Data backups are no longer optional – 07/30/18
With everything going digital, our lives have gotten easier but it has also made us more vulnerable. Losing precious memories or a month of hard work used to require a hungry pet or a natural disaster. Now all it takes is clicking on an email link or visiting the wrong website. While this has long been a hazard, the surge in ransomware has increased the chance of losing precious data exponentially.
With this increase in risk, backing up data to prevent a catastrophic loss has gone from being just a good idea to being critical. Single data backups reduce the peril significantly, but they really aren’t sufficient. This is especially true if the backup is stored on a portable drive that stays connected to your machine. When the computer is compromised anything else that is connected to it, including the portable drive, is also exposed.
Thankfully you don’t have to worry about data backups on your Mount Royal workstation as long as you save your data on the H: drive, J: drive or Google Drive. IT Services backs up multiple copies of files on those servers in multiple locations for you as does Google. If you are saving files on the C: drive or the Desktop though, they are at risk as files stored there are not backed up. This is why IT Services is constantly telling people to stop storing files on the C: drive and the Desktop. We aren’t trying to make your life more difficult, we are trying to protect you from data loss.
What about your machine at home? What is the best practice when it comes to backing up your own data? Most professionals will suggest the 3-2-1 strategy. Have three copies of your data, on two different unconnected devices, one of which is off site.
- Your first copy is your working copy. It sits on your computer and is what you mess with every day.
- Your second copy is stored on a separate device. You can use a USB key, a portable drive or another computer. It is connected to the internet or your computer only long enough to copy your data and is then disconnected. Ideally you would do this daily, but you can chance it and only do this weekly.
- Your third copy is stored off site. This ensures that if your home or office is flooded, burns down to the ground or is destroyed in some other manner; your data is still safe. Again, this should be a device or service that you connect to upload your data and then disconnect from. You can use a cloud service or the sneaker net (upload to a portable device that you store in a safety deposit box or other safe location). Ideally you would also do this daily, but a weekly update can be done as well.
Following 3-2-1 will almost guarantee that you can recover from any kind of data loss. However it does take some time and commitment, all you have to do is determine if your data is worth it. Unfortunately, we usually don’t figure that out until its too late.
Harrassed online? Here’s what you do- 07/12/18
If you are on social media, there is a very good chance that at some time you have been attacked by an internet troll. Usually they can be shut down by simply ignoring them and not responding to their attempts to create conflict. However, every once in a while the troll continues to harass and they go from being annoying to being abusive. Thankfully, it is possible to have these people brought up on criminal charges. However, you do need to do some homework. The process is not an easy one. Here are a few tips to get you going:
- Get screen shots.
You never know when a troll is going to cross the line from annoying to abusive, so any harassing posts should be captured in a screen shot. Trolls can delete posts and cancel accounts when they are being investigated. You cannot rely on them being archived. A screen shot preserves the evidence for future prosecution. - Print out your screen shots.
Technology fails, always have a paper backup. - Record dates and times of harassing.
You need to create a chronological record of the harassment. If authorities see it escalating over time, they will be more likely to intervene. - Know the terms and conditions as well as the rights and responsibilities of the social media site you are using.
Be aware of what can and can’t be reported. - Report the bullying to your internet and mobile service providers as well as the social media site.
Give them your screen shots and record of harassment. - Block the troll from your account.
Most social media sites allow you to block messages or posts from specific individuals. If the troll creates another account and continues to harass, this further supports your case. - Report the harassment to the police.
If you continue to be harassed even after you have not responded to their taunts and have blocked them from accounts, you have grounds to report the harassment to the police.
To get help with the documenting process and gain support, visit HeartMob a non profit organization dedicated to ending online harassment. Their website is full of resources including a twitter bot that replies to harassers with a disincentive.
The password to your internet connected device is on the web – 07/04/18
Have a thermostat, doorbell or baby monitor that connects to the internet? How about a router? Have you changed the default password that came with the device? No? Well, you might want to get right on that. Why? Well, the default passwords of most devices can be found on the internet. Yup, that is correct. You can do a simple search of the make and model of your device and in most cases get its default password.
This is very handy when you are setting up your device for the first time or you have to perform a factory reset. It is also very handy for hackers who count on consumers leaving the default password as is. Once criminals have the password, they can easily gain control of the device. Numerous instances of baby monitors scanning rooms on their own and devices being turned into bots for deny of service attacks have been documented.
This is just another gentle reminder to change your default password and keep the device firmware up to date on anything that connects to the internet. Want to learn more about internet connected devices? Check out this blog post.
