An unlocked computer can be compromised in 30 sec or less
With educational records fetching up to $265 on the black market and competing nations trying to catch up in the knowledge race, higher education institutions have become prime targets for cyber attacks.
We are entrusted with a treasure trove of intellectual assets that attackers are constantly trying to gain access to. Locking your computer screen when stepping away, even momentarily, is an easy but effective way to protect them. This simple measure ensures that your academic work stays safe from prying eyes, maintaining the integrity of your research, student data, and other sensitive information.
Locking your computer screen is this easy
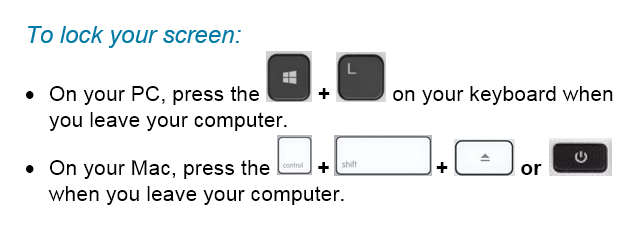
When you take the time to lock your screen, it not only prevents unauthorized individuals from gaining access to your data but it also demonstrates your professionalism and commitment to safeguarding the trust placed in you as a member of the Mount Royal community.
Developing the lock screen habit is easier if it is implemented into your regular routine regardless of where you are working and what device you are using. Lock your screen even when working from home or using your personal devices. This will help develop the habit. Everytime you stand up to leave your computer, remember this motto “Leave it? Lock it!”
By embracing this habit, you contribute to the resilience of the academic community against malicious actors attempting to profit at the expense of students privacy and academic research. Stay vigilant and protect your devices so that you can continue to help shape the minds of future generations.
Restart your machine and save your data – 07/08/21
With the latest zero day threat PrintNightmare, putting printing on pause across the globe; it has become more important than ever to to keep your devices updated. While there is no update yet available to patch this vulnerability, it is a good idea to make sure your computer is ready when it is released.
The best way to do that is to ensure automatic updates on your Windows machine is enabled. MRU devices are automatically updated when you connect to the network so you don’t have to worry about them. This is a system setting controlled by ITS and it can’t be changed. However, you can mess with automatic updates on your home machine. You can pause them on a Windows 10 machine and turn them off all together on a Windows 8 machine. It is strongly recommended that if you have paused the updates or tuned them off , you enable them again. This ensures that as soon as the patch for PrintNightmare is available, it will be downloaded.
If you have a Windows 7 or older machine, the automatic updates feature is not an option, you will have to check for and download the update manually. For the most part, operating systems of this age don’t receive updates anymore and are vulnerable to attack. Which is why it is a good idea to upgrade to a newer one. The exception is when a really, really nasty vulnerability comes along. PrintNightmare falls into this category. Even Windows XP will receive a patch for this one. However, you Windows 98 and 95 holdouts are out of luck.
To complete the installation process, you have to restart your machine. This is true for MRU devices as well as your home machine. Depending on how your version of Windows is set up, you may or may not be notified that a restart is required. So it is a good idea to restart your machine daily. Daily restarts ensure that you both have the latest security patch downloaded and it has been installed as well. Also, it takes less time to restart a machine that has only one update to install versus one that has five. In just a few minutes you can save hours of heartache. Restart your machine and save your data.
Use digital signatures with caution – 04/15/21
With everyone avoiding contact with other people at all costs, the use of digital signatures has become more common. However, some forms of digital signatures are more secure than others.
Services like Adobe or Docusign encrypt your digital signature. This means if someone tries to access it without your password, all they will see is gobbly gook. As long as you are careful with your passwords, your signature is secure with these types of services.
Other solutions for digital signatures are not as safe. Pictures of your written signature stored unencrypted or emailed can easily be stolen. If they are on your Google Drive, Onedrive or Dropbox this makes them even more vulnerable. Likewise, entering your signature into text fields in unencrypted forms is also dangerous.
Remember that your digital signature is used to verify your identify. You should treat it like you do your credit card number. If you wouldn’t store or transmit your credit card number using a particular method or service, then you shouldn’t store or transmit your signature that way either.
