Scammers getting really clever with MasterClass phishing emails – 04/28/22
Over the last few weeks phishing emails with fake invoices from MasterClass have been popping up in inboxes all over campus. I have been posting them to the Phish Bowl, but you can see an example here.
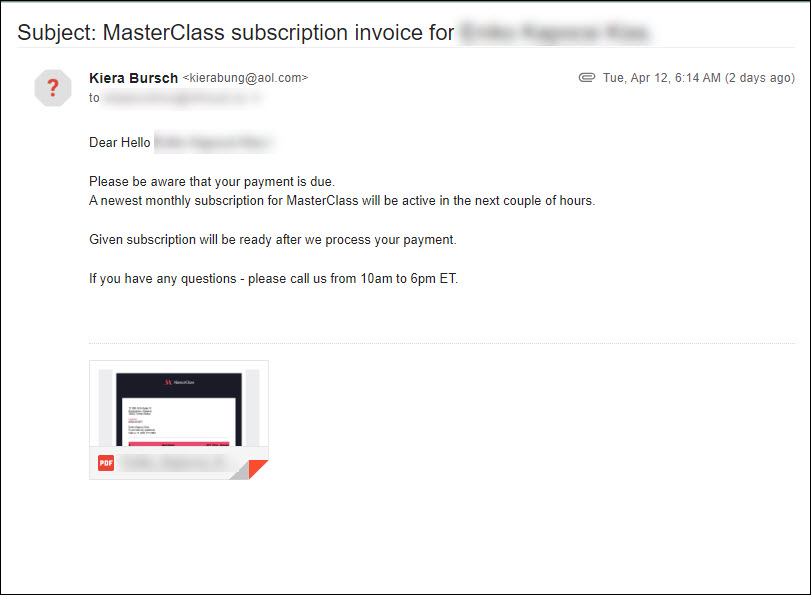
Most of you will have probably noticed that the attachment itself isn’t malicious. Instead the scammers are hoping you will call them and ask for a refund. If you do, there a number of scams they can pull.
The simplest is asking for your credit card number so they can issue a fund to the correct card. They assure you that the refund will appear on your credit card statement within 48 hours. Of course, no such refund is made. Instead they go on a 48 hour shopping spree on your dime.
The more sophisticated scams take you through a “refund” process where they deposit funds directly into your bank account. They then show you a fake screen shot that indicates they accidentally refunded you too much money and then ask you to e-transfer the excess funds. When you point out that the refund doesn’t appear on your online bank account statement, they say that it will take 24 hours to do so. If you ask to wait until it shows up, they say if they don’t fix the error now, they will get fired. They can be very persuasive. Sometimes they will cycle you through several “supervisors” and “mangers” to convince you that the excess funds must be returned immediately.
Of course, they never charged your card in the first place, nor will you ever see the money refunded to your bank account. Instead you will have handed over thousands of dollars to the scammers.
Fortunately, it doesn’t appear as though there have been many people on campus who have fallen for this scam. As a result, the scammers have upped their game. We are now seeing the following email arrive in inboxes shortly after the one I previously shared.

You see people are getting smart. The scammers are realizing that an email with an attachment maybe isn’t the best way to get people to call them. Instead, they have set up a remote support session. The diabolical part, is this email comes from a legitimate service, Zoho Assist. So malware filters won’t think anything is amiss. Your only clue is the little note at the bottom that mentions the email comes from a generic email account instead of MasterClass itself. This is something they hope won’t notice as the previous email has already got you thinking about that MasterClass subscription you didn’t sign up for.
I have to admit, this is very very clever. The good news is, if you take your time and look closely you can identify the scam and delete the email before things ever get to the excess refund stage.
New Google feature looks like phishing – 03/25/2021
Google has launched a new feature for Google meet. Any time there are more than two people in a meeting, you will automatically receive an attendance list attached to an email. This email has the name of the meeting in the subject line. This works great when you have created the meeting in your calendar and given it a name. The email makes sense and it looks legit.
However, if you create the meeting through the Google chat or the Meet button in the Gmail window, there is no way to give the meeting a name, so Google does that for you. As a result you end up with an email subject line that includes a bunch of random capital letters in quotes.
At first glance this email looks really, really phishy. You have this weird looking subject, an attachment and you didn’t request an attendance report. But if you take a closer look at the sender’s email address, you realize that this is in fact coming from Google and it is a legitimate email.
If you receive an email like this and you are uncertain what to do with it, then please report it. However, hopefully now that you have a little more information you won’t feel so quite uncomfortable when that odd email shows up unannounced from Google.
AHS offer of $100 for getting vaccinated is fake – 03/11/22
There is a particularly devious smishing attack currently being circulated. Check it out.

This one is extremely well done for several reasons. First, the chances are high that whoever receives this text is vaccinated. Second, the Alberta Government was indeed sending out $100 debit cards to those who got vaccinated last fall. Third, the link appears to go to Alberta Health Services. Lastly, we have all seen the sign-in partner prompt when dealing with the CRA or when receiving an e-transfer.
So what are the red flags? If you hover over the link, it will display a different URL than what you see in the link. In addition, the Alberta Government’s program was to distribute debit cards, not deposit money directly into your bank account. Also, that program ended in the fall and there is no new program to encourage you to get your booster.
No one I know has clicked the link to see what will happen. However, I can make a pretty good guess from the way the information is presented. Likely, the link takes you to a page that asks for your banking credentials.
As much as we could all use an extra $100 right now, this one falls into the “Too good to be true”, category.
Shared/delegated email accounts and MFA – 01/12/22
Google has started sending reminders to those who haven’t yet enabled multi-factor authentication (MFA) on their Mount Royal email account. For those with a single email account the process is easy. However if you use a delegated, google group or shared email account there may be some confusion. Do you have to enable MFA or not? Well that depends on what type of account you have and how you use it.
Delegated accounts allow you to access emails from your own Mount Royal email account. Neither you nor anyone else that uses the account ever logs into it. If you click on your profile pic in Gmail and see the account listed with delegated next to it, it is a delegated account.

