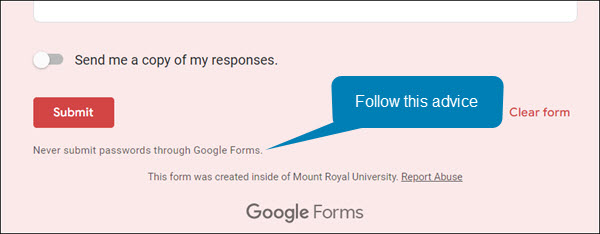
- The Google Form Credential Capture – If you access a shared document or click a link and it is a Google Form asking for your login credentials, close the form and report the email. Google Forms are easy for the attackers to set up, they come from the right domain and they don’t trigger anti-malware tools. This makes them an attackers favourite. Google forms are easy to identify, the bottom of the form is labeled.
How to protect yourself
While looking for red flags can help, attacks are becoming so sophisticated that sometimes it is hard to find them. However, there are some things that you can do to protect yourself. If the email comes from someone at MRU and a personal email address has been used, you can send them an email to their MRU email address and verify it’s legitimacy. If the email comes from someone outside of MRU, it is best to call them on the phone and ask if they are trying to share a document with you.
The good news is you don’t have to confirm every document share that comes your way, just the ones that come out of the blue or seem odd. If you do fall prey and enter your credentials, quick action is essential. Email cybersecurity@mtroyal.ca immediately. We will walk you through next steps. Please don’t just change your password and get on with life.
Depending on the type of attack used, a keylogger may have also been installed on your machine. If you contact us, we can properly assess the situation and let you know if your machine needs to be reimaged. Otherwise, you will keep changing your password and they will keep stealing it.
New employees being targeted by the gift card scam – 11/02/2023

Universities are seeing another increase in gift card scams. However, this time they are targeting new employees. Those new to the University are unaware of policies and procedures around gift cards as well as the reporting structure. This makes them an easier target for criminals.
This is how the scam works. Attackers scan LinkedIn for those announcing they have started a new position at a university. Then they research the university and find the people most likely to be the new employee’s supervisor/chair/dean. They use this information to craft a very convincing email asking if the new employee is available.
Once the employee responds, they ask them to purchase gift cards for an employee reward program or some other plausible reason. The fake supervisor/chair/dean is usually in a “meeting” and only reachable by email. They add this detail to discourage the new employee from trying to reach the impersonator by other means.
If you are a new employee, be aware that no one at MRU will ask you to purchase gift cards with your own credit card. Suspicious emails that you receive can be reported by using the PhishAlarm button or by forwarding it to cybersecurity@mtroyal.ca
If you have a newer employee on your team, please let them know about this scam. Encourage them to contact their supervisor/chair/dean by phone or in person to confirm any requests to purchase gift cards. Your advice could save someone thousands of dollars.
Alert – Scammers user Flickr accounts in sextortion scam – 10/10/2023
Attackers are using compromised Flickr accounts to send email messages containing malicious links. The emails appear to list links to explicit images of the recipient. When they panic and click on the links to determine if the images are of them, malware is loaded onto their machine. The malware steals their login credentials.

If you receive an email demanding money and threatening to expose embarrasing or compromising images or information, report the email to IT Services using the PhishAlarm button. If the button is not available, you can report by forwarding the email to cybersecurity@mtroyal.ca. To remove the email from your inbox, report it to Google by clicking on the three dots in the upper right corner of the email and selecting Report phishing from the drop down menu.
How to mark an email as unread on your phone – 07/18/2023
When reading an email on your phone, it is challenging to determine if the email is malicous or not. The screen is just too small to see the red flags, increasing the chances you will become a victim of a cyberattack.
Reading an email on your phone is perfectly safe. However when you are asked to take action, mark the email as unread and read it again later on a larger screen. While this is great advice, how exactly do you mark an email as unread on the Gmail app?
To mark an email as unread on the Gmail app:
- Open the email
- Click on the envelope in the upper right hand corner
Smart employee sees a correct email address and verifies anyway – 06/20/2023
Payroll was hit repeatedly this week with change bank requests. The requests looked legitimate. They came from a Mount Royal employee and the email address displayed was correct.
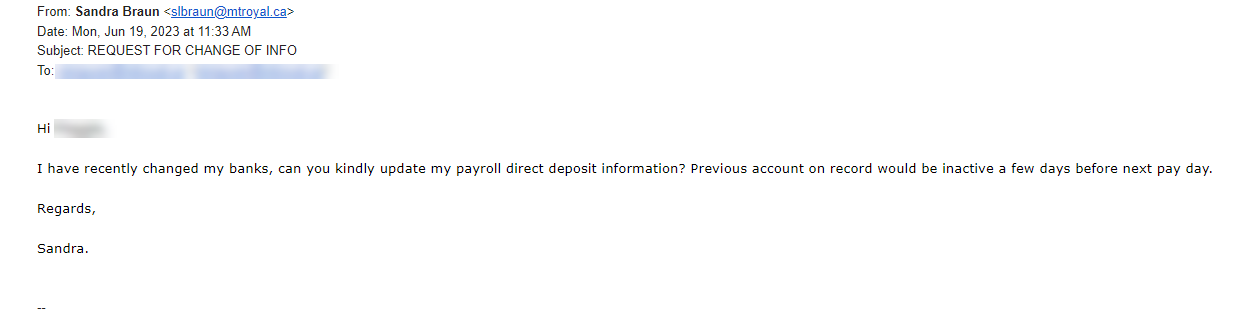
Fortunately, this wasn’t Payroll’s first rodeo and they knew that the sender’s email address was just a text field. An attacker could easily enter anything they like into that field. They also knew to verify that the request was actually made by the displayed sender. For this reason, they created a new, second email with a screen shot of the one received and asked the displayed sender if they had in fact sent the email. The answer was no.
Payroll’s quick thinking saved themselves and their colleagues days of heartache and a whole lot of money. This is a great illustration of why it is so important to verify that an email is legitimate before you act on it, even if the sending email address is correct. Just by taking a few extra minutes to send a new message, text or call; you can avert disaster and save the day just like Payroll did.
Campus slammed with fake performance reviews and faculty bonuses – 06/15/2023
This past week was a busy one for the cybersecurity team. The campus was slammed with document share invites from Google that were designed to look like they came from campus chairs and supervisors . Here is an example of one of the emails.

