Job scam landing in MRU inboxes – 05/13/19
The latest scam to make the rounds is an email that appears to offer the recipient an opportunity to apply for an admin position. It looks like this:
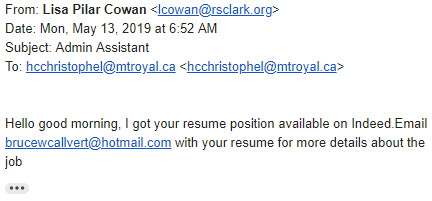
The email comes from the Vice President of an organization called the Robert Sterling Clark Foundation. It is a real organization and the sender’s email address appears to be legitimate. Most likely, the sender has had her email account hacked and the scammers are using it to send out these fraudulent emails. The poor grammar and hotmail email address are clues that something isn’t quite right.
Without responding to the email, it is impossible to know exactly what the scam is. However there are some standards tactics used. In the first one, once you send them your resume they offer you an interview but charge you a fee of several hundred dollars to participate. No company will ever charge you to be interviewed.
In the second tactic, you are either given an interview through text or email or just offered the job outright based on your resume. Once you accept the position, they send you a cheque. You are then asked to deposit the cheque into your account and then immediately transfer the same amount of money from your account to another. Of course in a few days their cheque bounces and your bank account is minus those funds.
No legitimate employer will offer you a job without a proper face to face interview. Nor is there a legitimate reason for an employer to send you a cheque and ask you to deposit it in your account only to have you immediately transfer it to another.
To protect yourself from job scams:
- Do not pay for an interview or for interview expenses.
- Do not accept a position that does not require a face to face interview.
- If you are asked to make purchases or transfer funds on your employers behalf, make sure any fund transfers or cheque deposits clear before you do so.
- Research perspective employers. Make sure you can reach your contact person through the company’s main contact number or email listed on their website. Check for reports of fraud involving the company.
Remember, if it seems too good to be true, it probably is. Just ask this woman from New Brunswick.
Another Rahilly phish making the rounds – 05/08/19
The gift card scammers are giving another go at trying to convince employees that our new president Dr. Rahilly is trying to contact them.

This time they have managed to get his name correct, replacing the much loved Tin with Tim. They have also changed up the email address going with presidant to make it look more official. Although if they had spelled it right, it would have been more effective.
This is just another attempt at a gift card scam. If you check the sender’s email address before you read the body of the email, you will be less likely to have emotion override rational thought and reply in haste. If you are contacted by the “presidant”, just delete the email.
Think you won’t ever be tricked? Think again. – 05/03/19
Mount Royal has been targeted by the gift card scam for months now. It seems like every month we receive a dozen or so reports of emails that appear to come from Mount Royal supervisors asking employees if they are available. The scammers hope they will get a response. Once they have one, they attempt to convince the employee to purchase gift cards and send them the redemption codes.
Last week the scammers came very close to being successful. A Mount Royal employee responded to the scammer and was about to go out and purchase gift cards as instructed when they thought they should double check with their supervisor’s admin. This sober second thought saved them hundreds if not thousands of dollars and a lot of embarrassment.
You are probably thinking you would never get sucked in like that. But dollars to doughnuts, that employee who responded thought the same darn thing. When our emotions get engaged, rational thought is bypassed. Hackers know this, that is why they create emails designed to do just that. You may think you cannot be tricked however when you receive an unexpected email that appears to come from your boss, your emotions get engaged. Rational thought is gone and all you want to do is follow instructions and make your boss happy.
So how do you defend against such an attack? When you open any email, the first place your eye needs to go to is the sender’s information. You need to engage rational thought before emotions can be triggered by what is in the rest of the email.
Check the email address and make sure it is legitimate. If the email address is not a Mount Royal address then you know it isn’t coming from your supervisor and it can be deleted. Only once you have established that the email address is correct do you read the email itself. Remember that the email may still be malicious. Just because it looks like it came from your boss, doesn’t mean it did. Their email may have been compromised. Look for red flags and if anything seems amiss contact your supervisor to make sure they did indeed send the email.