Adidas is not giving away free shoes – 06/19/18
From the Too Good to Be True file, comes the Adidas anniversary giveaway. Messages are currently circulating in WhatsApp promising a free pair of Adidas shoes in celebration of their anniversary. Initially messages referred to a 93rd anniversary, however the hacker decided to do some basic math and more recent messages correctly refer to a 69th anniversary.
You might be asking, why on earth would someone fall for this? Well once the scammers sorted out their math, they were clever enough to spoof the official Adidas site. The fake URL is exactly like the legitimate one with only the i replaced with a vertical line with no dot. This is an easy thing to miss when one is being tempted with free footwear.
In addition the scam is quite sophisticated. They don’t just come right out and say, give me your personal information and I will give you free shoes. Instead, they give the whole thing a legitimate feel by making the victim qualify first by answering a short survey and requiring them to share the offer with their WhatsApp contacts (just for the record, there is no way for them to determine if you have shared a message or not). Once you qualify, you are told you can claim your shoes for a dollar. Of course as payment is now required (but it’s only a dollar, so it’s nearly free), you are sent to a webpage that collects your payment card information. Having jumped through multiple hoops to claim your prize, you now feel like you have earned the free shoes and all thoughts that this are a scam are gone from your mind.
That is until you see the confirmation of payment web page that includes a line in the footer saying you will be charged $50 per month if you don’t cancel your subscription in seven days. Of course they now have your payment card information and will charge you what they want for as long as they want until you cancel the card. Even worse if you fail to read the footer, they will have access to your card until you notice the charges.
Anytime someone is giving something away, assume it is a scam. If you are tempted by the sparkly giveaway being dangled in front of you, visit the company’s website using a bookmark or search engine result. If they are giving something away, it will be advertised on their official site. Remember if it is too good to be true, it probably is.
Is that app really as popular as it seems? – 06/15/18

Cyber criminals are getting wise. They have noticed that if an Android app has lots of downloads listed, the odds are pretty good that others will download it as well. They are using this phenomenon to trick people into downloading their malicious apps.
How are they doing it? When you browse the app store, the only information that you see is the app name, app icon and the developer name. Creative criminals are taking advantage of this by entering their developer names as 100 Million Downloads, Installs 1,000,000,000 + or simply 5,000,000,000.
Criminals aren’t stopping the deception there. They are also using Verified Application or Legit Application as their developer names. Never mind that Google Play doesn’t have a developer account verification service, it looks good anyway.
This is just a reminder that when you are looking for apps to download stick to Google Play and read reviews carefully. Stay away from apps that use deceptive tactics, have few reviews or few downloads. Happy and safe downloading!
Some Google Groups are leaking data – 06/05/18
Have you checked the settings on your Google Group lately? By default when you create a group, only group members can post and view messages and people must ask to join the group. However, researchers have discovered that thousands of Google groups have their permissions set to allow the general public to view the group posts. This would not be an issue if the people posting information to the Google Group understood that their posts could be viewed by the public. However, sensitive and private information has been found within these group posts suggesting that they really have no idea.
If you are the owner of a Google Group, please take a moment to check your permissions. To check permissions:
- Open the Google Group.
- In the title bar of the Google Group, click Manage. The left menu changes.
- In the left menu, click Permissions. A list of permissions appears.
- Click to select each permission type and review its settings.
Please note that if you have selected All organization members, to View topics or Post anyone with an @mtroyal.ca email address may do so. This includes students, staff and faculty. If you have selected All members of the group, users must actually join the group to be able to post or view emails/topics.
If you wish to email/post to a Google Group, check the settings of the group to see who can see the messages you send. To check the settings:
- Open the Google Group.
- In the title bar of the Google Group, click About.
- Scroll down to find the Access section. The posting and viewing permissions of the group are listed here.
If you have questions or concerns about setting permissions, please contact Bernadette Pasteris at bpasteris@mtroyal.ca.
Hackers using calendar events to deliver malicious links – 05/23/18
Hackers have discovered a new way to deliver malicious links, through your Google calendar. How? Simply by creating a calendar event and inviting you.
By default when you are invited to a Google calendar event, the event appears in your calendar whether you have responded to an invite or not. The sneaky hackers know that if you receive an email with an invite from someone you don’t recognize, the odds are great that you will simple delete it or ignore it. So, they create an event with a vague description and include a link to the meeting agenda but choose to not email the guests.