While it clearly states, in big letters at the top, that Benjamin Clark is sharing the document, the document description says that it is Ranjan Datta who is doing the sharing. This can confuse you just enough to make you open the file. If you do, you will be asked to enter your Google login credentials before you are able to view the document. Once you enter your login credentials, you are indeed able to view it. However, your login credentials will have also been sent to the attackers. If the attackers are clever enough, you aren’t even aware that anything is amiss.
Fortunately, It is fairly easy to spot these impersonators if you pay attention to what Google is saying and ignore the description that the attacker has entered. Google will always post the name and email address of the person sharing the document in big letters at the top of the email. In addiition if that person does not have a Mount Royal email address, a pale yellow banner appears above the Open button letting you know. In comparision, the description is in a normal size text and appears just above the name of the shared file.
By taking a pause and analyzing the email, you can avoid having your email compromised. That said we are all human and make mistakes. If you think your login credentials may have been stolen, change your password immediately by visiting the MyMRU login page and clicking the Change Password link.
If you find one of these suspicious looking emails in your inbox, please report it using the PhishAlarm button or by forwarding it to cybersecurity@mtroyal.ca. Your quick actions allow us to alert your colleagues and prevent them from becoming victims.
Why reporting phishing emails matters- 05/18/2023

You see them on a regular basis. They arrive in your inbox asking you to click on a link, open an attachment or provide personal information. If you do, you lose your data, gain a virus or your money disappears. These pests in our inbox are called phishing emails. Cyber criminials fill them with tempting bait like invoices, delivery notifications and offers of free money.
Gratefuly, these annoying emails only appear periodically. It is unusual to get more than 7 in a week. You can thank IT Services for that. They use a variety of hardware and software tools to detect this pestilence and remove it. As a result, the majority of phishing emails never even make it to your inbox.
Unfortunately, ITS can’t keep 100% of malicious emails out of your inbox. If they did set up those types of defenses, you wouldn’t receive any emails at all. They must leave some leeway to allow legitimate emails to be delivered. Phishing emails get through because the defense tools consider them to be legitimate until they are identified and flagged as malicious. The only way these emails get flagged is if you report them.
There are actually three ways to report an email. First, there is the PhishAlarm button. This button is located in the right side panel of the Gmail window. When you open an email, you will see the button appear. Click the button, click Report Phish and you are good to go. Reporting this way isn’t just easy, it also captures information from the email header and includes it in the report so it is easier for ITS to analyze the email.
Unfortunately, not everyone has access to the PhishAlarm button. If you are not an employee of MRU, you won’t see it. Therefore we have a second way for you to report. You can forward the email to cybersecurity@mtroyal.ca. Using this method is a little more work and we don’t receive the same information about the email but at least we are notified so your colleagues can be too.
Lastly, you can also report the email directly to Google. It takes a little more effort, you have to click the three dots in the upper right hand corner and then select Report Phishing from the menu. However, once Google receives the report they can flag the email. If enough people flag it, it gets pulled from inboxes. Google also adds the email to its blocked list so future versions are kept out of inboxes entirely.

If you just delete a phishing email and don’t report it, we can’t notify others of the threat and Google can’t block it or pull it from inboxes. As a result, it continues to be a threat to your colleagues, family and friends. Email reporting is an essential part of our defenses. We can’t fight the cyber criminals without you. Regardless of what method you use, please report phishing emails.
Checking an email? Get a bigger screen – 12/08/2023
Updated 07/18/2023

Phishing emails are the bane of our existence. They take our precious time as we slow down to take a close look and make sure that email from our colleague is really coming from our colleague. This whole experience is a lot more challenging when we are attempting to do our analysis on a smartphone.
While reading an email on our phone is perfectly harmless, things can become dangerous when the email asks us to take action. To click or not to click? Do we send the requested information or not? How is one to know when it is hard to see the link URL or sender’s email address on that small screen?
It is so challenging to spot a malicious email on a phone, that even IT professionals get tricked. That’s right … Information Technology professionals get tricked. The people that get tricked repeatedly in IT are ALL trying to see phishing red flags on a smartphone screen and fail.
The next time you read an email on your phone that has a link, contains an attachment or is asking for sensitive information, mark it unread. When you are able to view it on a larger screen; re read it and look at the sender’s email address , hover over the links and check the grammar. While taking the extra time is inconvenient, it is far less painful than loosing half a day of work while you factory reset your phone or deal with the fallout of a data breach.
Emails that appear to come from MRU can be malicious – 11/30/2022