Must Read – No we don’t have a secret email service – 04/23/19
A new phishing email is showing up in MRU Inboxes and Spam folders. It looks like this:

The first question you should ask is why would you receive an email about unread messages? However, if the panic over missing out on 2 messages throws common sense out the window, a glance at the sender’s email address should alert you. If you miss that clue and click on the REVIEW NOW link in a desperate attempt to avoid missing out, it takes you to this web page:

If you have gotten to this point, there is a good chance you will think that MRU has a secret email service outside of Gmail that you weren’t aware of. As a result, you will have no issues with entering your Mount Royal login credentials to access the mysterious messages. That is exactly what the hackers are hoping you will do. Once you do, Bob is your uncle, and they have control of your Gmail.
Let me assure you that the only email messages you will every receive from Mount Royal University will come through and be received via Gmail. You will never have to login to another email service to receive messages.
If this or a similar emails show up in your Inbox or Spam folder, delete them. If you ever have questions about the legitimacy of an email that you have received from us, please forward the email to abuse@mtroyal.ca and we will be happy to investigate for you.
What to do with email in your Spam folder – 04/23/19
At Mount Royal University, we now have lots of diligent users reporting phishing emails to abuse@mtroyal.ca. The IT security team is over the moon with the wonderful responses we are getting. However, we are getting quite a few that people find in their Spam folder. So I thought I would take a moment to explain how your Spam folder works and what to do with the emails that find their way there.
First off, for those who have no idea what I am talking about, your Spam folder is found in Gmail. Email that Google thinks is malicious or spam is sent there. Often its links and/or attachments are disabled or removed. Google determines if an email is malicious or spam using a variety of criteria. Examples of this criteria include containing known malware or phishing links.
Occasionally newsletters you subscribe to or emails from vendors can end up in the Spam folder by accident. That is why the emails aren’t deleted outright. You have the opportunity to scan through the folder and check and make sure nothing that you actually want to receive has made its way there.
As the Spam folder can fill up pretty quickly with hundreds of emails, I usually recommend that once a week you take a quick scan through your spam and then delete its contents. This prevents you from getting overwhelmed with an overloaded folder.
If you find a phishing email in your Spam folder, Google already knows about it and doesn’t need to be notified. However if you find one that is especially concerning and think the Mount Royal Community should be warned, please forward it to abuse@mtroyal.ca. When you do, let us know that it came from your Spam folder so we know who needs to be notified.
For more information about the Spam folder, how to mark or unmark messages as spam and other spam related questions, check out Gmail Help.
Another variation of the MRU imposter phishing email – 04/02/19
Once again miscreants are trying to catch our employees off guard by hitting them with a phishing email that appears to come from a fellow Mount Royal employee. Fortunately for us, our employee identified the odd email address and stopped the attack cold.
The clever criminals added some distracting details to try and trip up their intended victim. They added a Re: to the subject line plus a fake time and date stamp to make it look like the email was a reply to a previously read email. They know we tend to trust email replies and they bet that the odd email address wouldn’t be noticed. They were wrong.
Our superhero employee saved the day by forwarding this bad boy to us instead of clicking on the nasty link. Keep a look out for this one.
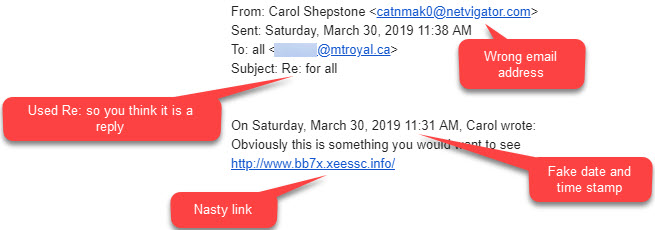
If it shows up in your inbox, be a superhero and forward it to abuse@mtroyal.ca.
Must Read – Mount Royal targeted with pdf containing malicious link – 03/25/19
The last few weeks there are been an unusually high number of targeted attacks on post secondary institutions. The latest phishing email shows a continuation of the trend. The email that arrives in your inbox looks innocent enough.

