Use digital signatures with caution – 04/15/21
With everyone avoiding contact with other people at all costs, the use of digital signatures has become more common. However, some forms of digital signatures are more secure than others.
Services like Adobe or Docusign encrypt your digital signature. This means if someone tries to access it without your password, all they will see is gobbly gook. As long as you are careful with your passwords, your signature is secure with these types of services.
Other solutions for digital signatures are not as safe. Pictures of your written signature stored unencrypted or emailed can easily be stolen. If they are on your Google Drive, Onedrive or Dropbox this makes them even more vulnerable. Likewise, entering your signature into text fields in unencrypted forms is also dangerous.
Remember that your digital signature is used to verify your identify. You should treat it like you do your credit card number. If you wouldn’t store or transmit your credit card number using a particular method or service, then you shouldn’t store or transmit your signature that way either.
How to check your cybersecurity awareness training status 04/15/21
Reminders are going out for everyone to complete their cybersecurity awareness training. In response people are noticing they have no training assignments and are wondering if they have completed the training or not. These wonderful folks usually completed their training in October.
Unlike Blackboard, the new Security Education Platform doesn’t let you access modules once they are completed. They are removed from your assignment list. However you can still see what training you have completed by looking at your Report Card.
To access your Report Card, click on your name in the upper right hand corner of the platform window and then select My Report Card. It will show you the status of all your assignments.
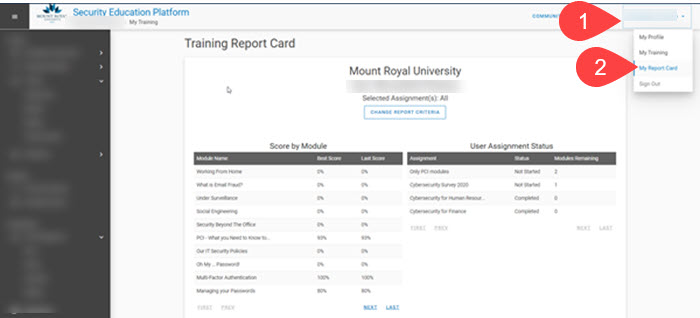
Please note that the name has been blurred out in this screenshot. In addition, you will see the cybersecurity survey in your assignment list. This survey is no longer available. Don’t worry if you didn’t complete it, it was optional.
I hope this helps those of you who can’t remember if you completed your training or not. If you have any other questions about the cybersecurity awareness training, please feel free to continue to contact me.
Google Chrome Privacy Settings you Should Check – 03/17/21
A while ago I posted an article on Data Privacy Day. Out of that article, several readers requested recommendations on privacy settings for Google Chrome. As much as I would love to tell readers to lock down everything and shut down the great Google data collection, privacy is a very personal thing. One person may be willing to give up functionality of their tools to ensure their private information stays private, while another is just fine with all knowing Google collecting their data if it means their life is easier. In short, I cannot tell you wonderful people what to lock down. Each one of you has to make that decision for yourselves.
That said, I can tell you what settings to check and where they are currently located. Google, just like most other service providers, likes to make them hard to find. A cynical person would say that was done on purpose. I have decided to be more positive today and I am going to blame poor interface design… I am trying here. Work with me.
Decide how your browsing history is used in Chrome
Most of the privacy goodies are hidden under Settings>Sync and Google Services. The first stop should be Control how your browsing history is used to personalize Search, ads and more. Click on the little square next to this monster and you find the Activity Controls.

At first glance, all you see is Web & App Activity. Scroll down a bit and click the See all activity controls link to find the motherload.

These settings determine how much functionality you want from Chrome vs how much data you want to keep from their prying eyes. It may take a few tries to find the right balance for you. Don’t be afraid to turn on some controls. You can always turn them off if they are making your life difficult. Personally I prefer to give them as little information as possible and find things on my own. I don’t like to be fed my content. You can stumble upon some pretty interesting stuff when you don’t have someone curating your content for you. However, that might not be your jam. Totally okay.
Further down the Sync and Google Services page, there are some other settings that you should check. Do you want to help Google be a better service, or send them your URLS or the text you type into the browser? Once again, try turning them off and see what happens to the functionality of Chrome.
Decide how you will be tracked
Cookies are used by websites to identify you for a variety of reasons. Some of them are useful like keeping track of what is in your shopping cart. Others are more concerning like tracking what you click on. As with all browsers, Chrome lets you decide what types of cookies are okay and which are to be disabled or blocked.
Chrome’s cookie settings can be found in Settings>Cookies and other data. I do not recommend selecting Allow all cookies or Block all cookies. However you may want to experiment with Blocking third party cookies.
Another setting you can consider is the Send a “do not track” request with your browsing traffic. As it suggests, it simply sends a request to a website that you not be tracked. How they respond to the request depends on the website. However, I feel better knowing that I have at least asked for some privacy. The odds that they honor that request are probably pretty slim. There I go being all cynical again. Sorry, I slipped.
Cover your tracks
Your browsing history including cookies, cached pages and autofill data can be cleared out manually or you can set it up to perform a cleaning at regular intervals. Ideally things should be cleaned out once a week, however the best cleaning interval for you depends on how you work. Do be aware that if you clean out cookies regularly, it may mean you have to re-enter things on sites over and over again. As with the other settings, experiment with it to find what works best for you. You can find these settings under Settings>Clear Browsing data.
Inconclusion
Even if you try out these settings and decide to not enable any of them, that’s perfectly okay. The important thing is you are aware of them and know how to change them. You are taking control and making decisions about your privacy instead of having them made for you.
Unfortunately, account providers regularly change their privacy settings and Google is no different. The information in this article may be out of date in a week, a month or tomorrow. Therefore, I suggest that every quarter you take a look at your privacy settings and make sure they are still at a comfortable level. A little proactivity goes a long way when maintaining your privacy.
Why is someone you know asking for your phone number? – 03/10/21
The MRU community have been finding emails in their spam folder similar to this one.