Keep your devices updated with the latest security patches – 01/21/21
With criminals constantly coming up with new ways to hack into our systems, keeping your devices updated with the latest security patches is more important than ever. When you are on campus keeping your workstation up to date and secure is easy. Shut down your machine at the end of the day Friday and start it up Monday morning. However once you are working from home and your computer is always on keeping your machine updated isn’t so straight forward.
If you are remoting in to an MRU workstation you can’t shut it down. Instead, logout of the workstation and disconnect from GlobalProtect at the end of each work day. The updates are downloaded in the background as you work. Once you log out, your workstation is automatically restarted to install them.
If you have an MRU laptop assigned to you, it is setup to automatically download updates as you work. Once the updates are downloaded you are prompted to restart your machine to install them. As long as you don’t ignore the prompts, you are good to go. If you choose to ignore them and call the Service Desk for support, you won’t be helped until you restart your machine.
If you are using your personal computer, make sure you have automatic updates enabled on Windows/Mac OS and all your applications. From the Windows Start menu, select Settings>Updates and security to check your Windows update settings. On a Mac, select System Preferences>Software Update and click the Automatic Updates checkbox. Just like MRU laptops, updates are downloaded in the background and you are asked to restart your machine to install them.
Once you know what to do, installing your security patches is pretty easy. While it can be annoying, it is well worth your time. With a little bit of effort you make it exponentially more difficult for attackers to compromise your data and mess with your life.
How to video conference safely – 04/16/20

With everyone working from home, video conferencing has gone from being a novelty to being a necessity. Many of you are working virtually for the first time. With new experiences come new challenges. Mistakes are being made, that is to be expected.
To help you make your video conferencing experience as safe as possible, I have found these terrific tips from SANS on how to keep your data safe and prevent accidental expose of sensitive information. With a little knowledge, you can become a video conferencing security expert. As always, feel free to share this information with your family, friends and colleagues.
VideoConferencingTips-ForAttendees-1Pager
Must Read – How to print sensitive documents on public printers – 03/07/19
Just don’t. Okay, I admit I am being rather unreasonable. However if you have any other alternative to printing tax receipts, pay stubs, benefits statements and the like, please use it. We are human beings after all and we get distracted. On a regular basis our techs pick up abandoned print jobs with sensitive information that should not be on public display. Here is the latest one.

With the tax season in full swing, we are seeing a lot of these types of documents left abandoned by their owners. If you do not have any other means of printing sensitive documents other than using public printers, please take the following precautions:
- Check twice to ensure you are sending the print job to the correct printer.
- Be standing by the printer as the document is being printed.
- If the document does not print, assume you have sent it to the wrong printer and immediately look for it. Do not attempt to print the document again until you are 100% sure it has not been sent to another printer.
Taking these simple inconvenient steps will help prevent miscreants from using your student number, SIN or other personal information for their gain and your misfortune. It will also keep how much you earn from being the latest water cooler gossip.
Do you know how much of your personal information is on the web? – 01/11/19

January 28th is Data Privacy Day. It is a day dedicated to taking a closer look at how much of your personal information is on the web. This is a great time to Google yourself and find out what shows up. As Google tailors your search results based on your previous activity, this exercise is more effective on a computer you haven’t used before. If you find the search results are showing more information about you than you are comfortable with, go into your accounts and change your privacy settings.
This exercise is also a great way to be reminded of old accounts that you have forgotten about and no longer use. As neglected accounts are more easily taken over by hackers, these accounts should be deleted. You may not need the account anymore, but I am pretty sure you wouldn’t want someone else using it to impersonate you. Things could get embarrassing or just plain awkward.
Although Data Privacy Day is a great time to check your online footprint. It is an exercise that you should do every few months. Those clever account providers are constantly changing their privacy settings. Each time they do, there is the possibility that something that was previously private is now public. By checking regularly you will make sure only the personal information that you want exposed is available to the public.
To help the Mount Royal Community out with their Data Privacy Day chores, I will be on Main Street January 31 from 10:00 am to 2:00 pm. Come down to see me and get googled on my computer. Everyone who does gets to spin the prize wheel and walk away with some swag. I will also be available to answer any questions that you have about privacy settings and minimizing your online footprint. See you there!!