Innocent enough if you don’t notice the totally wrong email address. For fun, lets pretend that you did indeed ignore the email address and opened the attachment. You are presented with this document.

Once again the crooks are using a malicious link in a legitimate document to bypass the firewall and antivirus. Clicking the Open button takes you to a compromised website. As our firewall recognizes the malicious URL, I can’t tell you what awaits as the site is being blocked. However, from the email content I assume you will be given a fake login page for Outlook or OneDrive designed to steal your credentials. This is just a gentle reminder to check the sender’s email address before you click on a link or open and attachment.
Must Read – MRU inboxes receive malicious Google Drive file share 03/20/19
Another day, another clever criminal trying to break into our network. This time they tried using the Google Drive to do it. Tuesday morning several employees found this in their inbox.
The Word Doc link is totally legit. If you click the link, it takes you to this document.

Clicking the link in the Word document takes you to a legitimate website that has been compromised. The site asks you to login to Office 360 to access the document. Of course if you do, you are giving some miscreant your Office 360 login credentials. They can then sell your credentials on the dark web or use them themselves to wreak havoc on your data as well as the data of others. Fun, Fun, Fun.
Because the Google Drive file share and the website are legitimate, they won’t be flagged by anti-virus or the firewall. It is actually very clever. However although it may get by the technology, a person can easily spot this as malicious. In fact, we had two different reports sent to abuse@mtroyal.ca about this one. Way to go MRU!!
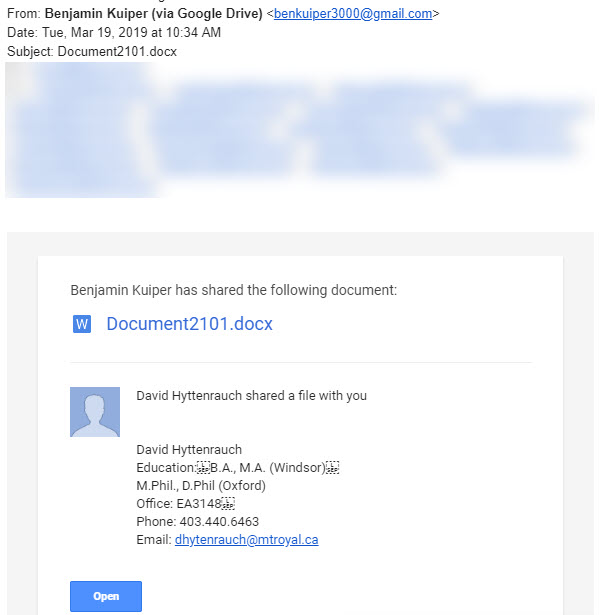
For those of you who aren’t already yelling at the screen, “Come on, that is so obvious”, I am going to walk you through the red flags. First one is the email is sent by Benjamin Kuiper from the email address benkuiper3000@gmail.com. Clearly not a Mount Royal email and he is not listed in the directory. Fail number one.
Second, the doc says it was being shared by Benjamin and David Hyttenrauch. This doc was sent to people on David’s team so even though they didn’t know who Ben was, they sure as heck knew who David was. This got the desired attention. However, you can’t send an invite to share one file from two people. Clearly, this Word doc was shared by Benjamin and the sneaky dude entered the rest of the deceiving information into the Add a note field in the Share with others dialog box to make it looks like Dave was involved. Fail number two.
Third, when you open the document it tells you that you have a file waiting for you on the OneDrive. OneDrive file shares are not sent with links in Word documents. Fail number three.
Lastly, if you were to hover over the link in the Word document you would see that it does not go to OneDrive. Fail number four.
As clever as criminals are, most of them can be stopped by alert employees who take the time to look at emails with links and attachments critically. As we have seen in this example, the majority of the time phishing emails contain clear clues that something is not right. Don’t get caught up in the emotion of the moment. Like our wonderful employees, take the time to really look and make sure that the email is what it appears to be. Your data, your colleagues and your IT department will thank you.