The email looks like it comes from a colleague or instructor. However the email contains some red flags. The biggest one being they are asking for your personal phone number. If they don’t already have it, they shouldn’t be asking for it. In addition, it was found in the Spam folder.
Google puts emails that it thinks are suspicious but they aren’t sure of into the Spam folder. If you see an email in your Spam folder, assume it is malicious and always confirm legitimacy with the sender before you respond. Confirmation is best done over the phone, however in situations like this where an MRU email wasn’t used, it is enough to contact the sender through an MRU email.
It is hard to say what the end game of this scam is. However, this is often step one in a gift card scam where they compel you to purchase gift cards and then give them the redemption codes. These redemption codes can then be sold on the dark web.
Let us know what you think of the Be a Superhero branding and earn contest entry codes – 03/01/21

The cybersecurity awareness program at MRU has been around for several years now. Throughout that time we have encouraged the campus community to Be Superheros by practicing cybersafe behavior. While the Be a Superhero branding has worked well for us, we are always looking for ways to make the program more engaging and effective.
We would like your feedback on our branding. Let us know if you still want to Be a Superhero or if it is time to leave our capes behind. You can find the survey here.
Everyone who completes the survey will receive a contest entry code for the Cybersecurity Challenge and a chance to win a $250 Best Buy gift certificate. As this is the last month to collect entry codes, this is a great way to get entries in and move your team forward.
It was Data Privacy Day, have you checked your privacy settings lately? – 01/28/21
January 28, was Data Privacy day. This is the one day a year that we are reminded how valuable our data is. We should protect it like we protect our money. However, account providers regularly change their privacy policies, settings and terms and conditions which makes that challenging.
When account providers make those types of changes, they sent out a notification email or we see a popup appear when we login to our account. Both are annoying and both require us to acknowledge we are aware of the changes before we can use their service. When we receive that notification we usually don’t have time to wade through the legalese to find the changes, we just click accept and move on with our day.
Data Privacy Day is a great time to take a pause and check those changes. Check both the terms and conditions and privacy settings. That way you know what data the account provider has access to and how much control you have over it. While this is a pain, taking a few minutes to check things now can save a lot of heartache later. In addition, if you are not comfortable with the changes it gives you an opportunity to let the account provider know and if necessary find a new service.
Keep your devices updated with the latest security patches – 01/21/21
With criminals constantly coming up with new ways to hack into our systems, keeping your devices updated with the latest security patches is more important than ever. When you are on campus keeping your workstation up to date and secure is easy. Shut down your machine at the end of the day Friday and start it up Monday morning. However once you are working from home and your computer is always on keeping your machine updated isn’t so straight forward.
If you are remoting in to an MRU workstation you can’t shut it down. Instead, logout of the workstation and disconnect from GlobalProtect at the end of each work day. The updates are downloaded in the background as you work. Once you log out, your workstation is automatically restarted to install them.
If you have an MRU laptop assigned to you, it is setup to automatically download updates as you work. Once the updates are downloaded you are prompted to restart your machine to install them. As long as you don’t ignore the prompts, you are good to go. If you choose to ignore them and call the Service Desk for support, you won’t be helped until you restart your machine.
If you are using your personal computer, make sure you have automatic updates enabled on Windows/Mac OS and all your applications. From the Windows Start menu, select Settings>Updates and security to check your Windows update settings. On a Mac, select System Preferences>Software Update and click the Automatic Updates checkbox. Just like MRU laptops, updates are downloaded in the background and you are asked to restart your machine to install them.
Once you know what to do, installing your security patches is pretty easy. While it can be annoying, it is well worth your time. With a little bit of effort you make it exponentially more difficult for attackers to compromise your data and mess with your life.
Keeping voicemail safe from breaches – 01/05/21