What the hackers hope is days or weeks later when you receive a meeting notification or see the event sitting in your calendar, you will think you have forgotten about a meeting and will open up the event and click on the link to view the agenda. I know what you are thinking, I wouldn’t fall for that because I would check the meeting owner’s email. Ideally that is exactly what you would do, however when humans think they have messed up they tend to panic and click.
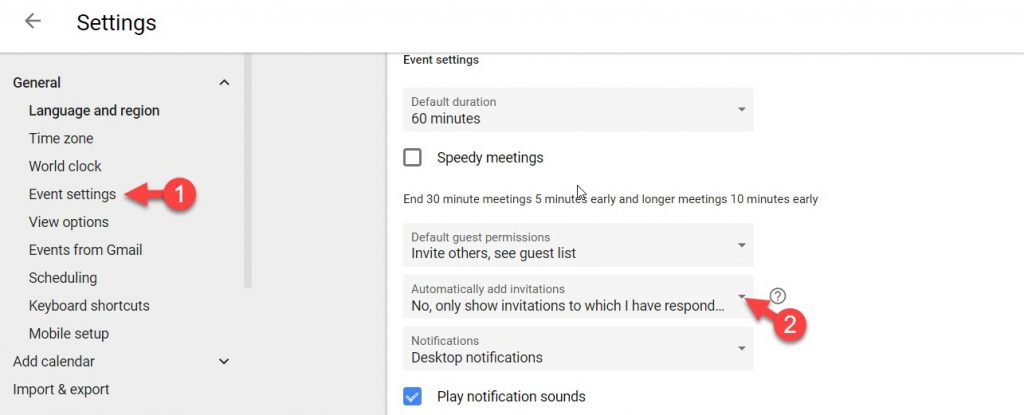
How do you protect yourself from the panic and click? You can change your event settings on your Google calendar. Go to Settings and select Event Settings. In the Automatically add invitations section, select No, only show invitations to which I have responded. This prevents events from being added to your calendar without an email invite so you can’t be ambushed.
Watch out for the Facebook video scam – 05/15/18
Facebook users around the world are being taken in by the latest video scam. They are receiving Messenger messages containing a video link. When they click on the link, they are taken to a fake Youtube web page and asked to download a browser extension so the video can be viewed. Of course when they do, they load malware onto their machine that harvests their data and then sends out the same message to all their Facebook friends.
This newest scam is just one of several that use Messenger to deliver malicious links. These links as well as those in text messages or other messaging apps should be treated the same as links in email:
- If it is from someone you know, call the sender to make sure they sent it before you click on it.
- If it is from an organization, visit their website directly to get the information.
- If you don’t recognize the person or organization, delete the message.
Twitter asking users to change their passwords – 05/04/18
Why is twitter asking all its users to change their passwords? They discovered that login credentials were being stored unmasked in an internal log. This means anyone at the company who opened this log could see users’ passwords and usernames. A HUGE no no. The good news is, they have no evidence that suggests any passwords or account information have been stolen. Now this doesn’t mean that some Twitter systems analyst hasn’t taken down your credentials to use at a later date, it just means they don’t think it has happened.
While this is a huge embarrassment for Twitter, for most of its users it will likely be nothing more than a lesson on the importance of having two step verification enabled. Those lucky ones who reuse passwords will also be reminded why it is better not to as they scramble to remember all the accounts that use the newly exposed password.
Help! I think I have a virus! – 04/24/18
Is your computer acting weird? Is it suddenly working really slowly? Are pop-ups all over your screen? Are folders graying out and can’t be opened? Are files suddenly unavailable or can’t be found? Is your mouse moving on it’s own? Has the text become unreadable? Do you have a virus alert? If you are experiencing any of these, you could have a virus or malware on your computer.
If you think you have malware on your machine, do not turn off your machine, some types of malware load on start up. Do not run a virus scan, some types of malware corrupt anti-virus programs. Do not try to fix the problem yourself. Do not panic, help is available. So what do you do?
- Don’t touch anything. Many types of malware are loaded by clicking anywhere on a pop up window. If you don’t click, you may be able to prevent an infection.
- Disconnect from the Internet. On your workstation, unplug the network cable. On your mobile device, disconnect from wifi.
- Call the IT Service Desk.
Not sure what a network cable looks like? It looks like a phone cable, but comes out of the back of your computer. It can be red, white, black, blue, gray or yellow. Still not sure? Here is a photo for you:

Worried about getting into trouble and you don’t want to call the Service Desk? Please don’t be. IT Services has service in the name for a reason. We are here to help you. We know you are human. We know people make mistakes. We like to get your calls.