How to navigate the tricky balance between security and convenience – 01/07/19
Every week I wade through a hundred news feeds. Two thirds of them containing tales of horror detailing the latest methods criminals are using to separate us from our data. The other one third are notices of privacy breaches by legitimate companies who knowingly misuse our data or are negligent in protecting it. With all the good news that I filter through, no one would fault me if I decided not to turn on a computer or touch a smart phone for the rest of my life. Yet I still manage to get up every morning, check my smartphone and work on a computer all day feeling at peace.
It isn’t denial that keeps panic at bay. It is being aware of what the risks are and mitigating them. Each time I interact with technology I look at what the real risks are, what the benefits of using it are and then determine whether the convenience outweighs the risk. Ultimately, it comes down to quality of life. If a piece of technology is going to significantly enhance my quality of life, then I consider the risks and do everything I can to reduce them.
Lets look at a smart thermostat as an example. I like to sleep in a really cold room. It would be awesome to be able to go to bed in a super cold room and wake up to a nice toasty one. However, I wake up at the same time every morning. So having a thermostat programmed to cool down at night and warm up during the day is sufficient. I don’t really need to connect it to the internet so I can lay in bed and change the temperature. It adds nothing to my quality of life. Sure it’s neat, but I won’t use that feature. It would however give criminals another access point to my network. For me, the risk of connecting the thermostat to the internet doesn’t merit the benefit.
Now lets look at my mom. Her body hurts if it gets cold. She too likes to sleep in a cold room. She is retired and wakes up at a different time every morning. For her being able to change the thermostat from her bed adds considerably to her quality of life. Yes there is a risk associated with it, but I have set her thermostat to update regularly and have changed the default password so the risk is minimal. For her the benefits of connecting the thermostat to the internet definitely outweigh the risks.
The risk vs benefit analysis applies to securing data as well, not just devices. Lets use password managers as an example. There is a small risk that a password manager could be hacked. However, if you reuse passwords or write them down the chances of the passwords being compromised is much greater than the chances of the password manager being hacked. In this case, the benefits of using a password manager far outweigh the small risk.
By keeping informed of what the technology risks are, how to mitigate them and using thoughtful analysis. You too can use technology and still sleep at night.
Browser extensions cause of Facebook data breach – 11/05/18
The BBC Russian Service has found data from 81 000 Facebook profiles sitting on the web. The data is apparently just a small sample of what was taken from 120 million accounts by a hacker selling his haul. It is hard to know if 120 million profiles were indeed hacked or if the breach is limited to what is currently on display. One would think that Facebook would notice 120 million profiles being accessed, so my guess is they don’t have much more than the small sample. After all, criminals aren’t known for their honesty.
Facebook is blaming malicious browser extensions. They are reporting that the extensions were monitoring user’s Facebook activity while shuttling personal information as well as private conversations to the hackers. The majority of information taken was from Ukrainian and Russian users, however profiles from all over the world were also pilfered.
This is a reminder to be wary of browser extensions. As with apps, only download ones that:
- You really need
- Have good reviews
- Have lots of downloads
- Come from reputable sites
Malicious browser extensions can be very difficult to detect as extensions update automatically. This allows hackers to create extensions that are harmless, until their first update. After that your handy extension starts doing all sorts of nasty things.
To reduce the risk, if you really need a particular browser extension consider disabling it when you aren’t using it. Lastly once you no longer need the extension, remove it from your browser.
Fake sites use HTTPS too – 10/04/18
As the holiday season approaches, people around the world are getting ready to cruise the internet looking for great gifts at bargain prices. As you do your online holiday shopping, keep in mind that sites labeled HTTPS guarantee your data is encrypted as it is transmitted between your computer and the web. It does not guarantee that the site is legitimate.
Criminals have gotten wise. They are now registering their fake web sites so they are tagged as HTTPS. So now instead of having to worry about your credit card information being intercepted as you purchase the iPhone XS Max for the unbelievable price of $300.00 USD, you can be confident that only the scammer is receiving your data.
So how do you know that a site is legitimate? Stick with retailers that you have used in the past and access their web sites using a bookmark or search result. If you receive an email with an offer, don’t use the link in the email. Visit the website directly.
If you are using a new retailer:
- Check reviews first. Avoid retailers with large numbers of complaints that haven’t been resolved.
- Always pay with a credit card or PayPal so you have a method of recourse should things go wrong.
- Remember to read all the terms & conditions of sale. Know if they have a return or exchange policy.
Lastly, remember…if it is too good to be true, it probably is a scam.