Why enabling two-factor authentication is more important now than ever – 02/28/19
Two-factor authentication (2FA) and it’s cousin, two-step verification is available on a variety of accounts such as Google, Facebook, LinkedIn, Yahoo, Twitter and Instagram. When it is enabled, after you successfully enter your password on a strange computer you are asked to respond to a prompt or enter a verification code sent to your phone. This ensures that even if your password is compromised, your account will stay secure. That is unless the criminal has your phone as well.
If that is the case, you are having one heck of a day and require support that is outside the scope of this article. I hope your phone is password protected and I wish you good luck. I digress. Back to why enabling 2 FA has become so important.
Last month we saw enormous lists of login credentials popup on the dark web. While previously miscreants had to purchase this valuable information, these large collections of usernames and passwords are now available for free. Aspiring Kevin Mitniks the world over can now try their hand at cybercrime, no upfront credential purchase needed.
As a result we have seen a big jump in credential stuffing attacks. Some of them on home security cameras with terrifying results. Ideally you should have a unique password for each account. However if this particular habit has not yet been entrenched, two-factor authentication will save your bacon
Although registering your email on Have I Been Pwned, will let you know if your password has been compromised, it takes time before a data breach shows up on their radar. With 2FA as soon as you receive a verification code or prompt on your phone, you know someone has stolen your password. This early warning system allows you to change the passwords on your accounts that don’t have 2FA before any damage is done.
Hopefully I have convinced you that two-factor authentication is no longer something that is nice to have, but is essential to securing your data. The next question is, “How do I start using it?”. Thankfully, there is this really great quick reference guide that walks you through the steps on how to enable 2FA on your Mount Royal email account. And yes, I wrote it…that’s why it’s really great. If you have any questions or need some help with the process, please feel free to contact me.
You can also come down to Main Street on March 13, April 10 or May 7. I will be there with my prize wheel. If you talk to me about two-factor authentication, you can spin and win.
Must Read – The MRU impersonators are ramping things up – 02/28/19
Phishing emails that appear to come from Mount Royal University supervisors are making their appearance again. This time they are throwing in the whole, “I am going into a meeting with limited phone calls, so just reply to my email” nonsense to try and keep you from calling the person directly to verify the legitimacy of the email.
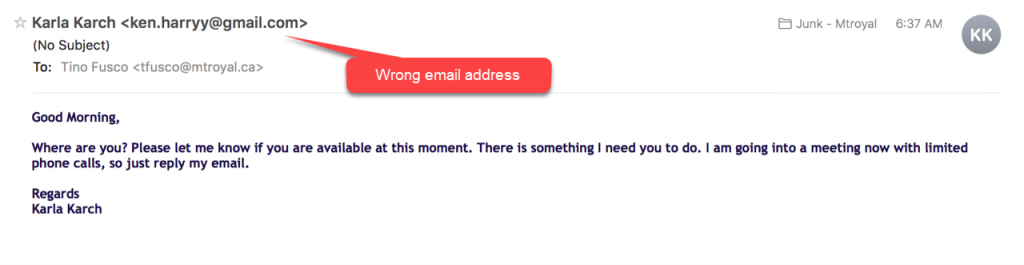
Thankfully they are still using lame sender email addresses, so they are pretty easy to spot if you take the time to look. However, they have started to use a new tactic that is concerning. They some how have gotten a hold of cell phone numbers and are now texting Mount Royal employees asking them to contact the texter immediately as they have a task for them. The messages appear to come from the employee’s supervisor.
How do you protect yourself from social engineering via text message?
- Don’t click on links in text messages
- Be suspicious of requests that are outside of regular procedures or processes
- Don’t give out information that the person you are talking to should already have
A good rule of thumb is, if it doesn’t feel right it probably isn’t. If you get a strange request from your supervisor, politely let them know you will get right back to them and hang up. Then contact them using an email or phone number that you know is legitimate.