Happy New Year!! Another year, another security concern. This time it isn’t your email, your workstation or your smart phone. This time it is your voicemail. Hackers are taking over voicemail accounts and using them to impersonate people, make thousands in long distance calls and by-pass two factor authentication. Not only does this cost organizations but it is also embarrassing and can lead to network compromise and data loss.
To prevent this, secure your voicemail just as you would your workstation. Use UNIQUE passwords/PINs at least 8 characters long. Remember you aren’t limited to just the 6 characters we are used to using. You can use up to 64 if you wish. Also, make sure your voicemail password/PIN is not a numeric version of any of your other passwords, your age, your birthday, your pets name or any other personal information.
Lastly keep your voicemail password/PIN secret. That means do not share it with colleagues nor leave it on a post-it on your phone. Once someone has your password/PIN, they can forward calls, change your greeting, make long distance calls, pretend to be you and generally cause problems while making you the fall guy. Even if they don’t have malicious intent, once someone gets ahold of your password/PIN they may not be as careful with it as you are.
If you are away on vacation and need someone else to cover for you, record a vacation message directing people to call your substitute directly. You can have calls forwarded automatically, but if no one answers a message is left on the voicemail that received the call, not the one that the call was forwarded to. If neither of these solutions will work for you contact the IT Service Desk, they will find one that does not involve the sharing of passwords/PINs.
Is the etransfer notice from MRU malicious or legit? – 12/07/20
This past year, Student Fees began issuing refunds through Interac e-transfers. Although students are notified in advance that a refund is coming, there is still some confusion about the legitimacy of these emails.
A sure fire way to ensure the refund is legitimate is to login to MyMRU and check your account balance. If you have been issued a refund, the amount will be posted there. If it matches the amount in the notification email then you know the e-transfer is legitimate.
If you are still not sure, you can email Student Fees at studentfees@mtroyal.ca and ask them if they sent you an e-transfer.
Password Managers, myths and misconceptions – 12/09/20
Now a days it seems like no matter what you do online, you need to create an account. With all those accounts comes the impossible task of remembering all those passwords. It is understandable why many of you (71%), are reusing password across multiple accounts. Unfortunately, password reuse leaves you vulnerable to credential stuffing.
So how do you create dozens and dozens of strong, unique passwords? The answer is use a password manager. A password manager generates, stores and autofills passwords for you. It saves you time as well as your sanity while ensuring your accounts are secured. It is a win, win. So much so that 73% of security experts use one.
Unfortunately, there are a lot of misconceptions around password managers. As a result, only 24% of non security experts choose to use one. Most of the reluctance is around convenience and security. It is generally thought that password mangers are too cumbersome to bother using and they aren’t secure anyway. Both of those assumptions are incorrect. I am going to set the record straight by debunking common password manager myths.
Myth #1 – Password managers aren’t secure
While no application is 100% secure, the odds that a password manager would be hacked is less than the odds that the sticky on your monitor will be read. Password managers store passwords in an encrypted file that can only be unencrypted by the password used to login to the password manager. If a hacker gains access to your password file but doesn’t have the password for it, all they will see is a jumbled mess. So unless you reuse the password for your password manager or use a weak password, the rest of your passwords should remain secure.
Myth #3 – Letting my browser save my passwords is just as secure as a password manager
Unless your browser requires you to enter a separate password to access passwords it stores then no, it is not secure. Your passwords stored in your browser are linked to your browser account. That allows you to take them with you from one device to the next. However if you forget to logout of your browser on a shared device, the next person who uses the device will have access to them. It is frightening the number of laptops that have been returned to the library displaying the last user’s passwords.
Myth #4 – Password managers are inconvenient to use
Every password manager has different features and works a little bit differently. If you find one that doesn’t work for you, try another. Almost all of them allow you to try them out for free for 30 days. Once you find one that you like, you will find that it actually saves you time and effort. You don’t have to wrack your brain to come up with strong, unique passwords anymore, the password manager does that for you. You don’t have to enter in your login credentials anymore, most password managers do that for you. You don’t have to sort through stickies to find the right password, the password manager finds it for you. You get the idea, all the annoying things you used to have to do to login to an account, website or application are done by the password manager. It makes life so much easier.
So there you have it. Password managers are secure, safer than using your browser and convenient. Most of all they make it easy for you to have a different password for every account. Now you just have to decide which one to use. KeePass is free to download and it is on all MRU workstations. However there are other web based tools that are a bit easier to sync between your devices. You can find a list of them on PC Mag’s website. I suggest that you take a look at them, compare features and pricing and then choose one or two to try for 30 days.
Unfortunately, IT Services does not reimburse you if you purchase a password manager. However, most are very affordable and can be used by your whole family.