Even though you may have received a notification to enable MFA on that account, you don’t have to. We know that is confusing so we are working on identifying all the delegated accounts so hopefully you will not get notifications in the future.
Shared accounts require you to login with a separate username and password to access emails. The username and password are often shared by several people. They are usually set up because the generic account needs a Youtube channel or to set up its own google forms. If you have a shared account, please do not ignore the MFA notifications and contact the IT Service Desk to find out if MFA is required. This will be determined on a case by case basis depending on how the account is used.
Google groups aren’t actually email accounts so you don’t see them listed with your delegated accounts. They are mail lists that you subscribe to or create. They are often set up to send emails directly to your inbox, however you can also access the emails from the Google Group app. As Google groups are part of the Google Workspace, you don’t need to MFA them separately. They are protected when you enable MFA on your MRU email account.
For more information on enabling MFA visit the Multi-factor Authentication web page.
No that is not a malicious pop up – 01/11/22
In preparation for the implementation of mandatory MFA on February 28, 2022, a new pop-up will appear when you login to Google if MFA is not turned on. It looks like this.

If you click Do this later, you can access your account and enable MFA at a later date. However, we do encourage you to click Enroll instead. The sooner you enable it , the sooner the annoying pop-up goes away. After February 28, 2022 anyone who does not have MFA turned on will have to contact the IT Service Desk to get access to their Mount Royal email account, Google Drive or any other Google Workspace apps.
The Cyber Guys are coming! – 01/11/22

January 2022 is here! As promised, next week we will be releasing the first Cyber Guys video. This short video is super fun. As a reward for watching you will earn a contest entry code. Have a giggle, get a cybersafety reminder and earn codes. What could be better? Log into the Security Education Platform and check your My Assignments list to find the video link.
The use and care of your MRU email address – 12/07/212
We are regularly notified that Mount Royal email addresses have been involved in a data breach through Have I been pwned. When we receive that notification, we are told what account provider was affected and which email addresses were involved. This allows us to contact those who had their accounts compromised and ask them to change their passwords.
With multi-factor authentication enabled, this is less of an issue. Even if a password is stolen, the attacker will not be able to get into a MRU email account without the second factor. However it is still important that compromised passwords are changed, especially if the same one is being used for multiple accounts. So we are still receiving data breach notifications.
Usually the data breaches are for work related services. However, once in while we are notified that a gaming site, dating website or a site with adult content has been breached. If you have used your Mount Royal email address to access that site, we will be notified. It is awkward for everyone when that happens.
Please keep your private life private and only use your MRU email address for work purposes. We don’t need to know what you do for hobbies, how you spend your time outside of work or where you shop. Save us all the embarrassment and use another email address for your personal pursuits. The security team thanks you.
Fake TD texts try to nab your banking credentials – 12/15/21
Look at what showed up on the phone of an MRU community member.

The links in this text do not go to the TD Canada Trust website. The person who received this text does not bank with TD so they knew it was a fake alert right away. However, if you do bank with them and receive this text, the odds are pretty good you will click. The whole alert received thing tends to make people panic. When they panic, they react. Rational thought never has a chance to kick in.
We don’t know for sure what will happen if you click one of the links. However, as it tells you to login, the odds are good that you will be directed to a fake TD login page. When you enter your username and password, the criminals will likely record and store your credentials to either use themselves or sell on the dark web. Either way, they can drain your bank accounts.
This is a reminder that if you receive an email or text from your bank, count to 10. Then call them directly using a phone number that you know is legitimate to ask them if there is a problem with your account. Resist the urge to click, no matter how great it is. Salvation is only a phone call away.
The return of the Cybercafe – 12/15/21
To level the playing field for the Cybersecurity Challenge for those working from home, starting in January 2022, the Cybercafe will return. Once a month I will make myself available from 10:00 am to 2:00 pm virtually for questions, MFA support or to discuss the latest cybersecurity threat. Everyone who stops in will get two contest entry codes, the same ones given out at the Cybersecurity Roadshow. This prevents double dipping, evens things out and gives our working from home folks a chance to catch up.
I am hoping that this will give everyone an equal chance to participate in the challenge and encourage those who may have felt left out to join in. This is an excellent opportunity for your team to catch up and earn some entries. See you all in 2022!
It is survey time! Participate and win a $50 gift certificate! – 12/06/21
It is that time of the year when we look back at last year’s program and figure out what worked, what didn’t and where we can improve. To help us determine if we are on the right track, we need your help. Please take 5 min to complete our survey. To ensure that we are learning about what people are doing on campus rather than what they know they should be doing, the survey is anonymous. You can freely admit your sins safe in the knowledge we will never know who you are. Your honestly will help us determine the direction of our program next year. You can take the survey here.
